Threat actors are likely employing a tool designated for red teaming exercises to serve malware, according to new findings from Cisco Talos.
The program in question is a payload generation framework called MacroPack, which is used to generate Office documents, Visual Basic scripts, Windows shortcuts, and other formats for penetration testing and social engineering assessments. It was developed by French developer Emeric Nasi.

The cybersecurity company said it found artifacts uploaded to VirusTotal from China, Pakistan, Russia, and the U.S. that were all generated by MacroPack and used to deliver various payloads such as Havoc, Brute Ratel, and a new variant of PhantomCore, a remote access trojan (RAT) attributed to a hacktivist group named Head Mare.
“A common feature in all the malicious documents we dissected that caught our attention is the existence of four non-malicious VBA subroutines,” Talos researcher Vanja Svajcer said.
“These subroutines appeared in all the samples and were not obfuscated. They also had never been used by any other malicious subroutines or anywhere else in any documents.”
An important aspect to note here is that the lure themes spanning these documents are varied, ranging from generic topics that instruct users to enable macros to official-looking documents that appear to come from military organizations. This suggests the involvement of distinct threat actors.
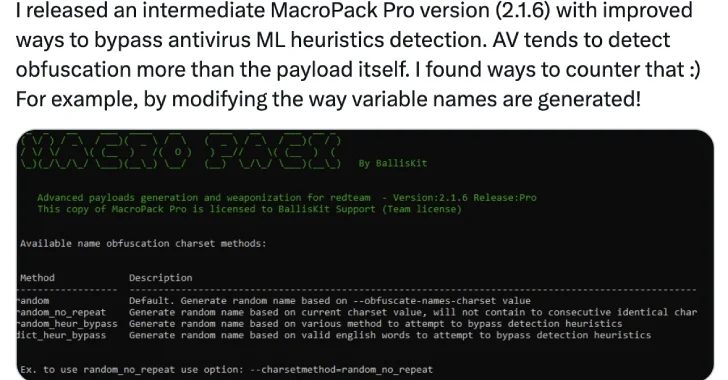
Some of the documents have also been observed taking advantage of advanced features offered as part of MacroPack to bypass anti-malware heuristic detections by concealing the malicious functionality using Markov chains to create seemingly meaningful functions and variable names.

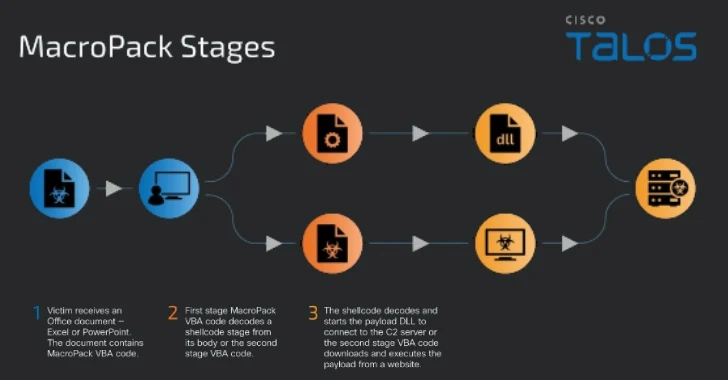
The attack chains, observed between May and July 2024, follow a three-step process that entails sending a booby-trapped Office document containing MacroPack VBA code, which then decodes a next-stage payload to ultimately fetch and execute the final malware.
The development is a sign that threat actors are constantly updating tactics in response to disruptions and taking more sophisticated approaches to code execution.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.
Some parts of this article are sourced from:
thehackernews.com

 New Cross-Platform Malware KTLVdoor Discovered in Attack on Chinese Trading Firm
New Cross-Platform Malware KTLVdoor Discovered in Attack on Chinese Trading Firm