The ThreatLocker® Zero Have faith in Endpoint Safety Platform implements a demanding deny-by-default, allow-by-exception security posture to give corporations the capacity to set policy-based controls inside of their setting and mitigate innumerable cyber threats, which include zero-days, unseen network footholds, and malware attacks as a immediate consequence of person mistake.
With the capabilities of the ThreatLocker® Zero Have confidence in Endpoint Protection Platform executed into their cybersecurity system, corporations in any market all around the entire world can verify off the specifications of most compliance frameworks and sleep superior at night realizing they are protected from the most devastating of cyberattacks, these kinds of as ransomware.
ThreatLocker has shared a free downloadable asset to equip IT experts with cybersecurity compliance very best procedures. This posting aims to elaborate on, and give a simple above of, the asset.
Complexities Throughout Compliance Frameworks
Cybersecurity compliance frameworks exist to assist businesses in setting up strong cybersecurity methods that will retain them ahead of threats. On the other hand, each and every framework is often ambiguous, building it hard to be certain the outlined necessities are met.
To insert far more complexity to decoding the needs of this compliance framework brainteaser, particular person frameworks are worded otherwise, even when pointing to the similar technology essential.
Compliance Finest Tactics
Regardless of the compliance framework, there is a standard set of complex controls that companies should carry out to improve their security posture and shift toward compliance.
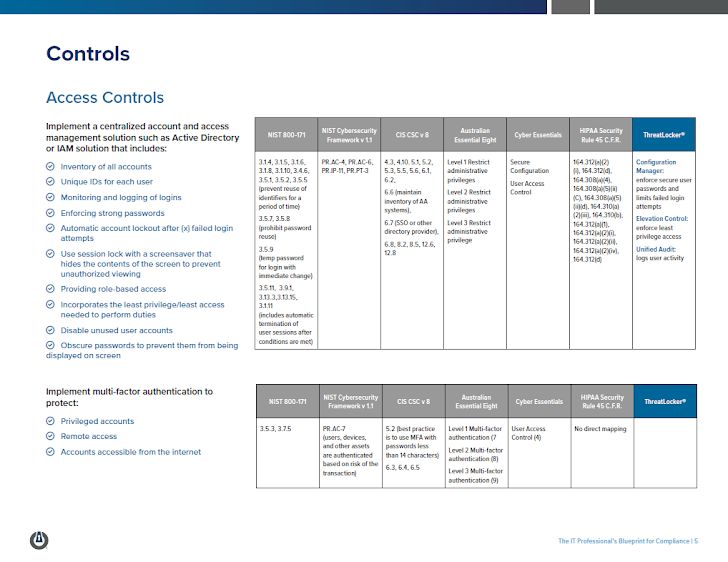
1. Access Management Options
Companies need to have a centralized account and accessibility management resolution that can stock all accessibility accounts, assign just about every person a exceptional ID, log all logins, give function-dependent accessibility, and implement the very least privilege/minimum access. The account and entry management resolution should really also enforce strong passwords, include an automatic lockout right after a specified range of failed login makes an attempt, defend the authentication feed-back, and disable identifiers right after a time period of inactivity.
2. Multi-Factor Authentication
Multi-issue authentication should be carried out and enforced for privileged account logins, for remote access logins, and when logging into any account available from the Internet.
3. Privileged Access Management (PAM)
A privileged accessibility management (PAM) resolution should really be utilised to defend directors and other privileged accounts. All privileged exercise should really be logged in a shielded central spot. Privileged functioning environments are divided from non-privileged, and non-privileged operating environments are unable to accessibility privileged. Privileged functioning environments must not be equipped to obtain non-privileged operating environments, the internet, email, or other web companies. The PAM alternative should really make it possible for for deactivating privileged accounts after 45 days of inactivity.
4. Distant Access Management Techniques
Companies have to have a remote accessibility management program that monitors and logs remote accessibility, offers automatic session lockout, controls the execution of privileged instructions, employs replay-resistant authentication, and makes use of patterned session locking to conceal the screen after a specified condition.
5. Allowlisting
Businesses must implement allowlisting (traditionally known as whitelisting) that delivers an up-to-date software package stock, displays put in computer software action and integrity, logs all executions, and can take away or disable unused, unauthorized, and unsupported software program, which include functioning units. The allowlisting answer need to include software containment to avert the generation of baby processes and management the execution of cell code, software program, libraries, and scripts. Any new software program need to be 1st deployed in a sandbox atmosphere and evaluated just before allowing it in the corporation.
6. Antimalware Solutions
Corporations should apply an antimalware solution that scans endpoints, web web pages, and detachable media in genuine-time, incorporates automatic definition updates, and helps prevent link to malicious web-sites.
7. Firewalls
Corporations need to integrate a firewall alternative that uses the least privilege, blocks all unnecessary ports and accessibility to the Internet, logs network activity, and terminates relationship following inactivity or the conclusion of a session.
8. Detection/Prevention Methods
Businesses should really employ an intrusion detection/avoidance solution, getting both a proactive and reactive tactic to their security.
9. Web Filters
Organizations need to have a web security solution that enforces network-based URL filters or DNS filtering.
10. Email Security
Email security solutions must be implemented to use only supported email shoppers, block all pointless file styles at the email gateway, and use DMARC. Make sure that email servers have an lively antimalware remedy.
11. Microsegmentation
Organizations want a technological remedy to microsegment the network virtually or working with VLANs.
12. Removable Media
Businesses require to put into action a solution to manage detachable media, like imposing encryption and restricting accessibility to it.
13. Mobile Device Management
Businesses need to apply a mobile system management option that encrypts mobile units, controls cell connections, and supports automatic lockout and distant wipe and lock.
14. Logging Remedy
Organizations need a safeguarded central logging solution that ingests and alerts on Windows function logs, software occasion logs, network logs, details entry logs, and user actions uniquely traced to the person. The logs should be reviewed frequently.
15. Patch Administration
Businesses need a patch administration alternative that scans their surroundings for missing patches, delivers stories, and can implement them.
16. Penetration Screening
Businesses will need to participate in penetration testing. Assessments really should be performed internally and on all externally struggling with providers. Any vulnerabilities identified must be remediated.
17. Threat Intelligence Sharing
Businesses really should take part in a menace intelligence sharing neighborhood in which they exchange information and facts concerning threats and vulnerabilities so they can mitigate threats and vulnerabilities proactively.
18. Knowledge Security
Businesses have to have to put into action measures to defend information. Info must have granular permissions applied. Only people who have to have accessibility to unique data to execute job responsibilities need to be ready to access that data.
19. Securely Discarding Info
Companies require a program to securely dispose of information just before gear is reused or removed.
20. Encrypting Sensitive Info
Businesses should really be certain that sensitive info is encrypted at rest (encrypted hard drives) and in transit (TLS or HTTPS) using a sturdy encryption algorithm.
21. Backing Up Programs
Corporations require to apply a backup method in which backups are done on a regular basis, duplicated with copies saved equally on and offsite, and routinely tested to make certain the firm always has a performing backup offered to assist in disaster restoration efforts.
22. Actual physical Security Controls
Organizations should really have ample actual physical security controls to guard from undesirable accessibility, this sort of as locks, cameras, and fences. Personnel and readers need to be monitored and logged. Belongings should be inventoried, identified, and tracked, and any unauthorized assets need to be resolved.
23. Security Recognition Schooling
Organizations require to apply a function-primarily based security awareness instruction solution, possibly developed in-house or acquired from a 3rd-get together supplier.
24. Published Procedures
Businesses will have to have prepared policies that staff browse and indication to implement each individual of the previously mentioned specialized controls.
Mapping Necessities Across Compliance Frameworks
Although compliance frameworks each and every have their own established of certain requirements, they share the typical aim of assisting businesses create strong cyber defense strategies to shield towards cyberattacks and the resulting data decline. Guarding this hot commodity is essential as attackers look for to exploit valuable details.
Firms with a powerful security posture, like all those using the ThreatLocker® Endpoint Safety Platform, are by now perfectly on their way to reaching compliance with any framework. Increase the ThreatLocker® Endpoint Defense System to your security strategy to assist build a thriving blueprint for compliance and realize entire world-course protection towards cyber threats.
ThreatLocker has curated a downloadable guidebook, “The It Professional’s Blueprint for Compliance”, that maps the parallel requirements of many compliance frameworks, which include:
- NIST SP 800-171
- NIST Cybersecurity Framework (CSF)
- The Center for Internet Security (CIS) Critical Security Controls (CSC)
- The Important 8 Maturity Design
- Cyber Essentials
- The Wellbeing Insurance policy Portability and Accountability Act (HIPAA)
The Book offers a mapped table for each and every of the higher than 24 compliance most effective practices mapped throughout the, also higher than, six compliance frameworks.
The tables that reside in the chapters of this asset have been built to provide thorough examples of what you can implement into your environment to check off the parallel specifications in just about every framework, from controls, to guidelines, to cybersecurity consciousness schooling.
Download your free of charge copy currently
Firms with a robust security posture, like individuals making use of the ThreatLocker® Zero Have confidence in Endpoint Safety System, are by now properly on their way to acquiring compliance with any framework. Include the ThreatLocker® Zero Have faith in Endpoint Protection Platform to your security method to support construct a effective blueprint for compliance and achieve world-class security towards cyber threats.
Master extra about ThreatLocker®
Identified this report appealing? This post is a contributed piece from a single of our valued companions. Observe us on Twitter and LinkedIn to examine much more exceptional information we write-up.
Some parts of this article are sourced from:
thehackernews.com


 U.S. Justice Department Sues Apple Over Monopoly and Messaging Security
U.S. Justice Department Sues Apple Over Monopoly and Messaging Security