When businesses start off incorporating cybersecurity polices and cyber incident reporting specifications into their security protocols, it really is essential for them to create thorough plans for preparing, mitigation, and response to prospective threats.
At the coronary heart of your business lies your operational technology and critical systems. This spots them at the forefront of cybercriminal interest, as they request to exploit vulnerabilities, compromise your details, and demand ransoms. In today’s landscape, characterized by the at any time-present risk of ransomware assaults and the challenges posed by fragmented security options, safeguarding your firm is paramount. This is exactly where The National Institute of Benchmarks and Technology (NIST) advocates for the development of resilient, reliable security methods capable of foreseeing, enduring, and rebounding from cyberattacks.
In this manual, we will examine strategies to fortify your defenses in opposition to cyber threats and be certain uninterrupted functions. Fidelis Security, a pioneer in proactive cybersecurity, is below to stand with you on this journey.
Put together
1. Compliance and Regulatory Compliance:
Compliance is especially critical in controlled industries, where by adhering to sector-particular and authorities rules is non-negotiable. Fidelis Security’s Compliance Administration methods offer controls and checking abilities to guarantee that their organizations stay compliant, even in the experience of evolving regulatory specifications.
In a entire world of at any time-evolving rules, keeping compliance can be a challenging process. Fidelis Security simplifies this problem by providing in depth Compliance Management alternatives. These answers supply the controls and monitoring abilities needed to make certain that businesses adhere to business-particular and govt restrictions. By keeping compliance, they not only stay away from potential penalties but also bolster their overall cybersecurity posture.
Fidelis Security’s patented deep session examine (DSI) and actual-time traffic evaluation help analysts to locate information and facts on the network that is managed by regulatory compliances statutes, these as PCI, HIPAA, FISMA, GLBA and FERPA, in addition to PII, intellectual assets, finance-associated, and private or key info. By working with pre-crafted details leakage safety (DLP) or personalized-crafted plan, analysts can match these classes of written content in addition to any material they deem sensitive. Prevention can be enabled on the network to stop exfiltration as the transfer takes place, which might have originated from a malicious actor or perhaps an insider risk.
2. Steady Checking and Threat Detection:
Continual checking and actual-time risk detection are essential elements of a proactive cybersecurity technique. Fidelis Security’s Network Detection and Response (NDR) methods offer you steady monitoring and superior danger detection abilities, serving to companies detect and reply to threats in real-time.
In the face of consistently evolving cyber threats, the potential to monitor networks and detect threats in authentic-time is a must have. Fidelis Security’s Network Detection and Reaction (NDR) answers are intended to present continual monitoring of networks and endpoints. These alternatives leverage innovative danger detection abilities to determine and reply to probable threats in advance of they escalate. With Fidelis NDR, companies gain the higher hand in the ongoing fight towards cyberattacks.
Fidelis NDR employs several capabilities more than the complete platform to accomplish authentic-time detection and reaction. Deep Session Inspection (DSI) and decoding, Deep Packet Inspection (DPI), Antivirus detection (AV), and DNS protocol anomaly detections, on network and mail sensors, present a multi-faceted approach to network-based detection. Celebration and sequence-based detections, as perfectly as anomaly detections, are accomplished utilizing the Fidelis Collector, a genuine-time databases of all decoded session and object metadata that is gathered as it traverses the network. In addition, Fidelis Endpoint detects destructive objects, site visitors flows, and behaviors on endpoints with an agent put in.
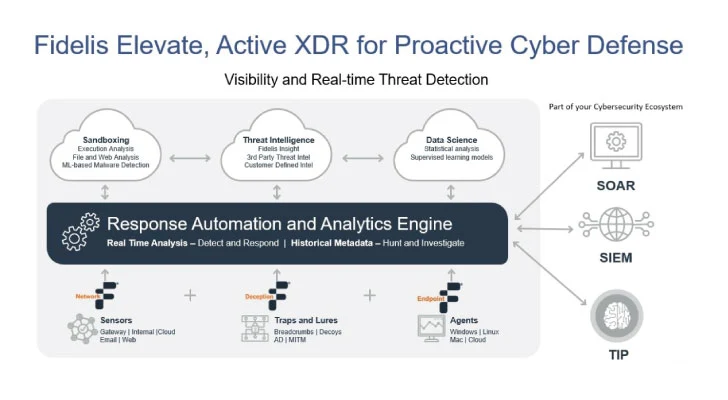
Fidelis Deception empowers you to make deception levels that are aligned with your true network infrastructure. These layers are created to establish and track malware and burglars as they try to move stealthily inside your network. By strategically inserting decoys and breadcrumbs, this solution aids in enhancing your network’s security posture. This solution permits you to attain heightened visibility and safeguard your assets, even in areas wherever traditional security brokers are not able to be deployed—such as in business IoT, Shadow IT, and legacy techniques. As a result, you can proactively pinpoint and neutralize threats inside your network, protecting against prospective harm to your group.
Lastly, the Fidelis Danger Investigate Group offers well timed intelligence in the variety of detection plan and risk intelligence feeds to each of these platforms to catch bad actors for the duration of the menace lifecycle and not following the reality. Any detections are presented to analysts in the Fidelis CommandPost so that they could initiate a swift response.
Mitigate
3. Vulnerability Management:
Vulnerability administration performs a critical purpose in lowering security risks. It requires identifying and addressing weaknesses in IT infrastructure. Fidelis Security’s Vulnerability Management alternatives give a strong approach to determining and prioritizing vulnerabilities proficiently, serving to businesses fortify their defenses.
Vulnerabilities in IT infrastructure can provide cybercriminals with entry points into systems. To counter this danger, Fidelis Security’s Vulnerability Administration alternatives empower companies to determine and prioritize vulnerabilities properly. By addressing weaknesses in infrastructure, they fortify their defenses and minimize security hazards, ultimately improving their cybersecurity posture.
4. Insider Threat Mitigation:
The menace of insider incidents, regardless of whether intentional or accidental, is a regarding obstacle. Mitigating these hazards is critical to enterprise continuity. Fidelis Security’s Information Decline Prevention (DLP) alternative is developed to handle insider threats by detecting strange things to do and safeguarding delicate details from unauthorized access.
Insider threats are a sophisticated problem that can have far-reaching outcomes. Fidelis DLP delivers a multifaceted strategy to mitigating these hazards, by safeguarding delicate info from unauthorized accessibility and exfiltration.
Answer
5. Incident Reaction and Recovery Planning:
Incident reaction and restoration plans are the lifelines in periods of a cyber disaster. Fidelis Security’s Incident Reaction solutions are their go-to useful resource for building and utilizing effective reaction plans, making certain swift and economical actions when needed most.
Incidents are a issue of ‘when’ rather than ‘if’ in the cybersecurity landscape. Becoming well prepared to respond swiftly and properly is important. Fidelis Security’s Incident Reaction options are built to support companies develop and carry out productive response plans. These plans are their lifeline in times of disaster, making sure that organizations can react swiftly and successfully to contain and mitigate the affect of cyber incidents.
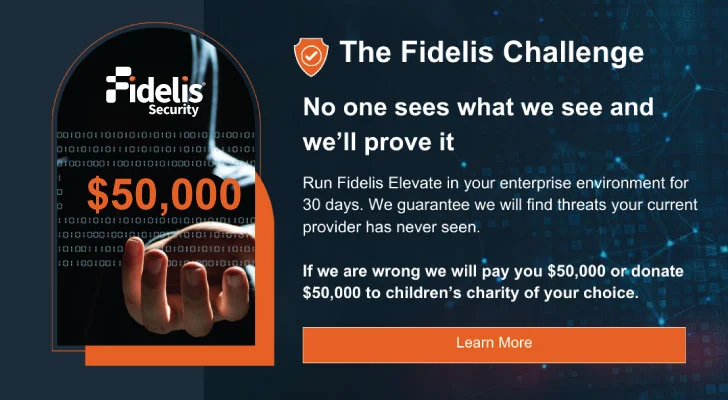
6. The Fidelis Challenge:
Fidelis Security provides know-how and determination to the forefront of cybersecurity. They firmly think that their standpoint on cyber threats is unmatched. To demonstrate this, corporations are invited to choose the Fidelis Challenge. For 30 days, they can combine Fidelis Elevate into your enterprise atmosphere, and Fidelis Security will showcase its unparalleled danger detection capabilities. Fidelis Security is self-assured that corporations will see the variance they can make in safeguarding their organizations. Test it for free of charge.
Conclusion
Cyber incidents have the likely to influence nationwide security, economic balance, and general public safety. Consequently, businesses need to prioritize the security of their critical infrastructure. The primary factors from this guidebook emphasize the great importance of robust cybersecurity actions for protecting seamless operations. Businesses are encouraged to concentrate on their cybersecurity attempts and leverage abilities to uncover the suitable tailored options for their security requires, thus enhancing their safety from ever-evolving threats.
Found this report intriguing? Follow us on Twitter and LinkedIn to browse a lot more unique information we put up.
Some parts of this article are sourced from:
thehackernews.com


 Google Expands Its Bug Bounty Program to Tackle Artificial Intelligence Threats
Google Expands Its Bug Bounty Program to Tackle Artificial Intelligence Threats