As get the job done ebbs with the common close-of-year slowdown, now is a fantastic time to review user roles and privileges and eliminate any one who shouldn’t have access as well as trim needless permissions. In addition to preserving some pointless license fees, a thoroughly clean person stock considerably boosts the security of your SaaS programs. From lowering risk to safeguarding from info leakage, in this article is how you can get started the new 12 months with a clean up consumer list.
How Offboarded Buyers Even now Have Obtain to Your Apps
When personnel depart a firm, they cause a series of modifications to backend systems in their wake. To start with, they are removed from the firm’s identity provider (IdP), which kicks off an automated workflow that deactivates their email and eliminates entry to all interior units. When enterprises use an SSO (solitary sign-on), these previous personnel eliminate entry to any on-line properties – which includes SaaS apps – that have to have SSO for login.
On the other hand, that won’t indicate that previous staff have been completely deprovisioned from all the SaaS applications. Enterprises have to manually deactivate or delete users from their SaaS programs for all applications that aren’t linked to the SSO, as perfectly as for any person that has area entry to an application that is connected to the SSO. This issue is significantly acute with substantial-privilege customers. Numerous applications require that they have nearby access in the event that the SSO goes offline.
Any offboarded consumer with accessibility to corporate SaaS applications retains their capacity to login and use the application. That usually means they can down load data, make adjustments, delete information, or even share their login credentials with competitors.
Obtain this Offboarding manual for step-by-move recommendations in offboarding staff members from your SaaS stack
Make Certain to Appropriate-Size Permissions
Overpermissioning any user unnecessarily expands the attack surface and needlessly introduces a greater stage of risk to the application. It really is the user’s permissions that command the stage of accessibility just about every worker has inside of an software. Ought to a consumer account be compromised, the threat actor would have an equivalent level of access as the consumer who was compromised.
A group leader would probably want administrative permissions to increase new end users, open projects, and if not manage usage of the software. Workers making use of the software may well need go through/compose permissions to satisfy their role, when assist personnel may possibly only require browse permissions or the skill to obtain stories.
With the year winding down, it really is a very good time to assessment person permissions and ensure that they are aligned with their purpose. Enterprises ought to put into practice the basic principle of the very least privilege (POLP), to be certain that staff members have the proper level of access to do their job. For apps that include team operation, assign like-people to teams with preset permissions to standardize permission sets. For other applications, it is worthwhile to evaluate person permissions and trim accessibility to only those functionalities that are desired.
Remove Dormant Accounts
Dormant accounts, which are accounts that are unused, commonly tumble into one particular of three categories.
The risk inherent in these accounts is considerable. Admin accounts made use of by numerous users are likely to have simple-to-guess usernames, effortless-to-keep in mind passwords, and nearby accessibility. This is a combination ripe for abuse. Unused personnel accounts could provide obtain to danger actors following a phishing attack, exactly where the worker does not even remember all the apps to which they have obtain. Meanwhile, security groups have no visibility into exterior end users and whether they are nevertheless concerned in the undertaking.
As enterprises move as a result of the holiday year, it behooves them to assessment dormant accounts and just take the important actions to investigate and appraise their risk. When indicated, these accounts really should be disabled or canceled.
Employ Account Sharing Avoidance
When groups use a shared username to decrease license expenses, they unknowingly make an extra security risk. Shared accounts are just about impossible to entirely protected. As staff members be a part of and depart the staff, the amount of consumers who know the account credentials raises. Furthermore, making use of a shared login stops the use of MFA and SSO, two critical instruments applied to secure SaaS programs.
Shared accounts also make it tough to detect threats stemming from an account. The data applied to detect threats is primarily based on regular utilization. Even so, if an account is generally accessed from numerous destinations, it is unlikely to bring about an alert if accessed by a risk actor.
While it isn’t uncomplicated to detect shared accounts, enterprises can put actions in place to prevent and detect account sharing. Demanding MFA or SSO, for example, would make it difficult for customers to share accounts. Security teams can also assessment consumer habits analytics that suggest account sharing. Monitoring IP tackle logins or closely reviewing user actions analytics are two means to detect shared consumer names.
Shelling out the time now to find shared accounts will support hold SaaS apps a lot more protected in the coming calendar year and very long into the potential.
For the comprehensive Offboarding Manual, click right here.
Automating Person Monitoring and Management
Examining software rosters manually and comparing them to the IdP is a wearisome job. So is checking permissions, examining dormant accounts, and looking for signs of account sharing. Introducing a SaaS Security Posture Administration (SSPM) system automates the method.
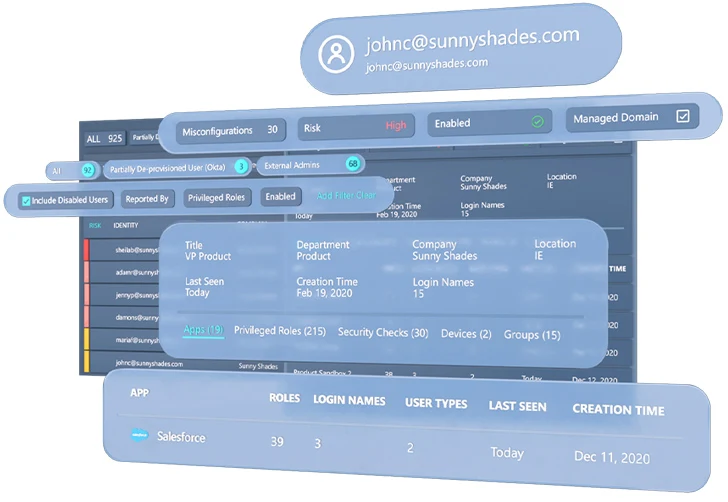 Figure 1: The User Inventory can supply an in-depth glance at just about every SaaS user
Figure 1: The User Inventory can supply an in-depth glance at just about every SaaS user
Making use of an SSPM’s consumer stock, like Adaptive Shield’s, enterprises can swiftly detect user accounts that have not been accessed in excess of a set interval of time, locate exterior customers with significant permission sets, and detect end users who have been taken out from the IdP. SSPMs are also capable of associating end users with units to even more limit risk.
As you get ready for 2024, introducing an SSPM is the most helpful and successful way to watch consumers and know who has entry to what inside your SaaS stack.
Discovered this article interesting? Comply with us on Twitter and LinkedIn to read additional exclusive content we put up.
Some parts of this article are sourced from:
thehackernews.com


 New P2PInfect Botnet MIPS Variant Targeting Routers and IoT Devices
New P2PInfect Botnet MIPS Variant Targeting Routers and IoT Devices