A new malvertising campaign has been observed distributing an updated variation of a macOS stealer malware referred to as Atomic Stealer (or AMOS), indicating that it is really being actively taken care of by its writer.
An off-the-shelf Golang malware accessible for $1,000 for each month, Atomic Stealer very first came to gentle in April 2023. Shortly immediately after that, new variants with an expanded established of information-collecting characteristics ended up detected in the wild, targeting avid gamers and cryptocurrency consumers.
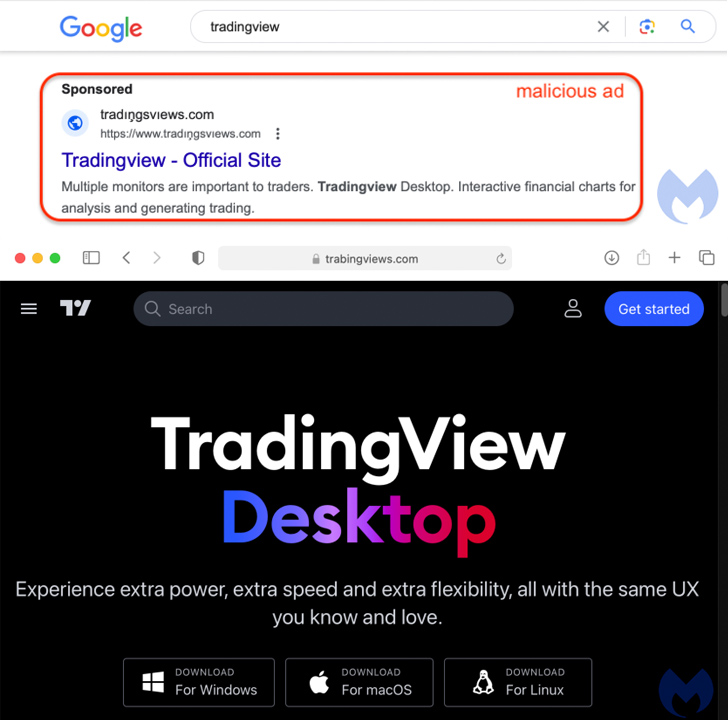
Malvertising by using Google Advertisements has been observed as the key distribution vector in which users exploring for common software package, authentic or cracked, on look for engines are demonstrated bogus advertisements that immediate to websites hosting rogue installers.
The hottest marketing campaign consists of the use of a fraudulent internet site for TradingView, prominently featuring a few buttons to down load the software package for Windows, macOS, and Linux functioning programs.

“The two the Windows and Linux buttons level to an MSIX installer hosted on Discord that drops NetSupport RAT,” Jérôme Segura, director of danger intelligence at Malwarebytes, explained.
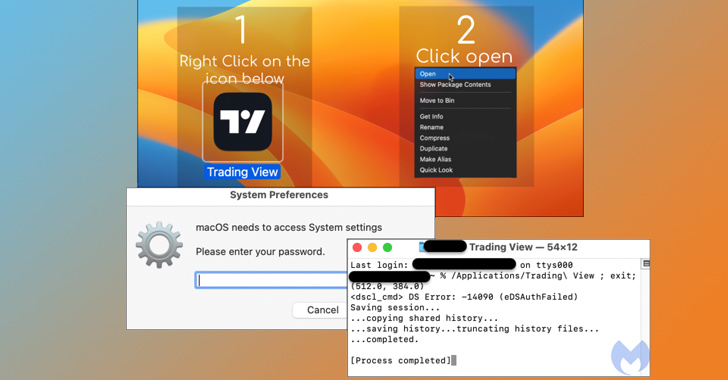
The macOS payload (“TradingView.dmg”) is a new edition of Atomic Stealer released at the conclude of June, which is bundled in an advert-hoc signed app that, the moment executed, prompts end users to enter their password on a phony prompt and harvest files as properly as information saved in iCloud Keychain and web browsers.
“Atomic stealer also targets both equally Chrome and Firefox browsers and has an intensive hardcoded record of crypto-similar browser extensions to attack,” SentinelOne earlier observed in Could 2023. Pick out variants have also targeted Coinomi wallets.
The supreme intention of the attacker is to bypass Gatekeeper protections in macOS and exfiltrate the stolen data to a server under their management.
The progress will come as macOS is more and more getting a viable target of malware assaults, with a variety of macOS-unique facts stealers appearing for sale in crimeware boards in latest months to take benefit of the wide availability of Apple programs in corporations.
Forthcoming WEBINARWay Also Susceptible: Uncovering the Point out of the Identity Attack Area
Achieved MFA? PAM? Services account security? Come across out how properly-outfitted your group really is against identification threats
Supercharge Your Competencies
“Whilst Mac malware definitely does exist, it tends to be less detected than its Windows counterpart,” Segura reported. “The developer or vendor for AMOS in fact produced it a marketing position that their toolkit is capable of evading detection.”
Atomic Stealer is not the only malware propagated through malvertising and search engine optimization (Seo) poisoning campaigns, as evidence has emerged of DarkGate (aka MehCrypter) latching onto the identical delivery system.
New versions of DarkGate have due to the fact been employed in attacks mounted by menace actors employing strategies identical to that of Scattered Spider, Aon’s Stroz Friedberg Incident Response Solutions mentioned last month.
Uncovered this posting attention-grabbing? Follow us on Twitter and LinkedIn to go through additional exceptional written content we article.
Some parts of this article are sourced from:
thehackernews.com

 The State of the Virtual CISO Report: MSP/MSSP Security Strategies for 2024
The State of the Virtual CISO Report: MSP/MSSP Security Strategies for 2024