The infamous North Korea-connected menace actor regarded as the Lazarus Team has been attributed to a new international campaign that consists of the opportunistic exploitation of security flaws in Log4j to deploy previously undocumented distant entry trojans (RATs) on compromised hosts.
Cisco Talos is tracking the exercise under the name Operation Blacksmith, noting the use of 3 DLang-dependent malware people, including a RAT identified as NineRAT that leverages Telegram for command-and-regulate (C2), DLRAT, and a downloader dubbed BottomLoader.
The cybersecurity firm explained the most up-to-date methods of the adversary as a definitive shift and that they overlap with the cluster greatly tracked as Andariel (aka Onyx Sleet or Silent Chollima), a sub-group inside the Lazarus umbrella.
“Andariel is generally tasked with preliminary entry, reconnaissance and creating extended time period obtain for espionage in guidance of the North Korean government’s countrywide pursuits,” Talos scientists Jung soo An, Asheer Malhotra, and Vitor Ventura stated in a specialized report shared with The Hacker News.
Attack chains involve the exploitation of CVE-2021-44228 (aka Log4Shell) in opposition to publicly-obtainable VMWare Horizon servers to supply NineRAT. Some of the well known sectors targeted involve manufacturing, agriculture, and physical security.
Forthcoming WEBINAR Cracking the Code: Study How Cyber Attackers Exploit Human Psychology
Ever wondered why social engineering is so productive? Dive deep into the psychology of cyber attackers in our forthcoming webinar.
Be part of Now
The abuse of Log4Shell is not shocking specified the reality that 2.8 % of applications are continue to utilizing susceptible versions of the library (from 2.-beta9 as a result of 2.15.) just after two several years of public disclosure, in accordance to Veracode, with a further 3.8% working with Log4j 2.17., which, whilst not vulnerable to CVE-2021-44228, is inclined to CVE-2021-44832.
NineRAT, very first developed all over Could 2022, is stated to have been put to use as early as March 2023 in an attack aimed at a South American agricultural group and then again in September 2023 on a European production entity. By using a genuine messaging assistance for C2 communications, the intention is to evade detection.
The malware acts as the main suggests of interaction with the contaminated endpoint, enabling the attackers to send out instructions to gather system information, add files of desire, down load further documents, and even uninstall and update alone.
“As soon as NineRAT is activated it accepts preliminary commands from the telegram centered C2 channel, to yet again fingerprint the contaminated systems,” the scientists pointed out.
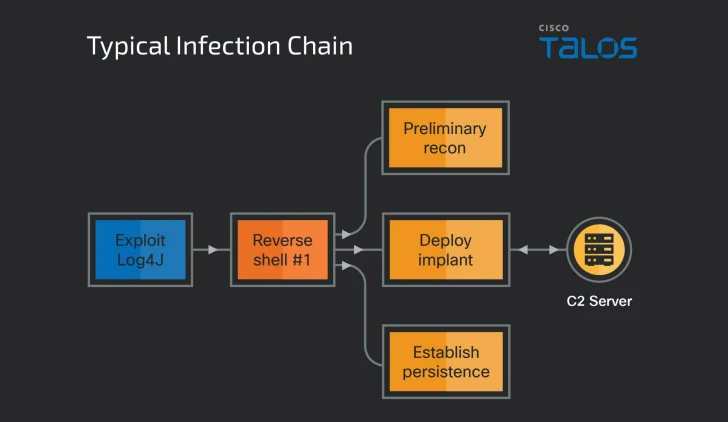
“Re-fingerprinting of contaminated devices indicates that the data gathered by Lazarus by means of NineRAT might be shared by other APT groups and fundamentally resides in a diverse repository from the fingerprint details collected initially by Lazarus during their first obtain and implant deployment period.”
Also utilized in the assaults just after original reconnaissance is a tailor made proxy tool called HazyLoad that was earlier identified by Microsoft as used by the menace actor as part of intrusions weaponizing critical security flaws in JetBrains TeamCity (CVE-2023-42793, CVSS score: 9.8). HazyLoad is downloaded and executed by suggests of one more malware termed BottomLoader.
Furthermore, Operation Blacksmith has been noticed providing DLRAT, which is both equally a downloader and a RAT equipped to accomplish procedure reconnaissance, deploy extra malware, and retrieve instructions from the C2 and execute them in the compromised methods.
“The multiple resources providing overlapping backdoor entry present Lazarus Group with redundancies in the event a device is learned, enabling extremely persistent accessibility,” the scientists stated.
The disclosure will come as the AhnLab Security Unexpected emergency Response Centre (ASEC) specific Kimsuky’s use of AutoIt variations of malware these types of as Amadey and RftRAT and distributing them by means of spear-phishing attacks bearing booby-trapped attachments and back links in an try to bypass security solutions.

Kimusky, also recognized by the names APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet (beforehand Thallium), Nickel Kimball, and Velvet Chollima, is an component functioning below North Korea’s Reconnaissance General Bureau (RGB), which also homes the Lazarus Group.
It was sanctioned by the U.S. Treasury Section on November 30, 2023, for accumulating intelligence to aid the regime’s strategic objectives.
“Soon after taking command of the contaminated program, to exfiltrate data, the Kimsuky team installs several malware this sort of as keyloggers and resources for extracting accounts and cookies from web browsers,” ASEC explained in an investigation printed past 7 days.
Found this post intriguing? Observe us on Twitter and LinkedIn to examine additional exclusive content we submit.
Some parts of this article are sourced from:
thehackernews.com


 Playbook: Your First 100 Days as a vCISO – 5 Steps to Success
Playbook: Your First 100 Days as a vCISO – 5 Steps to Success