Cybersecurity scientists are warning of publicly exposed Kubernetes configuration tricks that could put organizations at risk of offer chain assaults.
“These encoded Kubernetes configuration insider secrets had been uploaded to general public repositories,” Aqua security researchers Yakir Kadkoda and Assaf Morag reported in a new exploration printed before this week.
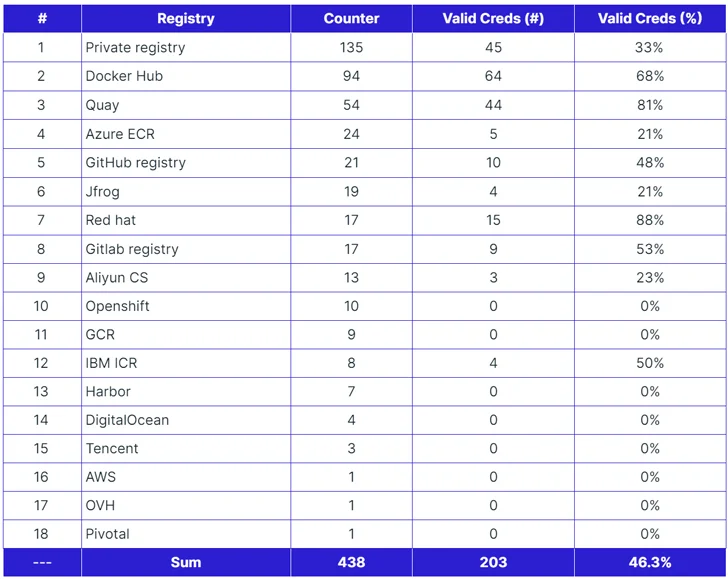
Some of individuals impacted incorporate two best blockchain companies and various other fortune-500 companies, in accordance to the cloud security organization, which leveraged the GitHub API to fetch all entries containing .dockerconfigjson and .dockercfg, which retail store qualifications for accessing a container graphic registry.

Of the 438 documents that perhaps held valid credentials for registries, 203 documents – about 46% – contained valid qualifications that provided entry to the respective registries. Ninety-three of the passwords were manually set by people today, as opposed to the 345 that were computer-created.
“In the bulk of circumstances, these credentials permitted for each pulling and pushing privileges,” the researchers famous. “Additionally, we generally uncovered personal container illustrations or photos inside most of these registries.”
On top of that, almost 50% of the 93 passwords were being considered weak. This comprised password, exam123456, windows12, ChangeMe, and dockerhub, between other people.
“This underscores the critical will need for organizational password policies that implement stringent password development principles to reduce the use of these vulnerable passwords,” the scientists extra.
Aqua explained it also found circumstances where corporations fall short to take away strategies from the data files that are dedicated to community repositories on GitHub, primary to inadvertent exposure.
But on a positive take note, all the credentials related with AWS and Google Container Registry (GCR) ended up identified to be temporary and expired, producing obtain difficult. In a comparable vein, the GitHub Container Registry required two-variable authentication (2FA) as an additional layer against unauthorized access.

“In some situations, the keys had been encrypted and as a result there was nothing to do with the essential,” the researchers mentioned. “In some circumstances, though the crucial was legitimate it had small privileges, usually just to pull or download a particular artifact or picture.”
According to Crimson Hat’s Condition of Kubernetes Security Report unveiled earlier this yr, vulnerabilities and misconfigurations emerged as prime security considerations with container environments, with 37% of the complete 600 respondents determining income/shopper decline as a outcome of a container and Kubernetes security incident.
Identified this report fascinating? Abide by us on Twitter and LinkedIn to read extra unique material we put up.
Some parts of this article are sourced from:
thehackernews.com


 Konni Group Using Russian-Language Malicious Word Docs in Latest Attacks
Konni Group Using Russian-Language Malicious Word Docs in Latest Attacks