A monetarily enthusiastic danger actor known as Magnet Goblin is quickly adopting a person-day security vulnerabilities into its arsenal in get to opportunistically breach edge equipment and general public-going through expert services and deploy malware on compromised hosts.
“Threat actor team Magnet Goblin’s hallmark is its means to swiftly leverage freshly disclosed vulnerabilities, particularly targeting public-facing servers and edge devices,” Verify Stage stated.
“In some instances, the deployment of the exploits is inside 1 working day immediately after a [proof-of-concept] is released, appreciably expanding the danger amount posed by this actor.”

Attacks mounted by the adversary have leveraged unpatched Ivanti Join Protected VPN, Magento, Qlik Perception, and maybe Apache ActiveMQ servers as an initial an infection vector to gain unauthorized access. The team is explained to be active due to the fact at least January 2022.
A effective exploitation is adopted by the deployment of a cross-system remote access trojan (RAT) dubbed Nerbian RAT, which was initial disclosed by Proofpoint in Might 2022, as very well as its simplified variant called MiniNerbian. The use of the Linux model of Nerbian RAT was beforehand highlighted by Darktrace.
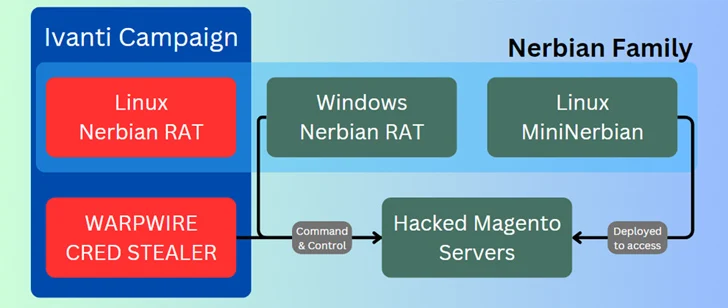
Both equally the strains let for execution of arbitrary commands acquired from a command-and-regulate (C2) server and exfiltrating the success backed to it.
Some of the other equipment utilised by Magnet Goblin include the WARPWIRE JavaScript credential stealer, the Go-based tunneling software acknowledged as Ligolo, and authentic remote desktop offerings such as AnyDesk and ScreenConnect.

“Magnet Goblin, whose campaigns surface to be fiscally motivated, has been swift to undertake 1-working day vulnerabilities to deliver their custom Linux malware, Nerbian RAT and MiniNerbian,” the business mentioned.
“All those tools have operated under the radar as they primarily reside on edge-devices. This is section of an ongoing pattern for menace actors to target locations which till now have been remaining unprotected.”
Identified this report interesting? Adhere to us on Twitter and LinkedIn to read extra unique content material we put up.
Some parts of this article are sourced from:
thehackernews.com


 Microsoft Confirms Russian Hackers Stole Source Code, Some Customer Secrets
Microsoft Confirms Russian Hackers Stole Source Code, Some Customer Secrets