A new attack marketing campaign dubbed CLOUD#REVERSER has been observed leveraging authentic cloud storage products and services like Google Push and Dropbox to phase destructive payloads.
“The VBScript and PowerShell scripts in the CLOUD#REVERSER inherently involves command-and-management-like activities by utilizing Google Generate and Dropbox as staging platforms to deal with file uploads and downloads,” Securonix scientists Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a report shared with The Hacker News.
“The scripts are made to fetch documents that match precise designs, suggesting they are ready for instructions or scripts put in Google Travel or Dropbox.”
The setting up point of the attack chain is a phishing email bearing a ZIP archive file, which contains an executable that masquerades as a Microsoft Excel file.

In an exciting twist, the filename helps make use of the concealed correct-to-still left override (RLO) Unicode character (U+202E) to reverse the purchase of the characters that appear just after that character in the string.
As a end result, the filename “RFQ-101432620247fl*U+202E*xslx.exe” is exhibited to the victim as “RFQ-101432620247flexe.xlsx,” consequently deceiving them into considering that they are opening an Excel document.
The executable is intended to drop a overall of 8 payloads, like a decoy Excel file (“20240416.xlsx”) and a closely obfuscated Visible Essential (VB) Script (“3156.vbs”) that is accountable for displaying the XLSX file to the consumer to keep the ruse and launch two other scripts named “i4703.vbs” and “i6050.vbs.”
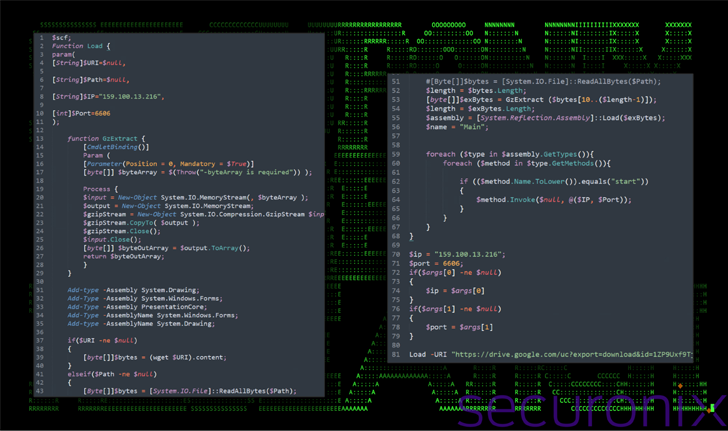
The two scripts are utilised to set up persistence on the Windows host by signifies of a scheduled process by masquerading them as a Google Chrome browser update undertaking to steer clear of boosting pink flags. That stated, the scheduled duties are orchestrated to operate two exceptional VB scripts referred to as “97468.tmp” and “68904.tmp” every minute.
Each and every of these scripts, in switch, is employed to run two different PowerShell scripts “Tmp912.tmp” and “Tmp703.tmp,” which are employed to join to an actor-managed Dropbox and Google Drive account and down load two much more PowerShell scripts referred to as “tmpdbx.ps1” and “zz.ps1”
The VB scripts are then configured to operate the newly downloaded PowerShell scripts and fetch far more information from the cloud services, which include binaries that could be executed relying on the method guidelines.
“The late-stage PowerShell script zz.ps1 has functionality to download files from Google Push based mostly on certain standards and help you save them to a specified route on the community procedure inside of the ProgramData directory,” the researchers claimed.
The fact that the two the PowerShell scripts are downloaded on-the-fly implies they could be modified by the danger actors at will to specify the documents that can be downloaded and executed on the compromised host.

Also downloaded by means of 68904.tmp is one more PowerShell script that’s capable of downloading a compressed binary and operating it specifically from memory in order to retain network connection to the attacker’s command-and-manage (C2) server.
The progress is after once more a signal that menace actors are significantly misusing respectable solutions to their edge and fly less than the radar.
“This technique follows a prevalent thread wherever risk actors handle to infect and persist on to compromised techniques whilst keeping to mix into normal history network sounds,” the scientists said.
“By embedding malicious scripts in just seemingly innocuous cloud platforms, the malware not only assures sustained obtain to specific environments but also utilizes these platforms as conduits for info exfiltration and command execution.”
Located this write-up intriguing? Comply with us on Twitter and LinkedIn to read a lot more special articles we article.
Some parts of this article are sourced from:
thehackernews.com

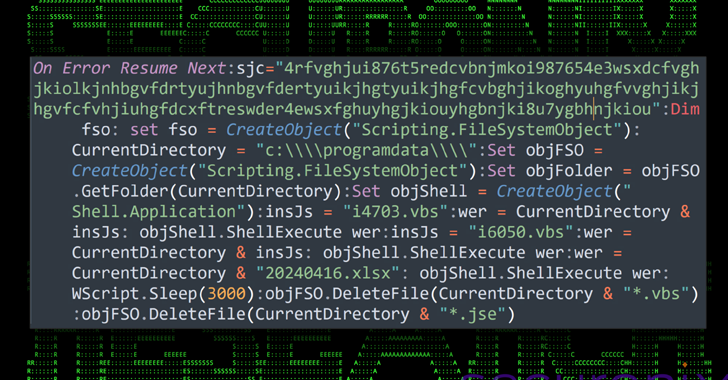
 SolarMarker Malware Evolves to Resist Takedown Attempts with Multi-Tiered Infrastructure
SolarMarker Malware Evolves to Resist Takedown Attempts with Multi-Tiered Infrastructure