Info stealing malware are actively having edge of an undocumented Google OAuth endpoint named MultiLogin to hijack person periods and make it possible for steady entry to Google products and services even just after a password reset.
In accordance to CloudSEK, the critical exploit facilitates session persistence and cookie generation, enabling risk actors to sustain access to a valid session in an unauthorized way.
The procedure was initial discovered by a risk actor named PRISMA on October 20, 2023, on their Telegram channel. It has because been incorporated into different malware-as-a-company (MaaS) stealer family members, these as Lumma, Rhadamanthys, Stealc, Meduza, RisePro, and WhiteSnake.

The MultiLogin authentication endpoint is principally designed for synchronizing Google accounts across products and services when people sign in to their accounts in the Chrome web browser (i.e., profiles).
A reverse engineering of the Lumma Stealer code has uncovered that the technique targets the “Chrome’s token_assistance table of WebData to extract tokens and account IDs of chrome profiles logged in,” security researcher Pavan Karthick M reported. “This desk has two very important columns: provider (GAIA ID) and encrypted_token.”
This token:GAIA ID pair is then blended with the MultiLogin endpoint to regenerate Google authentication cookies.
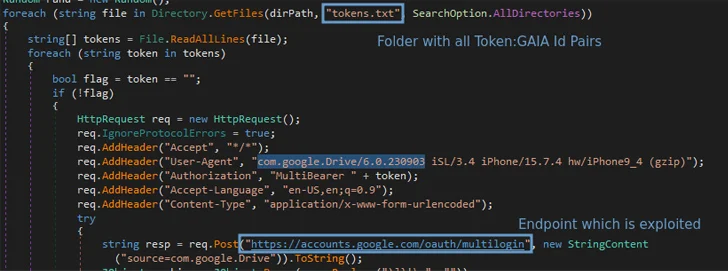
Karthick told The Hacker Information that 3 unique token-cookie era scenarios were examined –
- When the person is logged in with the browser, in which circumstance the token can be used any quantity of occasions.
- When the consumer alterations the password but allows Google continue being signed in, in which case the token can only be used when as the token was previously utilized as soon as to let the consumer keep on being signed in.
- If the person signals out of the browser, then the token will be revoked and deleted from the browser’s nearby storage, which will be regenerated upon logging in yet again.
When reached for comment, Google acknowledged the existence of the attack system but mentioned that buyers can revoke the stolen sessions by logging out of the impacted browser.
“Google is informed of the latest reports of a malware spouse and children stealing session tokens,” the firm told The Hacker Information. “Assaults involving malware that steal cookies and tokens are not new we routinely enhance our defenses from these tactics and to secure buyers who fall sufferer to malware. In this occasion, Google has taken motion to safe any compromised accounts detected.”

“Nevertheless, it can be vital to be aware a false impression in studies that suggests stolen tokens and cookies can not be revoked by the user,” it more additional. “This is incorrect, as stolen periods can be invalidated by only signing out of the afflicted browser, or remotely revoked by way of the user’s devices web page. We will continue on to keep track of the condition and present updates as needed.”
The business further more suggested buyers switch on Enhanced Risk-free Browsing in Chrome to defend against phishing and malware downloads.
“It’s advised to transform passwords so the risk actors wouldn’t make use of password reset auth flows to restore passwords,” Karthick claimed. “Also, users really should be advised to keep track of their account activity for suspicious sessions which are from IPs and locations which they really don’t understand.”
“Google’s clarification is an significant facet of person security,” said Hudson Rock co-founder and chief technology officer, Alon Gal, who formerly disclosed facts of the exploit late very last yr.
“However, the incident sheds mild on a innovative exploit that might challenge the regular techniques of securing accounts. Whilst Google’s actions are useful, this predicament highlights the need to have for a lot more state-of-the-art security methods to counter evolving cyber threats these types of as in the circumstance of infostealers which are immensely well-liked among cybercriminals these days.”
(The tale was up-to-date right after publication to include things like more feedback from CloudSEK and Alon Gal.)
Located this post interesting? Stick to us on Twitter and LinkedIn to read extra unique content we submit.
Some parts of this article are sourced from:
thehackernews.com


 5 Ways to Reduce SaaS Security Risks
5 Ways to Reduce SaaS Security Risks