In present day quickly evolving SaaS ecosystem, the emphasis is on human end users. This is just one of the most compromised areas in SaaS security management and involves demanding governance of consumer roles and permissions, monitoring of privileged users, their amount of activity (dormant, lively, hyperactive), their kind (inside/ exterior), regardless of whether they are joiners, movers, or leavers, and much more.
Not shockingly, security efforts have generally been human-centric. Configuration options involve applications like MFA and SSO for human authentication. Purpose-dependent obtain control (RBAC) limits the degree of accessibility password complexity guidelines block unauthorized human beings from accessing the software.
Yet, in the environment of SaaS, there is no lack of access granted to non-human actors, or in other phrases, 3rd get together linked apps.
Support accounts, OAuth authorizations, and API keys are just a few of the non-human identities that require SaaS access. When considered via the lens of the software, non-human accounts are equivalent to human accounts. They must be authenticated, granted a established of permissions, and monitored. Even so, due to the fact they are non-human, significantly less believed is given to ensuring security.
Non-human Entry Examples
Integrations are in all probability the least complicated way to realize non-human access to a SaaS app. Calendly is an app that eradicates the again-and-forth e-mails of appointment-earning by displaying a user’s availability. It integrates with a user’s calendar, reads the calendar to identify availability, and routinely provides appointments. When integrating with Google Workspace by an OAuth authorization, it requests scopes that help it to see, edit, share, and delete Google Calendars, among the other scopes. The integration is initiated by a human, but Calendly is non-human.
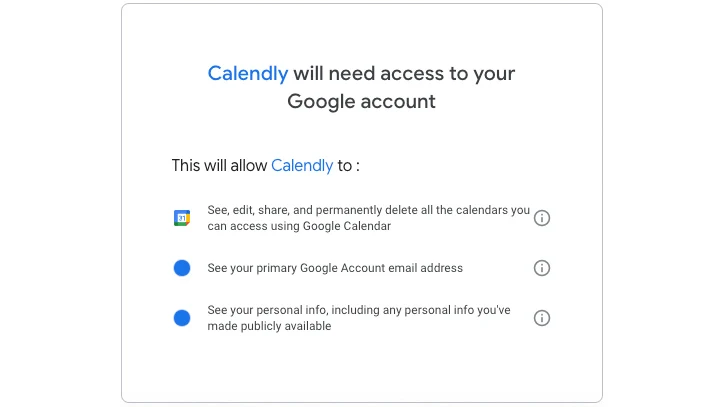 Determine 1: Calendly’s required authorization scopes
Determine 1: Calendly’s required authorization scopes
Other non-human accounts entail details sharing in between two or much more purposes. SwiftPOS is a position-of-sale (POS) application and system for bars, restaurants, and retail shops. Details captured by the POS is transferred to a enterprise intelligence platform, like Microsoft Power BI, wherever it is processed and analyzed. The data is transferred from SwiftPOS to Power BI by way of a non-human account.
The Problem of Securing Non-human Accounts
Taking care of and securing non-human accounts is not as simple as it sounds. For starters, every application has its very own approach to managing these styles of user accounts. Some applications, for instance, disconnect an OAuth integration when the user who approved it is deprovisioned from the app, when other individuals sustain the relationship.
SaaS purposes also consider different ways to running these accounts. Some incorporate non-human accounts in their consumer inventory, although other people retailer and display screen the information in a different portion of the software, creating them simple to ignore.
Human accounts can be authenticated through MFA or SSO. Non-human accounts, in distinction, are authenticated a single time and overlooked about until there is an issue with the integration. Human beings also have usual behavior styles, these kinds of as logging on to programs during functioning hrs. Non-human accounts usually accessibility apps during off-peak time to reduce network visitors and strain. When a human logs into their SaaS at 3 AM, it may trigger an investigation when a non-human hits the network at 3 AM, it really is just small business as regular.
In an hard work to simplify non-human account management, many corporations use the very same API essential for all integrations. To aid this, they grant wide authorization sets to the API key to address all the opportunity desires of the business. Other periods, a developer will use their individual large-authorization API essential to grant accessibility to the non-human account, enabling it to accessibility anything at all in the application. These API keys perform as all-entry passes utilized by a number of integrations, making them amazingly difficult to regulate.
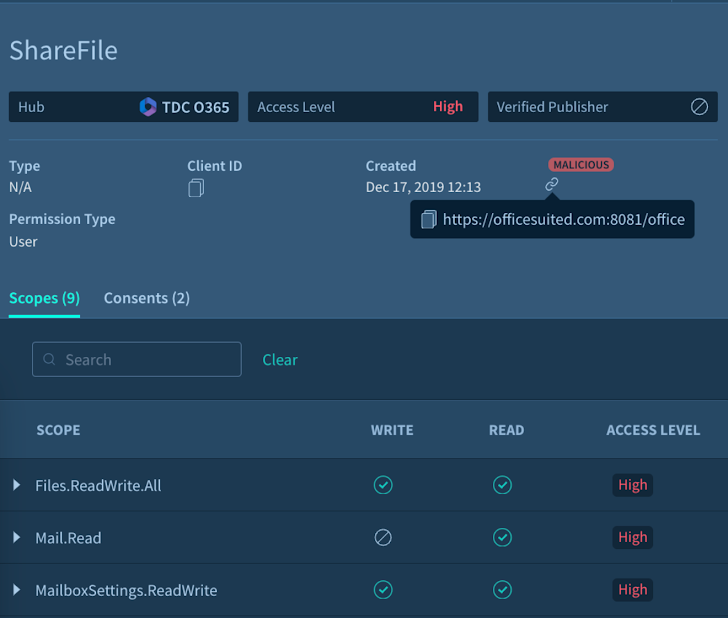 Figure 2: A Destructive OAuth Application detected through Adaptive Shield’s SSPM
Figure 2: A Destructive OAuth Application detected through Adaptive Shield’s SSPM
Sign up for THN’s approaching Webinar: Actuality Look at: Id Security for Human and Non-Human Identities
The Risk Non-human Accounts Insert to SaaS Stack
Non-human accounts are mostly unmonitored and have huge-ranging authorization scopes. This will make them an appealing goal for threat actors. By compromising any of these accounts, threat actors can enter the application undetected, primary to breaches, unauthorized modifications, or disruptions in support.
Getting Ways to Protected Non-human Accounts
Making use of a SaaS Security Posture Administration (SSPM) platform in concert with Identity Menace Detection & Response (ITDR) remedies, businesses can efficiently control their non-human accounts and detect when they behave anomalously.
Non-human accounts demand the same visibility by security teams as human accounts and really should be managed in the similar user stock as their human counterparts. By unifying identity management, it is far less difficult to look at obtain and permissions and update accounts regardless of who the owner is. It also makes certain a unified technique to account administration. Organizational procedures, these types of as prohibiting account sharing, must be used across the board. Non-human accounts should be constrained to particular IP addresses that are pre-authorised on an allow for checklist, and must not be granted accessibility via the normal login screens (UI login). Additionally, permissions should be tailored to fulfill their particular desires as apps, and not be wide-ranging or matching their human counterparts.
ITDR performs an vital function as effectively. Non-human accounts might access SaaS applications at all hrs of the night, but they are normally reasonably dependable in their interactions. ITDR can detect anomalies in behavior, irrespective of whether it is alterations in routine, the style of data currently being added to the application, or the pursuits currently being done by the non-human account.
The visibility supplied by SSPM into accounts and ITDR into non-human id conduct is crucial in managing threats and determining threats. This is an important action for retaining secure SaaS applications.
Go through far more about shielding against non-human identities
Discovered this posting interesting? This post is a contributed piece from one of our valued associates. Follow us on Twitter and LinkedIn to go through more unique content material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Ex-Google Engineer Arrested for Stealing AI Technology Secrets for China
Ex-Google Engineer Arrested for Stealing AI Technology Secrets for China