The Luna Moth marketing campaign has extorted hundreds of thousands of bucks from many victims in the legal and retail sectors.
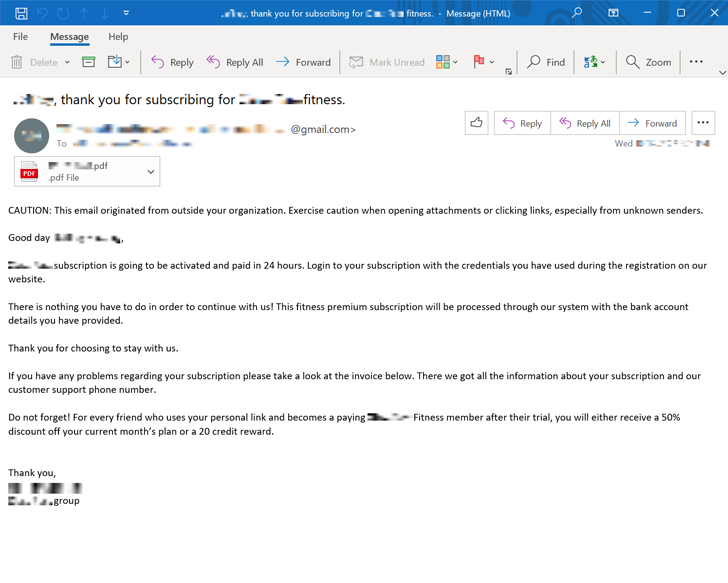
The attacks are notable for using a approach called callback phishing or telephone-oriented attack shipping (TOAD), wherein the victims are social engineered into producing a phone connect with by phishing e-mails containing invoices and subscription-themed lures.
Palo Alto Networks Device 42 said the assaults are the “products of a single very arranged campaign,” incorporating, “this threat actor has substantially invested in simply call centers and infrastructure which is one of a kind to each individual victim.”
The cybersecurity organization explained the activity as a “pervasive multi-thirty day period marketing campaign that is actively evolving.”
What’s notable about callback phishing is that the email messages are wholly devoid of any destructive attachment or booby-trapped backlink, enabling them to evade detection and slip past email security answers.
These messages generally come with an bill that involves a phone variety that the users can contact to cancel the intended membership. In truth, even so, the victims are routed to an actor-controlled phone middle and connected to a dwell agent on the other conclude, who ends up setting up a remote accessibility instrument for persistence.
“The attacker will then look for to determine beneficial information on the victim’s pc and connected file shares, and they will quietly exfiltrate it to a server they regulate using a file transfer software,” Device 42 researcher Kristopher Russo claimed.
The marketing campaign may possibly be source intense, but is also technically much less refined and possible to have a a great deal better achievement level than other phishing attacks.
On major of that, it permits extortion without encryption, permitting malicious actors to plunder sensitive data sans the want to deploy ransomware to lock the data files soon after exfiltration.
The Luna Moth actor, also acknowledged as Silent Ransom, has turn out to be an skilled of sorts when it comes to pulling off these strategies. In accordance to AdvIntel, the cybercrime group is considered to be the mastermind guiding the BazarCall assaults previous year.
To give these assaults a veneer of legitimacy, the adversaries, alternatively of dropping a malware like BazarLoader, consider benefit of authentic applications like Zoho Support to remotely interact with a victim’s computer, abusing the entry to deploy other reliable software such as Rclone or WinSCP for harvesting knowledge.
Extortion calls for array from two to 78 Bitcoin based on the corporation focused, with the menace actor building special cryptocurrency wallets for each and every payment. The adversary is also explained to present special discounts of practically 25% for prompt payment, though there is certainly no guarantee that the details is deleted.
“The risk actors behind this campaign have taken great pains to keep away from all non-important applications and malware, to lower the potential for detection,” Russo claimed. “Because there are pretty several early indicators that a sufferer is underneath attack, employee cybersecurity recognition instruction is the initially line of protection.”
Discovered this posting intriguing? Comply with THN on Fb, Twitter and LinkedIn to go through far more special content material we article.
Some parts of this article are sourced from:
thehackernews.com


 U.S. Authorities Seize Domains Used in ‘Pig butchering’ Cryptocurrency Scams
U.S. Authorities Seize Domains Used in ‘Pig butchering’ Cryptocurrency Scams