The North Korea-joined Lazarus Team has been observed weaponizing flaws in an undisclosed application to breach a economic company entity in South Korea 2 times within just a span of a yr.
Even though the 1st attack in Might 2022 entailed the use of a vulnerable model of a certification application that is widely applied by community establishments and universities, the re-infiltration in Oct 2022 concerned the exploitation of a zero-day in the exact same system.
Cybersecurity agency AhnLab Security Crisis Reaction Heart (ASEC) said it can be refraining from mentioning the software owing to the fact that “the vulnerability has not been totally confirmed still and a software patch has not been produced.”
The adversarial collective, following obtaining an original foothold by an not known system, abused the zero-day bug to execute lateral movement, soon soon after which the AhnLab V3 anti-malware engine was disabled by using a BYOVD attack.
It’s truly worth noting listed here that the Convey Your Own Susceptible Driver, aka BYOVD, technique has been regularly employed by the Lazarus Team in latest months, as documented by both ESET and AhnLab in a series of stories late previous calendar year.
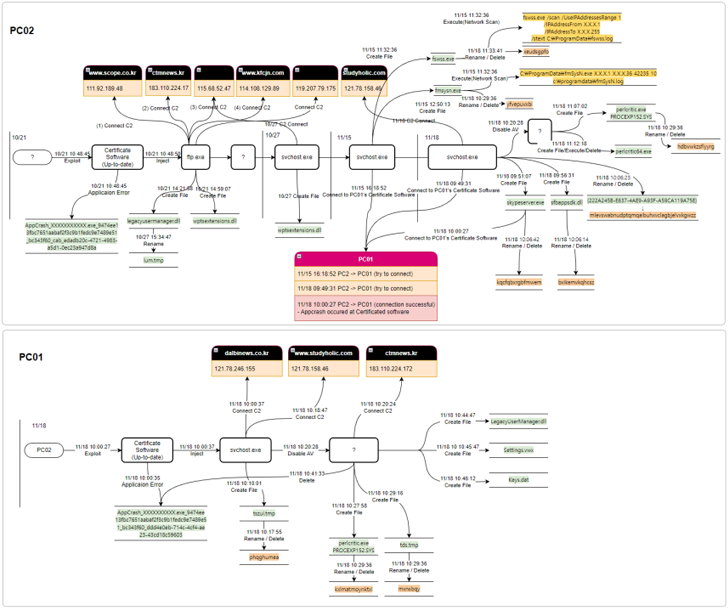
Among the other actions to conceal its destructive conduct incorporate transforming file names ahead of deleting them and modifying timestamps employing an anti-forensic procedure referred to as timestomping.
The attack eventually paved the way for a number of backdoor payloads (Keys.dat and Options.vwx) that are created to join to a distant command-and-regulate (C2) server and retrieve additional binaries and execute them in a fileless fashion.
Find out the Most current Malware Evasion Strategies and Avoidance Procedures
Ready to bust the 9 most harmful myths about file-dependent assaults? Join our future webinar and turn out to be a hero in the fight from patient zero infections and zero-day security events!
RESERVE YOUR SEAT
The development comes a 7 days following ESET drop mild on a new implant called WinorDLL64 which is deployed by the infamous menace actor by implies of a malware loader named Wslink.
“The Lazarus group is researching the vulnerabilities of a variety of other computer software and are regularly transforming their TTPs by altering the way they disable security products and carry out anti-forensic strategies to interfere or delay detection and analysis in get to infiltrate Korean establishments and providers,” ASEC stated.
Located this article fascinating? Stick to us on Twitter and LinkedIn to browse additional unique information we publish.
Some parts of this article are sourced from:
thehackernews.com


 Government Claims New UK GDPR Will Save Firms Billions
Government Claims New UK GDPR Will Save Firms Billions