Israeli organizations ended up qualified as part of two distinct strategies orchestrated by the Iranian nation-condition actor recognised as OilRig in 2021 and 2022.
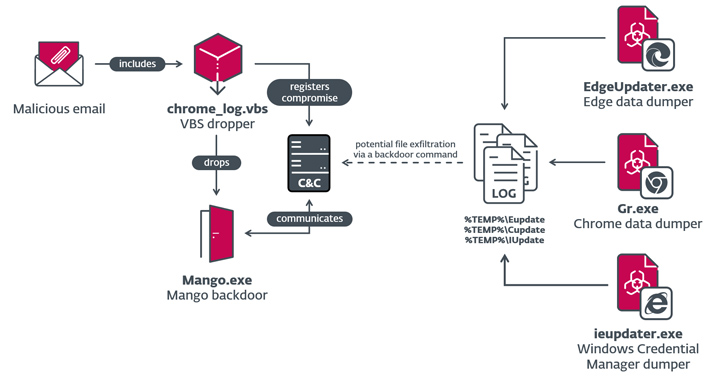
The campaigns, dubbed Outer Place and Juicy Combine, entailed the use of two previously documented initial-stage backdoors termed Photo voltaic and Mango, which were being deployed to obtain sensitive info from big browsers and the Windows Credential Supervisor.
“Each backdoors were being deployed by VBS droppers, presumably spread through spear-phishing email messages,” ESET security researcher Zuzana Hromcová mentioned in a Thursday examination.
OilRig (aka APT34, Cobalt Gypsy, Hazel Sandstorm, and Helix Kitten) is the identify assigned to an intrusion established affiliated with Iran’s Ministry of Intelligence and Security (MOIS). Energetic since 2014, the risk actor has utilized a vast vary of applications at its disposal to carry out data theft.

Before this February, Trend Micro found out OilRig’s use of a uncomplicated backdoor to steal users’ credentials, highlighting its “versatility to write new malware centered on investigated shopper environments and stages of accessibility.”
The team has also been noticed delivering an updated model of SideTwist as part of a phishing attack most likely focusing on U.S. firms.
That stated, the use of Mango malware was previously highlighted by both equally ESET and Microsoft in May perhaps 2023, with the latter attributing it to an emerging exercise cluster it tracks underneath the identify Storm-0133.
Storm-0133, also involved with MOIS, completely targets Israeli neighborhood federal government organizations and corporations serving the defense, lodging, and health care sectors, the Windows maker mentioned.
The most recent conclusions from the Slovak cybersecurity agency build the group’s continued target on Israel, working with spear-phishing lures to trick probable targets into installing the malware by using booby-trapped attachments.
In the Outer Room campaign observed in 2021, OilRig compromised an Israeli human methods web page and subsequently used it as a command-and-command (C2) server for Solar, a primary C#/.NET backdoor capable of downloading and executing documents and gathering information and facts.
Photo voltaic also acts as a automobile to deploy a downloader named SampleCheck5000 (or SC5k), which utilizes the Workplace Trade Web Solutions (EWS) API to obtain supplemental instruments for execution, as well as a utility to exfiltrate facts from the Chrome web browser referred to as MKG.
“Once SC5k logs into the distant Exchange server, it retrieves all the e-mail in the Drafts directory, sorts them by most current, holding only the drafts that have attachments,” Hromcová stated.
Forthcoming WEBINARAI vs. AI: Harnessing AI Defenses In opposition to AI-Powered Hazards
Ready to tackle new AI-driven cybersecurity issues? Be a part of our insightful webinar with Zscaler to deal with the expanding menace of generative AI in cybersecurity.
Supercharge Your Skills
“It then iterates over just about every draft concept with an attachment, searching for JSON attachments that comprise “info” in the physique. It extracts the benefit from the essential knowledge in the JSON file, base64 decodes and decrypts the worth, and phone calls cmd.exe to execute the ensuing command line string.”
The success of the command execution are staged and sent back to the operators by way of a new email message on the Exchange server and preserving it as a draft.
The Juicy Mix campaign of 2022 concerned the use of Mango, an enhanced edition of Photo voltaic incorporating extra capabilities and obfuscation approaches. For C2 reasons, the risk actor compromised a legitimate Israeli work portal web site.
“OilRig carries on to innovate and generate new implants with backdoor-like capabilities though acquiring new strategies to execute commands on remote methods,” Hromcová stated.
“The team deploys a established of customized put up-compromise resources that are utilised to accumulate qualifications, cookies, and browsing history from important browsers and from the Windows Credential Manager.”
Found this report intriguing? Stick to us on Twitter and LinkedIn to go through a lot more special content we article.
Some parts of this article are sourced from:
thehackernews.com

 High-Severity Flaws Uncovered in Atlassian Products and ISC BIND Server
High-Severity Flaws Uncovered in Atlassian Products and ISC BIND Server