The Iranian risk actor identified as Tortoiseshell has been attributed to a new wave of watering hole assaults that are intended to deploy a malware dubbed IMAPLoader.
“IMAPLoader is a .NET malware that has the capacity to fingerprint sufferer methods working with indigenous Windows utilities and functions as a downloader for additional payloads,” the PwC Threat Intelligence claimed in a Wednesday analysis.
“It uses email as a [command-and-control] channel and is in a position to execute payloads extracted from email attachments and is executed by way of new support deployments.”

Active considering the fact that at the very least 2018, Tortoiseshell has a heritage of working with strategic web page compromises as a ploy to aid the distribution of malware. Before this May well, ClearSky joined the group to the breach of eight internet websites related with shipping and delivery, logistics, and economic companies corporations in Israel.
The risk actor is aligned with the Islamic Groundbreaking Guard Corps (IRGC) and is also tracked by the broader cybersecurity neighborhood under the names Crimson Sandstorm (beforehand Curium), Imperial Kitten, TA456, and Yellow Liderc.
The most current established of attacks between 2022 and 2023 involves embedding destructive JavaScript in compromised respectable web-sites to collect more specifics about the readers, which includes their area, product info, and time of visits.
These intrusions concentrated mainly on the maritime, shipping and logistics sectors in the Mediterranean, in some instances top to the deployment of IMAPLoader as a follow-on payload should really the target be considered a superior-worth focus on.
IMAPLoader is said to be a substitute to a Python-based IMAP implant Tortoiseshell formerly utilized in late 2021 and early 2022, owing to the similarities in the features.

The malware functions as a downloader for upcoming-phase payloads by querying hard-coded IMAP email accounts, exclusively checking a mailbox folder misspelled as “Recive” to retrieve the executables from the message attachments.
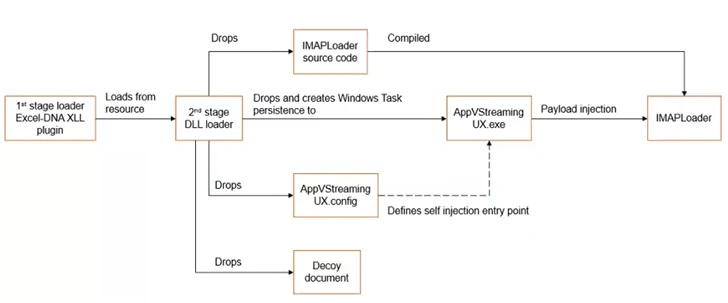
In an alternate attack chain, a Microsoft Excel decoy document is employed as an first vector to kick-commence a multi-stage system to provide and execute IMAPLoader, indicating that the risk actor is applying a selection of tactics and strategies to comprehend its strategic ambitions.
PwC claimed it also identified phishing web-sites created by Tortoiseshell, some of which are aimed at the journey and hospitality sectors within Europe, to carry out credential harvesting applying fake Microsoft indication-in webpages.
“This danger actor remains an energetic and persistent menace to quite a few industries and countries, which includes the maritime, transport, and logistics sectors within just the Mediterranean nuclear, aerospace, and protection industries in the U.S. and Europe and IT managed assistance providers in the Middle East,” PwC mentioned.
Found this report fascinating? Adhere to us on Twitter and LinkedIn to read through extra special articles we submit.
Some parts of this article are sourced from:
thehackernews.com


 Critical Flaw in NextGen’s Mirth Connect Could Expose Healthcare Data
Critical Flaw in NextGen’s Mirth Connect Could Expose Healthcare Data