IT hygiene is a security greatest practice that ensures that digital belongings in an organization’s setting are secure and running correctly. Superior IT cleanliness involves vulnerability management, security configuration assessments, maintaining asset and process inventories, and thorough visibility into the functions happening in an environment.
As technology innovations and the equipment used by cybercriminals and cybersecurity professionals evolve, the methods utilized to carry out cyber assaults differ dependent on their complexity and uniqueness. Menace actors continually target businesses practising lousy IT hygiene to exploit acknowledged security weaknesses and human error. Security directors can defend versus cyberattacks by employing very good IT hygiene tactics like whitelisting systems, keeping methods up to date, and more.
Getting total visibility into the IT property is fundamental to developing an successful security system. The emergence of shadow IT, like rogue belongings, software, or consumer accounts, can produce a blind spot that threat actors can use as an attack vector. IT cleanliness tactics deal with the issue of visibility, making sure IT assets are sufficiently safeguarded for that reason reducing the attack surface.
Popular troubles faced by organizations working towards bad IT cleanliness
The pursuing are some of the issues organizations encounter as a consequence of bad IT cleanliness:
Why is IT hygiene important?
IT cleanliness is critical for protecting the security and resilience of an organization’s IT infrastructure. By adhering to good IT cleanliness procedures, corporations can be certain the security, performance, and dependability of their IT infrastructure though also complying with regulatory prerequisites and minimizing charges. IT cleanliness is significant as follows.
For starters, businesses can considerably greatly enhance their security posture by training fantastic IT hygiene through detailed vulnerability and patch management. This observe guarantees the safety of endpoints and programs from malicious attacks.
Moreover, by retaining fantastic IT hygiene, organizations can correctly lower their attack surface as they have better visibility of all their IT property.
Eventually, adhering to IT superior cleanliness tactics aids in meeting regulatory demands and sector expectations and conserving expenses. Proactive monitoring and reaction can guide companies in averting lawful sanctions and fiscal and reputational problems resulting from knowledge breaches and cyberattacks.
How Wazuh allows improve IT hygiene
Wazuh is a free, open resource security system that features unified XDR and SIEM abilities. It assists give security throughout workloads on cloud and on-premises environments. It offers a centralized look at for checking, detecting, and alerting security activities on monitored endpoints and cloud workloads.
This part highlights a number of Wazuh capabilities important to maintaining your network cleanse and protected.
1 —System stock: IT cleanliness begins with genuine-time visibility of electronic property in an natural environment and the gatherings occurring in them. Real-time visibility incorporates an up-to-day inventory of belongings and procedure. It includes instantly pinpointing risks, vulnerabilities, and misconfigurations throughout those property. The Wazuh procedure stock capacity collects relevant info like components, operating systems, ports, deals, Windows updates, and network interfaces on monitored endpoints. This information and facts is critical to building an helpful IT hygiene practice that improves the all round security posture of an business. For instance, the method inventory information is made up of a record of open ports on endpoints which can aid security administrators in identifying and closing pointless ports, therefore lessening the attack surface.
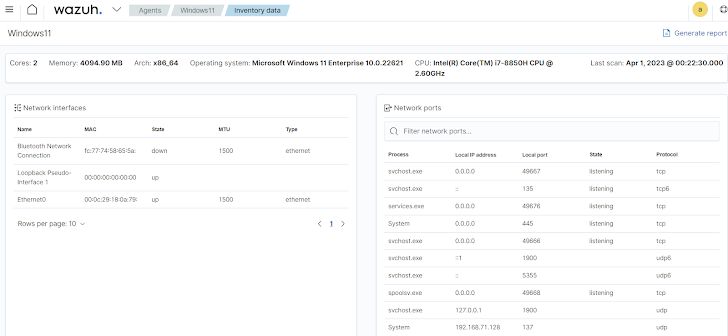 Figure 1: Wazuh dashboard displaying stock facts of a monitored endpoint.
Figure 1: Wazuh dashboard displaying stock facts of a monitored endpoint.
2 — Security Configuration Assessment (SCA): This involves conducting an comprehensive examination of security issues on monitored endpoints. It truly is based on compliance criteria to enhance security posture. Ideal IT hygiene methods demand security administrators to complete configuration assessments routinely to discover and remediate vulnerabilities and misconfigurations on endpoints. Security configuration assessments and endpoint hardening efficiently cut down an organization’s attack surface.
The Wazuh SCA ability assesses procedure configurations and triggers alerts when these configurations do not fulfill secure procedure policies. Depending on the industry, IT hygiene ensures that endpoints comply with HIPAA, PCI DSS, NIST 800-53 compliance benchmarks, and CIS benchmarks.
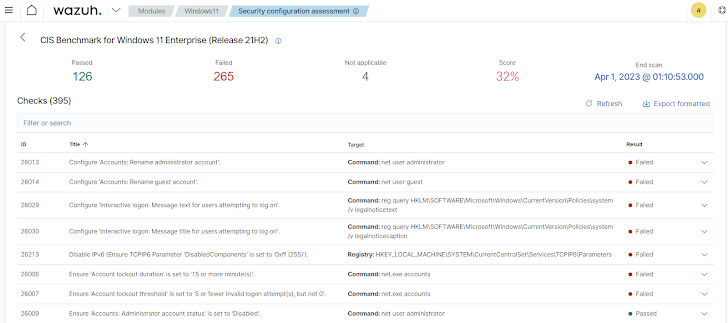 Figure 2: Wazuh dashboard exhibiting SCA report of a monitored endpoint.
Figure 2: Wazuh dashboard exhibiting SCA report of a monitored endpoint.
3 — Vulngrability management: This is a proactive and steady process of identifying, prioritizing, and remediating vulnerabilities on endpoints. The vulnerability management process is very important to manage IT hygiene. The Wazuh Vulnerability Detector ability allows you discover security vulnerabilities in the operating system and apps put in on monitored endpoints. Security directors can consider necessary steps to remediate vulnerabilities and improve IT cleanliness.
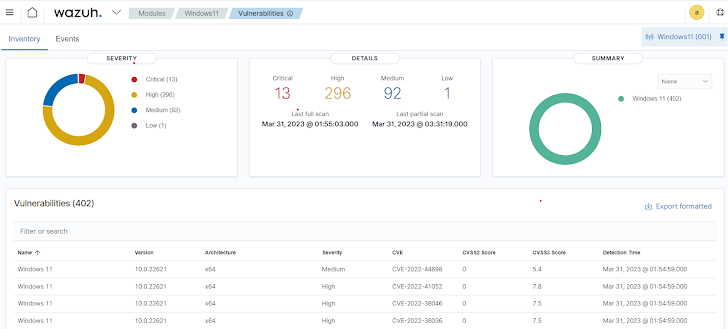 Figure 3: Wazuh dashboard showing vulnerability report of a monitored endpoint.
Figure 3: Wazuh dashboard showing vulnerability report of a monitored endpoint.
4 — Exgended threat detection and automatic response: This can assistance with IT cleanliness by continuously monitoring and examining endpoint things to do in an organization’s atmosphere. This continual monitoring assures proactive detection and reaction to threats or destructive actions. With an XDR/SIEM resolution, security groups can rapidly determine and isolate infected endpoints, thus blocking the unfold of malware in their business network. Wazuh helps corporations keep an eye on and safe their IT infrastructure by offering thorough menace detection and automatic reaction capabilities for endpoints. It helps to increase an organization’s IT hygiene procedures by supplying ongoing checking, malware detection, incident reaction, and compliance capabilities.
Conclusion
In present day ever-transforming threat landscape, developing a very good IT hygiene routine is important to reduce cyber criminals from producing security breaches. By leveraging the abilities of Wazuh, corporations can proactively detect and answer to security threats and preserve a robust cyber security posture.
Wazuh is a free, open up source SIEM and XDR answer that provides comprehensive security for companies. Wazuh enhances an organization’s IT cleanliness applying a number of capabilities to warn administrators of vulnerabilities, advise remediation measures, and respond to threats.
Wazuh has over 20 million once-a-year downloads and thoroughly supports consumers via a continually expanding open supply community.
Discovered this report attention-grabbing? Observe us on Twitter and LinkedIn to examine a lot more exceptional material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Fiat's Topolino EV is an Italian twist on the Citroen Ami
Fiat's Topolino EV is an Italian twist on the Citroen Ami