Chinese-talking buyers have been focused by destructive Google advertisements for restricted messaging apps like Telegram as part of an ongoing malvertising marketing campaign.
“The danger actor is abusing Google advertiser accounts to develop destructive advertisements and pointing them to internet pages the place unsuspecting buyers will download Distant Administration Trojan (RATs) in its place,” Malwarebytes’ Jérôme Segura said in a Thursday report. “These kinds of packages give an attacker entire regulate of a victim’s machine and the capacity to fall supplemental malware.”
It is truly worth noting that the action, codenamed FakeAPP, is a continuation of a prior attack wave that specific Hong Kong buyers searching for messaging applications like WhatsApp and Telegram on research engines in late October 2023.
The latest iteration of the marketing campaign also provides messaging application LINE to the list of messaging apps, redirecting users to bogus websites hosted on Google Docs or Google Websites.

The Google infrastructure is utilized to embed backlinks to other sites under the danger actor’s management in order to produce the destructive installer information that in the end deploy trojans these as PlugX and Gh0st RAT.
Malwarebytes claimed it traced the fraudulent adverts to two advertiser accounts named Interactive Interaction Group Constrained and Ringier Media Nigeria Confined that are based in Nigeria.
“It also seems that the danger actor privileges quantity above top quality by frequently pushing new payloads and infrastructure as command-and-manage,” Segura said.
The enhancement arrives as Trustwave SpiderLabs disclosed a spike in the use of a phishing-as-a-support (PhaaS) system known as Greatness to make authentic-wanting credential harvesting internet pages targeting Microsoft 365 users.
“The package allows for personalizing sender names, email addresses, subjects, messages, attachments, and QR codes, enhancing relevance and engagement,” the firm stated, adding it arrives with anti-detection steps like randomizing headers, encoding, and obfuscation goal to bypass spam filters and security units.
Greatness is available for sale to other legal actors for $120 per month, effectively lowering the barrier to entry and assisting them perform assaults at scale.
Attack chains entail sending phishing email messages bearing destructive HTML attachments that, when opened by the recipients, immediate them to a bogus login webpage that captures the login qualifications entered and exfiltrates the particulars to the menace actor via Telegram.
Other infection sequences have leveraged the attachments to fall malware on the victim’s machine to facilitate information theft.

To boost the probability of good results of the attack, the email messages spoof dependable resources like banking companies and employers and induce a wrong sense of urgency using subjects like “urgent bill payments” or “urgent account verification expected.”
“The range of victims is unknown at this time, but Greatness is commonly made use of and properly-supported, with its have Telegram community furnishing information on how to work the package, together with more suggestions and tricks,” Trustwave mentioned.
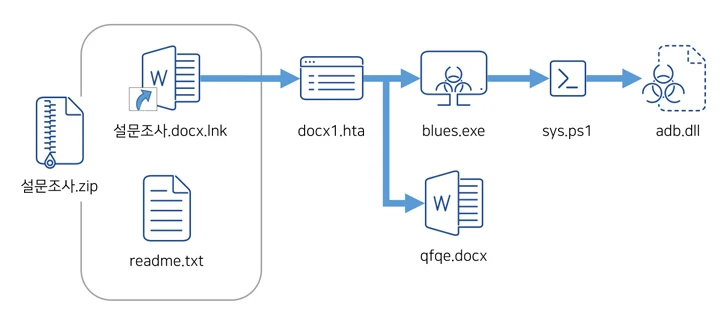
Phishing attacks have also been noticed striking South Korean corporations applying lures that impersonate tech providers like Kakao to distribute AsyncRAT through destructive Windows shortcut (LNK) files.
“Destructive shortcut data files disguised as legit documents are continually staying distributed,” the AhnLab Security Intelligence Middle (ASEC) explained. “End users can mistake the shortcut file for a ordinary doc, as the ‘.LNK’ extension is not visible on the names of the documents.”
Uncovered this short article interesting? Observe us on Twitter and LinkedIn to study more special content we publish.
Some parts of this article are sourced from:
thehackernews.com


 Microsoft Warns of Widening APT29 Espionage Attacks Targeting Global Orgs
Microsoft Warns of Widening APT29 Espionage Attacks Targeting Global Orgs