The North Korea-linked country-point out actor recognized as Kimsuky is suspected of employing a previously undocumented Golang-primarily based information and facts stealer called Troll Stealer.
The malware steals “SSH, FileZilla, C generate data files/directories, browsers, method details, [and] display captures” from contaminated techniques, South Korean cybersecurity enterprise S2W said in a new technological report.
Troll Stealer’s one-way links to Kimsuky stem from its similarities to regarded malware people, these kinds of as AppleSeed and AlphaSeed malware that have been attributed to the team.

Kimsuky, also tracked below the names APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet (beforehand Thallium), Nickel Kimball, and Velvet Chollima, is very well identified for its propensity to steal sensitive, confidential information and facts in offensive cyber functions.
In late November 2023, the risk actors have been sanctioned by the U.S. Treasury Department’s Workplace of Foreign Belongings Manage (OFAC) for collecting intelligence to further North Korea’s strategic targets.
The adversarial collective, in the latest months, has been attributed to spear-phishing assaults targeting South Korean entities to produce a variety of backdoors, together with AppleSeed and AlphaSeed.
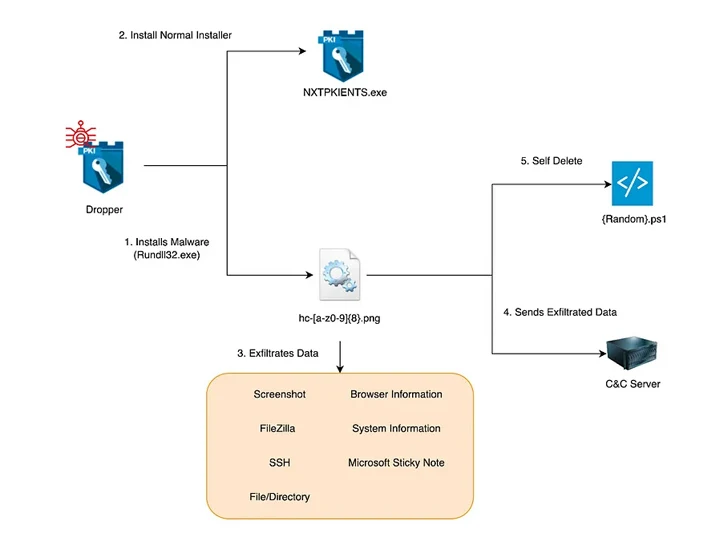
S2W’s most up-to-date assessment reveals the use of a dropper that masquerades as a security software installation file from a South Korean company named SGA Solutions to launch the stealer, which will get its identify from the route “D:/~/repo/golang/src/root.go/s/troll/agent” that’s embedded in it.
“The dropper runs as a authentic installer together with the malware, and each the dropper and malware are signed with a legitimate, legitimate D2Innovation Co.,LTD’ certificate, suggesting that the firm’s certification was essentially stolen,” the organization mentioned.
A stand-out element of Troll Stealer is its skill to pilfer the GPKI folder on contaminated devices, elevating the probability that the malware has been set to use in attacks targeting administrative and community corporations in the nation.

Given the absence of Kimsuky campaigns documenting the theft of GPKI folders, it has elevated the risk that the new behavior is either a shift in tactics or the get the job done of one more menace actor intently affiliated with the group that also has entry to the supply code of AppleSeed and AlphaSeed.
There are also symptoms that the menace actor may possibly be associated with a Go-based backdoor codenamed GoBear which is also signed with a reputable certificate related with D2Innovation Co., LTD and executes guidelines been given from a command-and-handle (C2) server.
“The strings contained in the names of the features it phone calls have been uncovered to overlap with the instructions utilized by BetaSeed, a C++-based mostly backdoor malware utilised by the Kimsuky team,” S2W claimed. “It is noteworthy that GoBear adds SOCKS5 proxy features, which was not earlier supported by the Kimsuky group’s backdoor malware.”
Located this report interesting? Abide by us on Twitter and LinkedIn to study more unique content we article.
Some parts of this article are sourced from:
thehackernews.com


 Critical Patches Released for New Flaws in Cisco, Fortinet, VMware Products
Critical Patches Released for New Flaws in Cisco, Fortinet, VMware Products