Polish authorities establishments have been specific as element of a substantial-scale malware marketing campaign orchestrated by a Russia-joined country-condition actor known as APT28.
“The campaign despatched e-mails with written content intended to arouse the recipient’s desire and persuade him to simply click on the link,” the pc unexpected emergency reaction staff, CERT Polska, explained in a Wednesday bulletin.
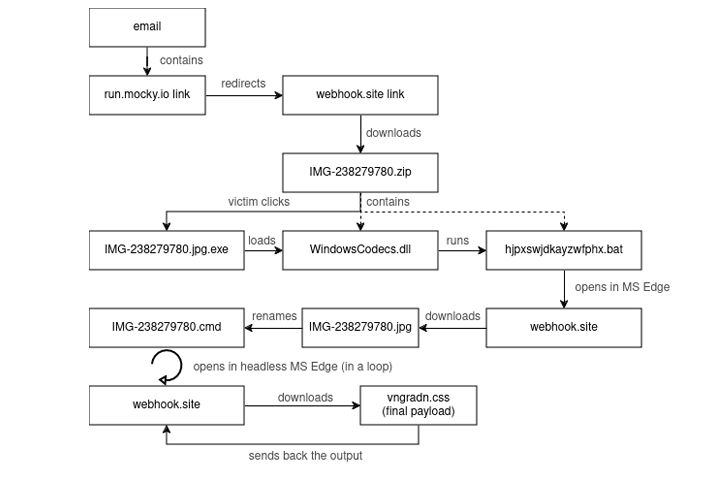
Clicking on the connection redirects the sufferer to the domain operate.mocky[.]io, which, in transform, is applied to redirect to yet another legitimate site named webhook[.]web site, a cost-free provider that allows builders to inspect data which is staying despatched by means of a webhook, in an effort to evade detection.
The action step requires the obtain of a ZIP archive file from webhook[.]site, which includes the Windows Calculator binary that masquerades as a JPG impression file (“IMG-238279780.jpg.exe”), a concealed batch script file, and yet another hidden DLL file (“WindowsCodecs.dll”).
Ought to a target run the software, the destructive DLL file is facet-loaded by indicates of a technique referred to as DLL facet-loading to in the long run operate the batch script, although pictures of an “genuine lady in a swimsuit along with one-way links to her real accounts on social media platforms” are shown in a web browser to sustain the ruse.

The batch script simultaneously downloads a JPG graphic (“IMG-238279780.jpg”) from webhook[.]internet site that is subsequently renamed to a CMD script (“IMG-238279780.cmd) and executed, subsequent which it retrieves the final-phase payload to assemble information and facts about the compromised host and mail the particulars again.
CERT Polska explained the attack chain bears similarities to a prior campaign that propagated a custom made backdoor referred to as HeadLace.
It is really worth noting the abuse of respectable solutions like Mocky and webhook[.]web site is a tactic regularly adopted by ATP28 actors so as to sidestep detection by security application.
“If your firm does not use the higher than-talked about companies, we recommend that you look at blocking the over-pointed out domains on edge devices,” it additional.
“Regardless of irrespective of whether you use the over-mentioned web-sites, we also advocate filtering e-mails for back links in webhook.website and run.mocky.io, due to the fact scenarios of their respectable use in the email content are extremely exceptional.”
The progress arrives days after NATO nations around the world accused the Kremlin-backed group of conducting a prolonged-expression cyber espionage marketing campaign targeting their political entities, state establishments, and critical infrastructure.
APT28’s malicious activities have also expanded to focus on iOS devices with the XAgent spyware, which was initial specific by Trend Micro in relationship with a campaign dubbed Operation Pawn Storm in February 2015.

“Largely focusing on political and govt entities in Western Europe, XAgent possesses abilities for distant regulate and info exfiltration,” Broadcom-owned Symantec mentioned.
“It can collect facts on users’ contacts, messages, machine facts, mounted apps, screenshots, and call documents. This data could likely be utilised for social engineering or spear-phishing strategies.”
Information of APT28’s assaults on Polish entities also follows a spike in monetarily motivated attacks by Russian e-criminal offense teams like UAC-0006 concentrating on Ukraine in the second fifty percent of 2023, even as companies in Russia and Belarus have been specific by a nation-condition actor recognised as Midge to supply malware capable of plundering delicate information.
Located this report interesting? Follow us on Twitter and LinkedIn to study extra unique content we publish.
Some parts of this article are sourced from:
thehackernews.com


 New Guide: How to Scale Your vCISO Services Profitably
New Guide: How to Scale Your vCISO Services Profitably