The danger actor tracked as TA866 has resurfaced right after a nine-month hiatus with a new huge-volume phishing marketing campaign to produce acknowledged malware family members these as WasabiSeed and Screenshotter.
The marketing campaign, noticed before this month and blocked by Proofpoint on January 11, 2024, involved sending thousands of invoice-themed e-mail focusing on North America bearing decoy PDF information.
“The PDFs contained OneDrive URLs that, if clicked, initiated a multi-phase infection chain inevitably foremost to the malware payload, a variant of the WasabiSeed and Screenshotter customized toolset,” the business security firm claimed.
TA866 was first documented by the organization in February 2023, attributing it to a marketing campaign named Screentime that dispersed WasabiSeed, a Visual Standard script dropper which is utilized to download Screenshotter, which is able of getting screenshots of the victim’s desktop at frequent intervals of time and exfiltrating that facts to an actor-managed domain.
There is evidence to advise that the arranged actor might be economically enthusiastic owing to the reality that Screenshotter functions as a recon instrument to establish significant-worth targets for publish-exploitation, and deploy an AutoHotKey (AHK)-based bot to ultimately drop the Rhadamanthys details stealer.

Subsequent conclusions from Slovak cybersecurity company ESET in June 2023 unearthed overlaps between Screentime and yet another intrusion established dubbed Asylum Ambuscade, a crimeware group energetic considering the fact that at minimum 2020 that also engages in cyber espionage operations.
The most up-to-date attack chain continues to be just about unchanged help you save for the switch from macro-enabled Publisher attachments to PDFs bearing a rogue OneDrive backlink, with the campaign relying on a spam assistance presented by TA571 to distribute the booby-trapped PDFs.
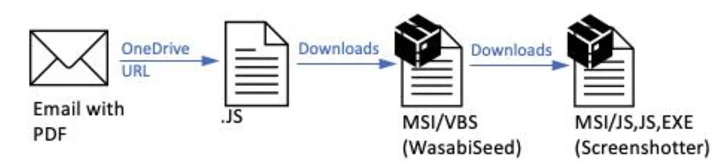
“TA571 is a spam distributor, and this actor sends substantial volume spam email strategies to deliver and set up a selection of malware for their cybercriminal consumers,” Proofpoint researcher Axel F explained.
This involves AsyncRAT, NetSupport RAT, IcedID, PikaBot, QakBot (aka Qbot), and DarkGate, the very last of which allows attackers to execute different instructions these as information and facts theft, cryptocurrency mining, and execution of arbitrary applications.
“Darkgate very first appeared in 2017 and is offered only to a tiny amount of attack teams in the kind of Malware-as-a-Support via underground community forums,” South Korean cybersecurity firm S2W explained in an examination of the malware this 7 days.
“DarkGate carries on to update it by adding functions and repairing bugs primarily based on assessment success from security researchers and distributors,” highlighting continued efforts built by adversaries to put into action anti-assessment strategies to bypass detection.
News of TA866’s resurgence will come as Cofense unveiled that delivery-connected phishing e-mails generally single out the producing sector to propagate malware like Agent Tesla and Formbook.
“Delivery-themed e-mails increase throughout the holiday break seasons, albeit only a little,” Cofense security researcher Nathaniel Raymond explained.

“For the most section, the annually developments counsel that these email messages observe a particular craze through the 12 months with various degrees of volumes, with the most substantial volumes remaining in June, October, and November.”
The improvement also follows the discovery of a novel evasion tactic that leverages the caching system of security products to get all over them by incorporating a Simply call To Motion (CTA) URL that points to a trustworthy web page in the phishing information sent to the specific personal.
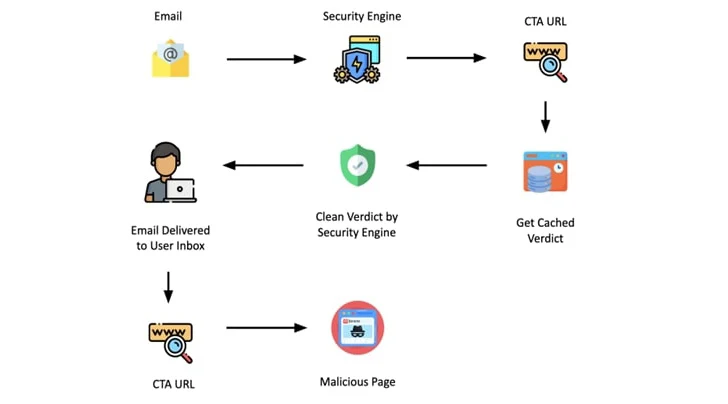
“Their strategy involves caching a seemingly benign model of the attack vector and subsequently altering it to deliver a destructive payload,” Trellix claimed, stating these attacks have disproportionately focused money companies, production, retail, and insurance policy verticals in Italy, the U.S., France, Australia, and India.
When such a URL receives scanned by the security engine, it really is marked as safe, and the verdict is stored in its cache for a set time. This also suggests that if the URL is encountered all over again inside of that time period of time, the URL is not reprocessed, and rather, the cached consequence is served.
Trellix pointed out that attackers are having gain of this quirk by waiting around till the security vendors procedure the CTA URL and cache their verdict, and then altering the website link to redirect to the meant phishing web page.
“With the verdict currently being benign, the email effortlessly lands in the victim’s inbox,” security scientists Sushant Kumar Arya, Daksh Kapur, and Rohan Shah explained. “Now, must the unsuspecting recipient make your mind up to open up the email and simply click on the backlink/button inside the CTA URL, they would be redirected to the destructive web site.”
Identified this write-up fascinating? Stick to us on Twitter and LinkedIn to read through far more exclusive material we article.
Some parts of this article are sourced from:
thehackernews.com


 NVIDIA RTX 4070 Super review: A 1,440p powerhouse for $599
NVIDIA RTX 4070 Super review: A 1,440p powerhouse for $599