An unfamiliar cryptocurrency exchange situated in Japan was the goal of a new attack before this thirty day period to deploy an Apple macOS backdoor called JokerSpy.
Elastic Security Labs, which is checking the intrusion established underneath the identify REF9134, mentioned the attack led to the set up of Swiftbelt, a Swift-based enumeration instrument encouraged by an open-source utility named SeatBelt.
JokerSky was to start with documented by Bitdefender final week, describing it as a advanced toolkit designed to breach macOS machines.

Really minor is acknowledged about the danger actor driving the attacks other than the truth that the attacks leverage a set of packages written in Python and Swift that come with capabilities to acquire details and execute arbitrary instructions on compromised hosts.
A most important element of the toolkit is a self-signed multi-architecture binary acknowledged as xcc that is engineered to test for FullDiskAccess and ScreenRecording permissions.
The file is signed as XProtectCheck, indicating an attempt to masquerade as XProtect, a developed-in antivirus technology in macOS that can make use of signature-centered detection principles to clear away malware from by now infected hosts.
In the incident analyzed by Elastic, the generation of xcc is followed by the danger actor “trying to bypass TCC permissions by building their individual TCC database and making an attempt to swap the existing 1.”
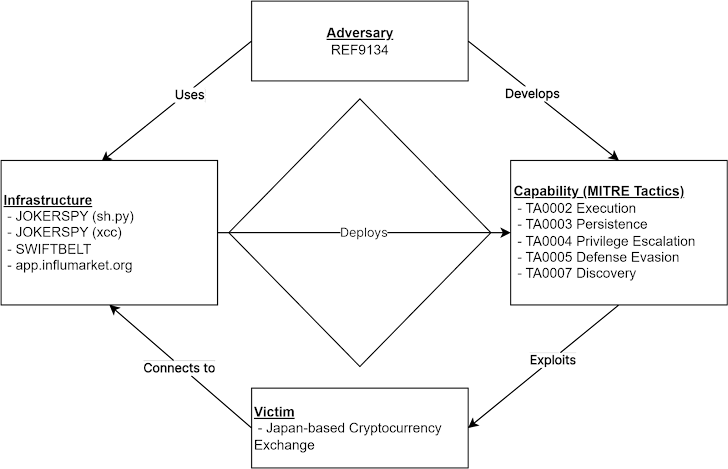
“On June 1, a new Python-based mostly resource was found executing from the exact same listing as xcc and was used to execute an open-supply macOS publish-exploitation enumeration tool identified as Swiftbelt,” security researchers Colson Wilhoit, Salim Bitam, Seth Goodwin, Andrew Pease, and Ricardo Ungureanu stated.
The attack specific a substantial Japan-based cryptocurrency provider company concentrating on asset trade for buying and selling Bitcoin, Ethereum, and other widespread cryptocurrencies. The identify of the corporation was not disclosed.

The xcc binary, for its element, is released by implies of Bash via a few diverse applications that are named IntelliJ Concept, iTerm (a terminal emulator for macOS), and Visual Studio Code, indicating that backdoored versions of software package development software program are most likely used to obtain original accessibility.
An additional noteworthy module set up as portion of the attack is sh.py, a Python implant that is made use of as a conduit to deliver other article-exploitation equipment like Swiftbelt.
“As opposed to other enumeration procedures, Swiftbelt invokes Swift code to keep away from creating command line artifacts,” the researchers claimed. “Notably, xcc variants are also penned applying Swift.”
Discovered this report attention-grabbing? Follow us on Twitter and LinkedIn to browse a lot more distinctive information we put up.
Some parts of this article are sourced from:
thehackernews.com


 How Generative AI Can Dupe SaaS Authentication Protocols — And Effective Ways To Prevent Other Key AI Risks in SaaS
How Generative AI Can Dupe SaaS Authentication Protocols — And Effective Ways To Prevent Other Key AI Risks in SaaS