A beforehand recognized Windows-primarily based ransomware pressure recognised as IceFire has expanded its target to goal Linux enterprise networks belonging to many media and leisure sector companies throughout the environment.
The intrusions entail the exploitation of a recently disclosed deserialization vulnerability in IBM Aspera Faspex file-sharing program (CVE-2022-47986, CVSS score: 9.8), in accordance to cybersecurity business SentinelOne.
“This strategic change is a sizeable shift that aligns them with other ransomware teams that also concentrate on Linux units,” Alex Delamotte, senior threat researcher at SentinelOne, reported in a report shared with The Hacker News.
A the vast majority of the assaults observed by SentinelOne have been directed towards organizations found in Turkey, Iran, Pakistan, and the U.A.E., nations around the world that are not ordinarily qualified by arranged ransomware crews.
IceFire was initially detected in March 2022 by the MalwareHunterTeam, but it wasn’t until August 2022 that victims have been publicized by means of its dark web leak web-site, in accordance to GuidePoint Security, Malwarebytes, and NCC Group.
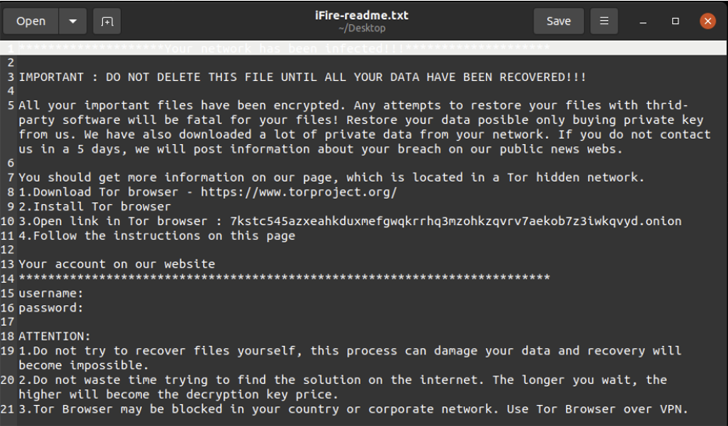
The ransomware binary focusing on Linux is a 2.18 MB 64-little bit ELF file that is set up on CentOS hosts working a susceptible version of IBM Aspera Faspex file server software package.
It can be also able of preventing encrypting sure paths so that the infected device continues to be operational.
WEBINARDiscover the Concealed Dangers of Third-Celebration SaaS Apps
Are you aware of the threats connected with 3rd-celebration application entry to your company’s SaaS apps? Be a part of our webinar to discover about the varieties of permissions remaining granted and how to limit risk.
RESERVE YOUR SEAT
“In comparison to Windows, Linux is extra challenging to deploy ransomware against–particularly at scale,” Delamotte said. “Several Linux devices are servers: standard infection vectors like phishing or push-by download are less effective. To conquer this, actors flip to exploiting software vulnerabilities.”
The development comes as Fortinet FortiGuard Labs disclosed a new LockBit ransomware marketing campaign using “evasive tradecraft” to avoid detection through .IMG containers that bypass Mark of The Web (MotW) protections.
Found this report intriguing? Follow us on Twitter and LinkedIn to read much more special written content we put up.
Some parts of this article are sourced from:
thehackernews.com


 Understanding the Shared Responsibility Model, Critical Step to Ensure Cloud Security
Understanding the Shared Responsibility Model, Critical Step to Ensure Cloud Security