Refined cyber actors backed by Iran regarded as OilRig have been connected to a spear-phishing campaign that infects victims with a new strain of malware named Menorah.
“The malware was intended for cyberespionage, able of figuring out the machine, looking through and uploading files from the machine, and downloading a further file or malware,” Development Micro researchers Mohamed Fahmy and Mahmoud Zohdy said in a Friday report.
The victimology of the attacks is not right away identified, though the use of decoys implies at least a person of the targets is an business situated in Saudi Arabia.

Also tracked less than the names APT34, Cobalt Gypsy, Hazel Sandstorm, and Helix Kitten, OilRig is an Iranian state-of-the-art persistent threat (APT) team that specializes in covert intelligence gathering operations to infiltrate and maintain accessibility in just specific networks.
The revelation builds on the latest results from NSFOCUS, which uncovered an OilRig phishing attack resulting in the deployment of a new variant of SideTwist malware, indicating that it really is beneath continual advancement.
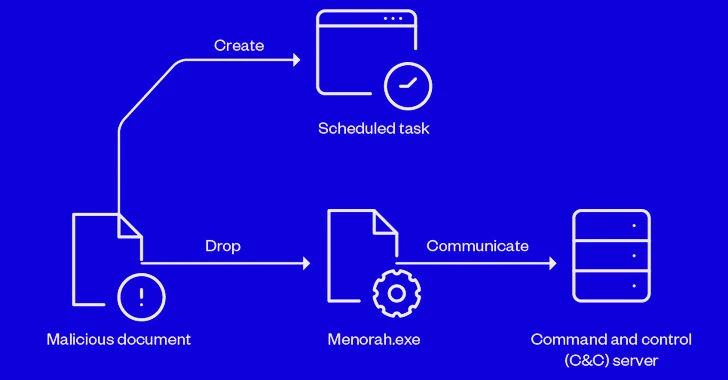
In the most up-to-date infection chain documented by Craze Micro, the lure document is utilized to create a scheduled undertaking for persistence and fall an executable (“Menorah.exe”) that, for its portion, establishes get hold of with a remote server to await additional guidelines. The command-and-command server is at present inactive.
Upcoming WEBINARFight AI with AI — Battling Cyber Threats with Upcoming-Gen AI Instruments
All set to deal with new AI-driven cybersecurity troubles? Be a part of our insightful webinar with Zscaler to handle the growing threat of generative AI in cybersecurity.
Supercharge Your Techniques
The .NET malware, an enhanced model of the first C-based mostly SideTwist implant found by Check Level in 2021, is armed with various attributes to fingerprint the targeted host, record directories and information, upload selected information from the compromised method, execute shell instructions, and down load information to the procedure.
“The group continuously develops and enhances applications, aiming to decrease security methods and researchers’ detection,” the researchers explained.
“Usual of APT groups, APT34 demonstrates their extensive methods and assorted expertise, and will possible persist in customizing routines and social engineering techniques to use for every focused group to make sure success in intrusions, stealth, and cyber espionage.”
Observed this report appealing? Observe us on Twitter and LinkedIn to go through more exceptional material we write-up.
Some parts of this article are sourced from:
thehackernews.com

 New Critical Security Flaws Expose Exim Mail Servers to Remote Attacks
New Critical Security Flaws Expose Exim Mail Servers to Remote Attacks