Providers offered by an obscure Iranian organization recognised as Cloudzy are currently being leveraged by numerous danger actors, which include cybercrime teams and country-condition crews.
“Whilst Cloudzy is integrated in the United States, it nearly definitely operates out of Tehran, Iran – in doable violation of U.S. sanctions – less than the direction of a person
going by the identify Hassan Nozari,” Halcyon stated in a new report released Tuesday.
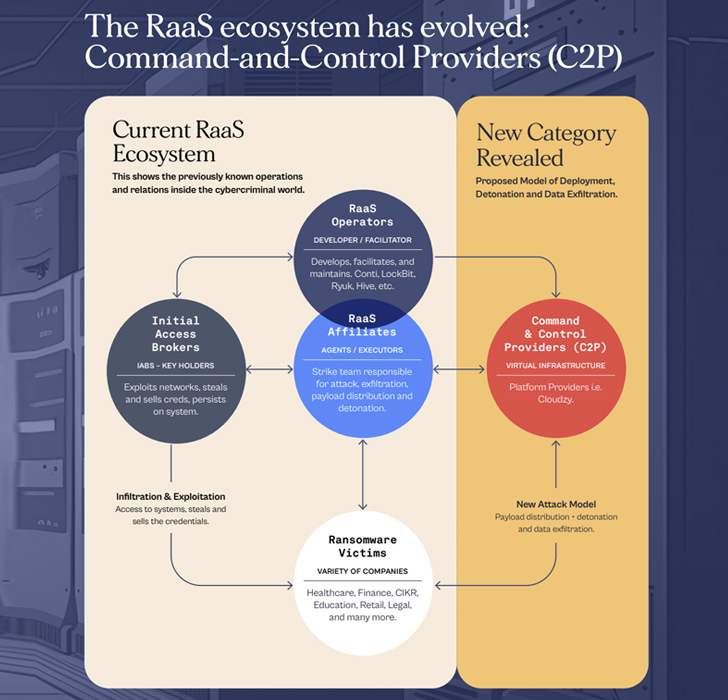
The Texas-dependent cybersecurity agency mentioned the organization functions as a command-and-management company (C2P), which offers attackers with Remote Desktop Protocol (RDP) digital private servers and other anonymized solutions that ransomware affiliate marketers and other individuals use to pull off the cybercriminal endeavors.

“[C2Ps] appreciate a liability loophole that does not need them to be certain that the infrastructure they offer is not getting used for illegal functions,” Halcyon mentioned in a statement shared with The Hacker Information.
The ransomware-as-a-company (RaaS) enterprise model is a remarkably-evolving 1, encompassing the main developers affiliates, who have out the attacks in exchange for a cut and initial accessibility brokers, who exploit recognized vulnerabilities or stolen credentials to get hold of a foothold and promote that accessibility to affiliates.
The emergence of C2P vendors points to a new established of actors who “knowingly or unwittingly” present the infrastructure to have out the attacks.
Some of the critical actors that are assessed to be leveraging Cloudzy incorporate point out-sponsored entities from China (APT10), India (Sidewinder), Iran (APT33 and APT34), North Korea (Kimsuky, Konni, and Lazarus Group), Pakistan (Clear Tribe), Russia (APT29 and Turla), and Vietnam (OceanLotus) as properly as cybercrime entities (Evil Corp and FIN12).
Also in the combine are two ransomware affiliates dubbed Ghost Clown and Area Kook which use the BlackBasta and Royal ransomware strains, respectively, and the controversial Israeli spyware vendor Candiru.

It’s suspected that malicious actors are banking on the simple fact that paying for VPS services from Cloudzy only requires a operating email tackle and anonymous payment in cryptocurrency, hence producing it ripe for abuse and boosting the possibility that risk actors could be weaponizing minimal-recognised companies to gasoline major hacks.
“If your VPS server is suspended for the reason that of misuse or abusive utilization such as prohibited employs: Phishing, Spamming, Child Porn, Attacking other people, and so on.,” reads aid documentation on Cloudzy’s web site. “There is a $250-$1000 fantastic or NO WAY for unsuspension this depends on the complaint form.”
“Though these C2P entities are ostensibly reputable businesses that may or could not know that their platforms are becoming abused for attack strategies, they nonetheless deliver a important pillar of the more substantial attack equipment leveraged by some of the most sophisticated risk actors,” the corporation stated.
Found this posting exciting? Follow us on Twitter and LinkedIn to browse more special content material we publish.
Some parts of this article are sourced from:
thehackernews.com


 Norwegian Entities Targeted in Ongoing Attacks Exploiting Ivanti EPMM Vulnerability
Norwegian Entities Targeted in Ongoing Attacks Exploiting Ivanti EPMM Vulnerability