A reverse engineering of the firmware operating on Ivanti Pulse Safe appliances has exposed many weaknesses, after again underscoring the obstacle of securing software package supply chains.
Eclypsiusm, which acquired firmware version 9.1.18.2-24467.1 as part of the approach, stated the base operating procedure made use of by the Utah-based program enterprise for the gadget is CentOS 6.4.
“Pulse Protected runs an 11-yr-previous version of Linux which hasn’t been supported since November 2020,” the firmware security corporation mentioned in a report shared with The Hacker News.
The progress arrives as risk actors are capitalizing on a selection of security flaws identified in Ivanti Connect Safe, Coverage Protected, and ZTA gateways to provide a huge array of malware, like web shells, stealers, and backdoors.
The vulnerabilities that have appear below energetic exploitation in new months comprise CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893. Past week, Ivanti also disclosed an additional bug in the software (CVE-2024-22024) that could permit danger actors to accessibility otherwise limited resources without any authentication.

In an alert posted yesterday, web infrastructure enterprise Akamai stated it has noticed “major scanning action” targeting CVE-2024-22024 setting up February 9, 2024, adhering to the publication of a proof-of-concept (PoC) by watchTowr.
Eclypsium reported it leveraged a PoC exploit for CVE-2024-21893 that was unveiled by Fast7 previously this month to get a reverse shell to the PSA3000 appliance, subsequently exporting the product image for abide by-on examination making use of the EMBA firmware security analyzer.
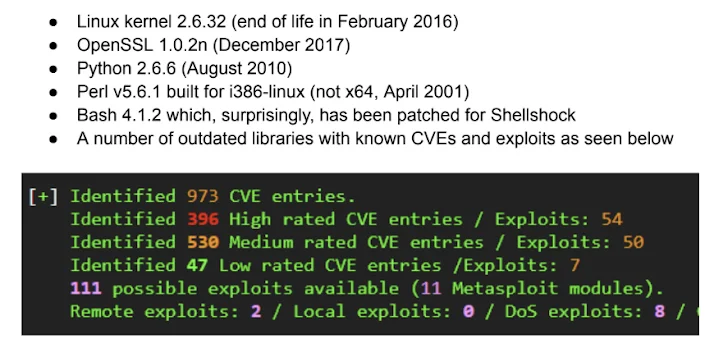
This not only uncovered a number of outdated offers – corroborating former conclusions from security researcher Will Dormann – but also a range of vulnerable libraries that are cumulatively vulnerable to 973 flaws, out of which 111 have publicly recognized exploits.
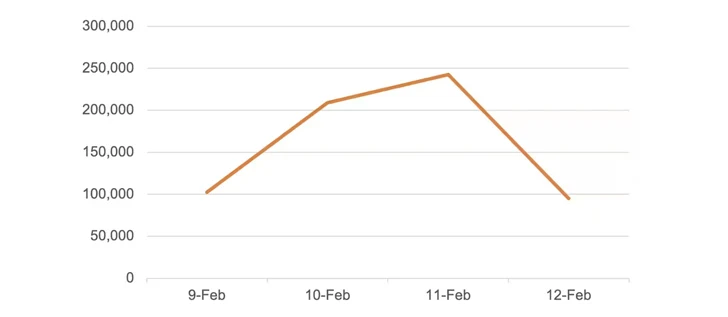 Selection of scanning requests for each working day concentrating on CVE-2024-22024
Selection of scanning requests for each working day concentrating on CVE-2024-22024
Perl, for occasion, has not been updated considering the fact that version 5.6.1, which was launched 23 many years in the past on April 9, 2001. The Linux kernel variation is 2.6.32, which attained close-of-lifestyle (EoL) as of March 2016.
“These old software offers are parts in the Ivanti Join Safe solution,” Eclypsium explained. “This is a best instance as to why visibility into electronic supply chains is critical and why enterprise consumers are ever more demanding SBOMs from their suppliers.”
In addition, a further assessment of the firmware unearthed 1,216 issues in 76 shell scripts, 5,218 vulnerabilities in 5,392 Python information, in addition to 133 outdated certificates.
The issues really don’t conclude there, for Eclypsium found a “security gap” in the logic of the Integrity Checker Device (ICT) that Ivanti has proposed its shoppers to use in purchase to appear for indicators of compromise (IoCs).
Specifically, the script has been identified to exclude in excess of a dozen directories these kinds of as /knowledge, /and so on, /tmp, and /var from being scanned, thus hypothetically allowing for an attacker to deploy their persistent implants in one of these paths and nonetheless pass the integrity examine. The device, however, scans the /home partition that merchants all product-specific daemons and configuration information.

As a consequence, deploying the Sliver post-exploitation framework to the /info directory and executing ICT reports no issues, Eclypsium discovered, suggesting that the software gives a “fake perception of security.”
It is really value noting that danger actors have also been observed tampering with the developed-in ICT on compromised Ivanti Link Protected products in an endeavor to sidestep detection.
In a theoretical attack demonstrated by Eclypsium, a danger actor could fall their future-stage tooling and retailer the harvested info in the /information partition and then abuse yet another zero-working day flaw to get accessibility to the unit and exfiltrate the data staged earlier, all the though the integrity device detects no indicators of anomalous activity.
“There have to be a process of checks and balances that lets shoppers and third-get-togethers to validate item integrity and security,” the business said. “The a lot more open this approach is, the better position we can do to validate the digital offer chain, namely the hardware, firmware, and program elements used in their merchandise.”
“When suppliers do not share info and/or function a shut procedure, validation becomes hard, as does visibility. Attackers will most certainly, as evidenced not long ago, acquire benefit of this condition and exploit the deficiency of controls and visibility into the method.”
Found this posting appealing? Comply with us on Twitter and LinkedIn to go through extra special articles we put up.
Some parts of this article are sourced from:
thehackernews.com


 How Nation-State Actors Target Your Business: New Research Exposes Major SaaS Vulnerabilities
How Nation-State Actors Target Your Business: New Research Exposes Major SaaS Vulnerabilities