Cybersecurity researchers have uncovered a new set of malicious offers published to the NuGet package manager working with a lesser-recognised approach for malware deployment.
Software package supply chain security firm ReversingLabs described the marketing campaign as coordinated and ongoing because August 1, 2023, whilst linking it to a host of rogue NuGet deals that had been observed providing a distant entry trojan known as SeroXen RAT.
“The danger actors behind it are tenacious in their need to plant malware into the NuGet repository, and to continuously publish new destructive deals,” Karlo Zanki, reverse engineer at ReversingLabs, said in a report shared with The Hacker News.

The names of some of the deals are below –
- Pathoschild.Stardew.Mod.Construct.Config
- KucoinExchange.Net
- Kraken.Exchange
- DiscordsRpc
- SolanaWallet
- Monero
- Modern.Winform.UI
- MinecraftPocket.Server
- IAmRoot
- ZendeskApi.Customer.V2
- Betalgo.Open.AI
- Forge.Open.AI
- Pathoschild.Stardew.Mod.BuildConfig
- CData.NetSuite.Net.Framework
- CData.Salesforce.Net.Framework
- CData.Snowflake.API
These packages, which span a number of versions, imitate well-liked deals and exploit NuGet’s MSBuild integrations function in get to implant malicious code on their victims, a feature termed inline tasks to obtain code execution.
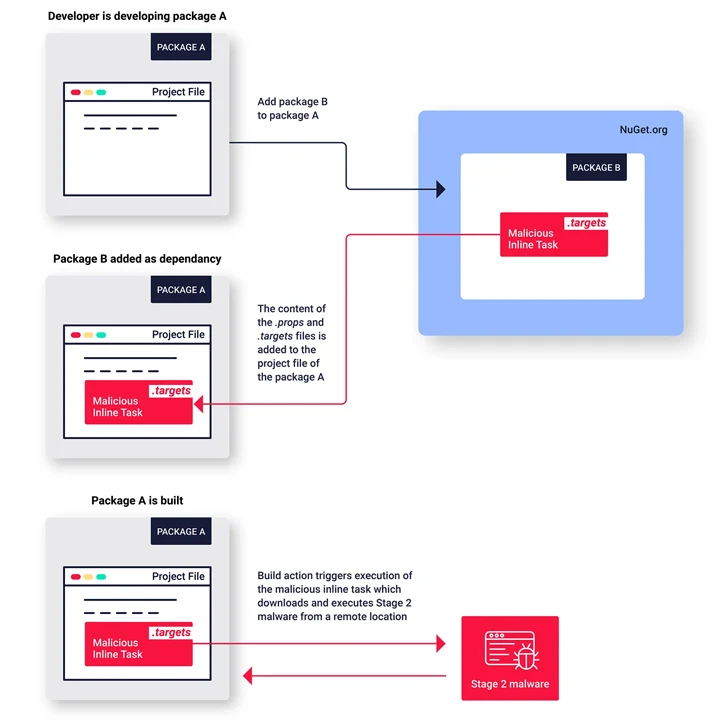
“This is the 1st acknowledged illustration of malware printed to the NuGet repository exploiting this inline duties feature to execute malware,” Zanki claimed.
The now-taken out deals show equivalent features in that the risk actors behind the procedure attempted to conceal the malicious code by producing use of spaces and tabs to transfer it out of look at of the default monitor width.
As earlier disclosed by Phylum, the packages also have artificially inflated downloaded counts to make them show up far more genuine. The ultimate purpose of the decoy packages is to act as a conduit for retrieving a 2nd-stage .NET payload hosted on a throwaway GitHub repository.
“The threat actor guiding this campaign is remaining mindful and shelling out interest to particulars, and is identified to hold this destructive marketing campaign alive and active,” Zanki reported.
Observed this posting intriguing? Observe us on Twitter and LinkedIn to study extra exclusive articles we submit.
Some parts of this article are sourced from:
thehackernews.com

 PentestPad: Platform for Pentest Teams
PentestPad: Platform for Pentest Teams