Cybersecurity researchers have found out that the malware known as BLOODALCHEMY utilized in assaults focusing on governing administration corporations in Southern and Southeastern Asia is in simple fact an current variation of Deed RAT, which is considered to be a successor to ShadowPad.
“The origin of BLOODALCHEMY and Deed RAT is ShadowPad and given the history of ShadowPad getting used in numerous APT campaigns, it is very important to pay out exclusive consideration to the usage craze of this malware,” Japanese organization ITOCHU Cyber & Intelligence mentioned.
BLOODALCHEMY was first documented by Elastic Security Labs in Oct 2023 in relationship with a campaign mounted by an intrusion established it tracks as REF5961 concentrating on the Affiliation of Southeast Asian Nations (ASEAN) nations around the world.

A barebones x86 backdoor prepared in C, it truly is injected into a signed benign method (“BrDifxapi.exe”) making use of a strategy identified as DLL aspect-loading, and is capable of overwriting the toolset, accumulating host details, loading further payloads, and uninstalling and terminating itself.
“When unconfirmed, the existence of so several powerful commands signifies that the malware may possibly be a subfeature of a greater intrusion set or malware package, however in enhancement, or an exceptionally centered piece of malware for a distinct tactical utilization,” Elastic researchers mentioned at the time.
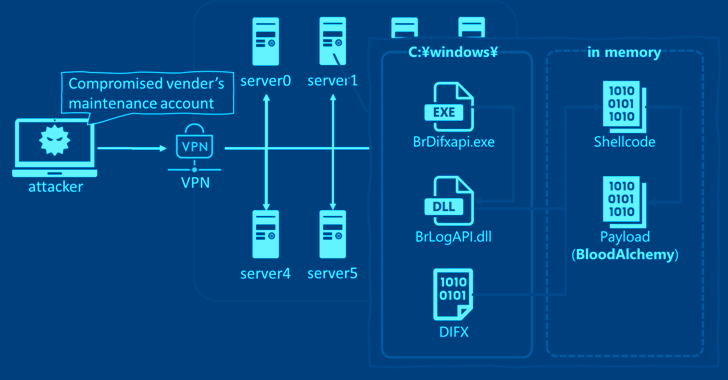
Attack chains deploying have been observed compromising a upkeep account on a VPN unit to acquire original accessibility to deploy BrDifxapi.exe, which is then applied to sideload BrLogAPI.dll, a loader that’s liable for executing the BLOODALCHEMY shellcode in memory after extracting it from a file named DIFX.
The malware employs what is identified as a run method that determines its actions, successfully allowing it to evade analysis in sandbox environments, set up persistence, build make contact with with a distant server, and handle the infected host by way of the implemented backdoor instructions.

ITOCHU’s investigation of BLOODALCHEMY has also discovered code similarities with Deed RAT, a multifaceted malware completely made use of by a risk actor known as House Pirates and is considered as the following iteration of ShadowPad, which in by itself is an evolution of PlugX.
“The initial remarkably comparable point is the exclusive details constructions of the payload header in both equally BloodAlchemy and Deed RAT,” the firm reported. “Some similarities have been located in the loading course of action of shellcode, and the DLL file utilized to browse the shellcode as very well.”

It really is worth noting that the two PlugX (Korplug) and ShadowPad (aka PoisonPlug) have been commonly used by China-nexus hacking teams more than the years.
The disclosure comes as a China-connected menace actor acknowledged as Sharp Dragon (beforehand Sharp Panda) has expanded their concentrating on to contain governmental businesses in Africa and the Caribbean as portion of an ongoing cyber espionage campaign.
Located this report appealing? Stick to us on Twitter and LinkedIn to go through more exclusive written content we post.
Some parts of this article are sourced from:
thehackernews.com

 Ransomware Attacks Exploit VMware ESXi Vulnerabilities in Alarming Pattern
Ransomware Attacks Exploit VMware ESXi Vulnerabilities in Alarming Pattern