Microsoft on Wednesday reported that a user containment feature in Microsoft Defender for Endpoint helped thwart a “huge-scale distant encryption try” produced by Akira ransomware actors focusing on an unknown industrial business in early June 2023.
The tech giant’s risk intelligence group is tracking the operator as Storm-1567.
The attack leveraged products that have been not onboarded to Microsoft Defender for Endpoint as a defense evasion tactic, when also conducting a series of reconnaissance and lateral movement things to do prior to encrypting the units employing a compromised consumer account.
But the new automatic attack disruption capacity meant that the breached accounts are prevented from “accessing endpoints and other resources in the network, restricting attackers’ means to shift laterally irrespective of the account’s Lively Listing state or privilege stage.”

In other words and phrases, the thought is to cut off all inbound and outbound conversation and prohibit human-operated attacks from accessing other equipment in the network.
Redmond also explained its business endpoint security platform disrupted lateral movement tries towards a health-related exploration lab in August 2023, in which the adversary reset the password for a default domain administrator account for observe-on actions.
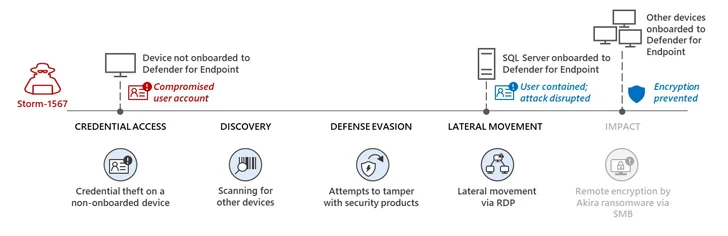
“Extremely privileged person accounts are arguably the most important belongings for attackers,” Microsoft stated. “Compromised area admin-amount accounts in environments that use conventional solutions deliver attackers with accessibility to Lively Listing and could subvert classic security mechanisms.”
“Identifying and containing these compromised consumer accounts, for that reason, helps prevent attacks from progressing, even if attackers acquire first obtain.”
Located this report fascinating? Observe us on Twitter and LinkedIn to read a lot more special articles we put up.
Some parts of this article are sourced from:
thehackernews.com

 Researchers Uncover Malware Posing as WordPress Caching Plugin
Researchers Uncover Malware Posing as WordPress Caching Plugin