About 34% of security vulnerabilities impacting industrial control systems (ICSs) that have been noted in the very first 50 percent of 2023 have no patch or remediation, registering a significant boost from 13% the prior year.
According to facts compiled by SynSaber, a complete of 670 ICS product flaws were being reported via the U.S. Cybersecurity and Infrastructure Security Company (CISA) in the very first 50 percent of 2023, down from 681 described through the initial 50 % of 2022.
Of the 670 CVEs, 88 are rated Critical, 349 are rated Superior, 215 are rated Medium, and 18 are rated Minimal in Severity. 227 of the flaws have no fixes in comparison to 88 in H1 2022.
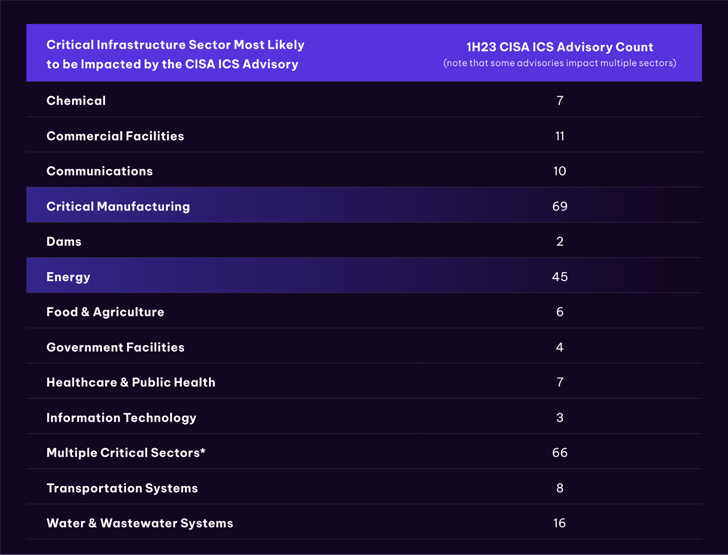
“Critical production (37.3% of complete noted CVEs) and Electricity (24.3% of the complete described) sectors are the most probably to be afflicted,” the OT cybersecurity and asset checking organization said in a report shared with The Hacker Information.
Other prominent field verticals involve h2o and wastewater programs, commercial services, communications, transportation, chemical, healthcare, food and agriculture, and authorities facilities.

Some of the other noteworthy results are as follows –
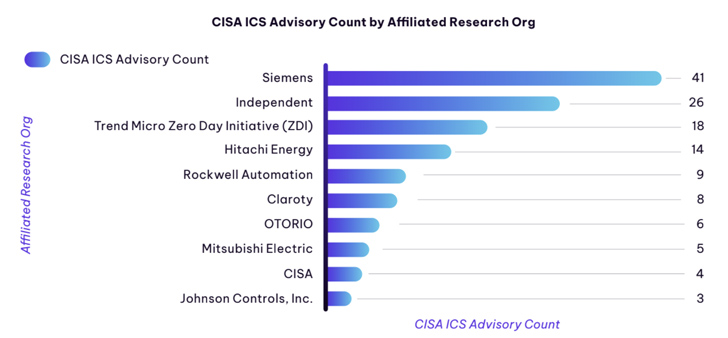
- Mitsubishi Electrical (20.5%), Siemens (18.2%), and Rockwell Automation (15.9%) had been the most impacted distributors in the critical manufacturing sector
- Hitachi Vitality (39.5%), Advantech (10.5%), Delta Electronics, and Rockwell Automation (the two 7.9%) ended up the most impacted sellers in the strength sector
- Siemens emerged as the primary entity developing the most CVEs by means of the first 50 % of 2023, accounting for 41 ICS advisories
- Use just after no cost, out-of-bounds read, poor enter validation, out-of-bounds produce, and race issue ended up the prime five computer software weaknesses
What’s more, a the greater part of CVE stories (84.6%) originated from first products companies (OEMs) and security sellers in the United States, followed by China, Israel, and Japan. Impartial and academic investigate accounted for 9.4% and 3.9%, respectively.
“Without end-Working day vulnerabilities continue being an issue – six CISA Advisories identified for ICS seller items that attained close of lifetime with ‘Critical’ severity vulnerabilities have no update, patch, components/ software program/ firmware updates, or known workarounds,” the organization pointed out.
SynSaber, having said that, famous that relying on CISA ICS advisories by itself could not be ample, and that corporations require to keep track of several sources of information and facts to get a improved thought of the flaws that could be appropriate to their environments.

“Care should be taken to comprehend vulnerabilities in the context of the environments in which they surface,” it said. “Considering the fact that just about every OT atmosphere is one of a kind and function-constructed, the likelihood of exploitation and impression that it might have will vary tremendously for every firm.”
The results come as Nozomi Networks uncovered a “significant quantity of network scanning indications in drinking water procedure services, cleartext password alerts across the creating elements market, system transfer action in industrial machinery, [and] OT protocol packet injection attempts in oil and gas networks.”
The IoT cybersecurity organization said it detected an regular of 813 exclusive assaults each day versus its honeypots, with top rated attacker IP addresses emanating from China, the U.S., South Korea, Taiwan, and India.
Discovered this report attention-grabbing? Comply with us on Twitter and LinkedIn to study extra unique articles we publish.
Some parts of this article are sourced from:
thehackernews.com


 Top Industries Significantly Impacted by Illicit Telegram Networks
Top Industries Significantly Impacted by Illicit Telegram Networks