Why SaaS Security Is a Problem
In modern electronic landscape, companies are ever more relying on Software program-as-a-Support (SaaS) programs to generate their functions. Nevertheless, this prevalent adoption has also opened the doorways to new security hazards and vulnerabilities.
The SaaS security attack surface carries on to widen. It started off with running misconfigurations and now requires a holistic technique to handling the complete SaaS ecosystem. This involves the continuous monitoring and administration of user access, roles and permissions, 3rd bash applications installed by buyers, risks deriving from SaaS user products and Identification Menace Detection & Reaction (ITDR).
There are a wide range of good reasons that SaaS security is so sophisticated currently. Firstly, there are a assorted selection of programs, every possessing its own UI and terminology. And individuals environments are dynamic, from SaaS distributors knowledge the great importance of security and continuously enhancing their applications with contemporary security measures to the at any time-evolving person governance essential such as onboarding, deprovisioning, changes in consumer access. These controls are helpful only when continually ruled, for every single application and each and every user. If which is not ample, these apps are managed by dispersed business enterprise departments, creating it virtually difficult for the security workforce to put into practice their security insurance policies.
ITDR Described
To deal with the Identification Danger Detection & Reaction challenge inside the SaaS ecosystem, SaaS security remedies need to have a impressive solution that detects and responds to identity-connected security threats dependent on vital Indicators of Compromise (IOCs) and User and Entity Habits Analytics (UEBA). These indicators deliver forensic indications of a potential breach, this sort of as malware, information breaches, unconventional behavior, and other suspicious situations.
ITDR is developed to tackle many SaaS-associated threats, which includes password-primarily based attacks, IP habits anomalies, account-primarily based detection, OAuth-based mostly assaults, unauthorized document obtain, unconventional consumer agent things to do, and much more. By offering a extensive suite of protecting measures, corporations should proactively defend their SaaS stack and make sure the integrity of their sensitive knowledge.
When it will come to dealing with SaaS threats, present risk detection and identity management strategies will not go significantly sufficient. Present-day SaaS environments are intricate and ITDR abilities inside of these landscapes require deep expertise and tested know-how.
Maor Bin, Co-Founder and CEO at Adaptive Protect had this to say about the new iteration of SaaS-ITDR, “Present ITDR solutions target on Endpoint and Lively Directory safety and do not layer the complicated SaaS atmosphere. On-prem Energetic Directory will before long turn out to be a legacy technology and as on-prem is shifting to SaaS, this will recreate a hole in id security posture administration in SaaS applications.”
This gap that Bin mentions is critical for SaaS security remedies to shut and that is why Adaptive Defend has taken strides and introduced out abilities to do just that.
Discover a lot more about ITDR and other core use situations to improve your SaaS security
Critical ITDR Abilities for SaaS Ecosystems
Your ITDR must be designed on the basis of a deep comprehending of SaaS characteristics and Identification Governance inside this landscape. Make confident you pick out a remedy that is centered on a really wide protection of SaaS purposes, who deeply understands the SaaS globe and provides exact danger detection via contextualization of a wide variety of sources and occasions.
As a signifies of prevention and very first layer of defense, the SSPM operates as the security layer in the Identity Cloth to create sturdy consumer governance. This includes too much permissions, access entitlement, consumer deprovisioning, and a lot more, throughout the total SaaS stack. Businesses ought to acquire deep and consolidated visibility and handle of person accounts, roles, permissions, privileged buyers, and actions.
As a 2nd layer of menace defense, your SaaS security alternative, like Adaptive Protect, ITDR abilities supply substantial protection in detecting anomalies and Techniques, Tactics, and Techniques (TTPs). By concentrating on context and creating user and enterprise profiles, it improves the accuracy of these detection alerts. On top of that, understanding predicted habits patterns and taking into consideration components these kinds of as user entry, permissions, and devices, allows the option to much better realize and prioritize alerts.
 Screenshot 1: Watch demonstrating threats by time with MITRE ATT&CK mapping
Screenshot 1: Watch demonstrating threats by time with MITRE ATT&CK mapping
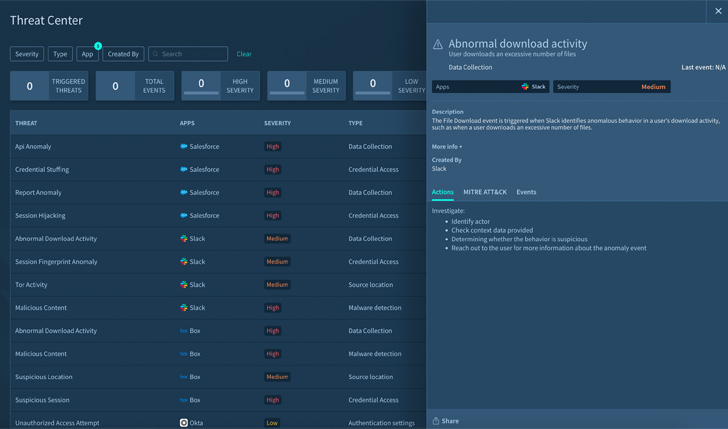 Screenshot 2: Threat middle demonstrating all monitored celebration
Screenshot 2: Threat middle demonstrating all monitored celebration
Key Capabilities Incorporate:
- Indicator of Compromise (IOC) Detection: Selection of proof indicating that the organization’s SaaS applications are less than attack or have been compromised. IOCs can contain knowledge from IP addresses, domain names, URLs and much more.
- User and Entity Actions Analytics (UEBA): Detection of behavioral anomalies, Adaptive Shield’s ITDR can recognize danger actors as they navigate by the organization’s purposes, giving proactive risk detection.
Complete Security Administration
When securing your SaaS environments, make sure your security system goes outside of identity menace detection and response. Your option should really include things like a selection of abilities that bolster your over-all security administration and provide a holistic prevention product for securing the SaaS Identification Fabric:
- Misconfiguration Administration: Identify security drifts throughout all security controls and get detailed remediation plans to make certain proper configuration and stop log-associated threats.
- Identification and Access Governance: Consolidate visibility of person accounts, permissions, and routines across all SaaS purposes, enabling efficient risk management and making certain acceptable access stages. Detect and mitigate the hazards associated with disabled or dormant accounts.
- SaaS-to-SaaS Entry and Discovery: Acquire visibility into linked apps, genuine or destructive, and evaluate the degree of risk they pose to your SaaS environment.
- Gadget-to-SaaS Risk Administration: Achieve context and visibility to correctly control dangers originating from SaaS users and their connected equipment.
With unparalleled insights and an array of features, Adaptive Shield empowers organizations to defend their SaaS stack, reduce details breaches, and safeguard their SaaS facts from emerging threats.
Get a 15-moment demo to see how you can secure your total SaaS stack
Uncovered this post intriguing? Comply with us on Twitter and LinkedIn to browse additional distinctive written content we article.
Some parts of this article are sourced from:
thehackernews.com


 Charming Kitten Targets Iranian Dissidents with Advanced Cyber Attacks
Charming Kitten Targets Iranian Dissidents with Advanced Cyber Attacks