From a user’s perspective, OAuth performs like magic. In just a couple keystrokes, you can whisk as a result of the account development process and get quick obtain to whatsoever new app or integration you are seeking. Sadly, couple people comprehend the implications of the permissions they allow when they build a new OAuth grant, making it quick for malicious actors to manipulate workforce into giving away unintended entry to corporate environments. In one of the optimum-profile examples, Pawn Storm’s attacks against the Democratic Countrywide Conference and many others leveraged OAuth to concentrate on victims by social engineering.
Security and IT teams would be wise to establish a follow of reviewing new and existing OAuth grants programmatically to catch dangerous activity or overly-permissive scopes. And, there are new methods for SaaS security cropping up that can make this system easier.
Let us acquire a look at some greatest techniques for prioritizing and investigating your organization’s grants.
When really should you investigate an OAuth grant?
Businesses tactic OAuth grant evaluations in a number of various ways. Some decide to evaluate new OAuth grants in true-time, initiating a evaluate any time a consumer indicators up for a new application or connects an integration. An even greater follow would be to tailor your Google or Microsoft options to call for administrative acceptance for any new grant before staff can start out making use of it, supplying your workforce time to investigate and capture something suspicious.
Although reviewing new OAuth grants can assist you detect issues early on, oversight should not end the moment an OAuth grant is in put. It’s essential to retain OAuth security cleanliness by examining grants on an ongoing foundation to detect significant-risk exercise or drastic modifications. Month-to-month or quarterly, security and IT groups need to audit current OAuth grants, examine for modifications, and prune the grants that have not been applied.
Tailor your investigations by assessing OAuth scopes.
OAuth authentication will work by assigning accessibility tokens to third-social gathering programs that can act as a proxy for a user’s consent, and the scope of permissions granted can range broadly. You can prioritize your OAuth investigations by contemplating the scope of entry every grant gives.
Since distinctive scopes have diverse stages of risk to your group, you can vary the standards of your investigations based mostly on the permissions granted. Target more focus on grants with scopes that are far more likely to give entry to critical details, these kinds of as individually identifiable information (PII) or mental house, or grants that can make variations to an application.
And, you might want to look into applications that can assemble an stock of all OAuth grants for you, together with scopes and OAuth risk scores to make this approach less difficult.
Evaluate OAuth vendors and their reputations.
Evaluate no matter if or not the seller liable for issuing the OAuth grant is honest. For instance, you can assessment the vendor’s security site, look at their security certifications, and make guaranteed their security software follows ideal methods.
Selected reputational signals can assistance you understand the degree of rely on other companies have put in the grant. For example, Microsoft and Google both equally have programs for verifying the id of application publishers, which can give you more self-confidence in the grant. Nevertheless, attackers have managed to exploit verified publisher statuses in current assaults, so practitioners must take into account them a beneficial signal somewhat than a definitive evaluation of an app’s trustworthiness.
The recognition of a certain application, and of a certain grant, can give but another rely on indicator. If the grant just isn’t new to your group, you can contemplate its recognition inside of your very own workforce by using a seem at how quite a few of your individual staff are employing it and with what frequency. You can even increase this to the acceptance or range of installs outside the house of your corporation in the case that the OAuth application is existing in the Google market.
Look at the OAuth grant’s domains.
Prior to you can rely on a brand’s track record, you need to make positive that the grants stated actually belong to the vendor you happen to be striving to verify. Checking a grant’s domains can help you figure out irrespective of whether a seller essentially backs that distinct OAuth grant, or if the grant was created by anyone seeking to piggyback off of a authentic brand’s status.
For case in point, if the grant’s reply URL is calendly3.com, you should really make absolutely sure it’s basically a Calendly domain and not a malicious copycat. You need to investigate irrespective of whether the title of the grant matches the URL, and regardless of whether the domain has been authorised by Google.
Examine the publisher email.
You can attain extra insight into a grant’s legitimacy by seeking into the publisher email, which is the email tackle utilised to sign-up the shopper ID applied by the OAuth token.
Sometimes, an OAuth grant publisher will use a particular email address from a freemail supplier like Gmail, which may suggest some risk. If that is the scenario, you can glance into the track record of that email to comprehend the likelihood that it may well have been utilized for malicious intent. For case in point, make absolutely sure there are no compromised qualifications floating about that could enable a poor actor to just take in excess of the email account. Microsoft a short while ago warned of threat actors exploiting stolen Exchange On the internet accounts to spread spam applying malicious OAuth programs. The actors obtained original access to the stolen accounts utilizing credential stuffing attacks, which signifies compromised qualifications would have been an early indicator of risk.
Assess how the seller is accessing your natural environment.
Retaining an eye on how a seller accesses your natural environment can support you flag sudden adjustments and detect suspicious activity. For illustration, let’s say you make it possible for an OAuth grant to obtain your organization’s email. For three months, they accessibility it by calling Google Workspace APIs from Amazon AWS. Suddenly, you get a higher-risk API get in touch with from a absolutely unique infrastructure (TOR exit node, proxy network, VPS, and so on). Potentially the seller has been compromised, or possibly the application’s credentials have been stolen. If you’re checking activity connected to how these distributors are accessing your ecosystem, this type of modify can point out a possible problem.
Your organization’s skill to keep track of this exercise may possibly rely on the level of company you pay back for. For example, Google calls for a particular license to accessibility an activity stream that reveals what APIs are known as within your atmosphere, as properly as when and how they’re accessed. If you never fork out for the action stream and an incident takes place, you could be blind.
Microsoft, on the other hand, not long ago adjusted their stance on log accessibility by opting to make cloud logs obtainable to all customers fairly than only quality license holders. The adjust adopted strain from CISA and other folks following federal government email accounts at various organizations ended up hacked, which would not have been discoverable devoid of top quality logging readily available to at the very least a single of the influenced get-togethers.
Keep an eye on the security posture of your OAuth distributors.
As element of your ongoing monitoring, retain an eye out for significant-profile provide chain assaults that may perhaps have affected your OAuth vendors. If a service provider in your vendor’s provide chain activities a facts breach, could it compromise your own security posture?
Equally, look at the outcome of key vulnerabilities on the suppliers you depend on. When a widely exploited vulnerability like the ones found in Apache Log4j gets to be community, evaluate irrespective of whether any of the suppliers with OAuth entry to your environment could be influenced. Equally, you ought to fork out attention to vulnerabilities in just OAuth grants on their own, like the Microsoft “nOAuth” misconfiguration that can enable terrible actors to choose above impacted accounts. If you consider your sellers may perhaps be afflicted, you might pick to consider an action like revoking people grants until eventually you know that the vulnerability has been resolved.
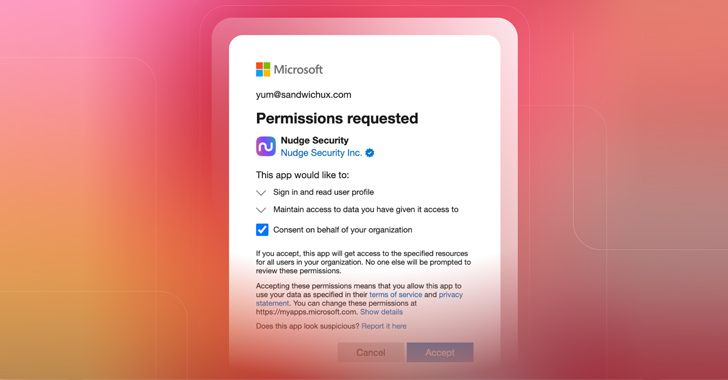
Investigate and revoke significant-risk OAuth grants with Nudge Security.
Nudge Security is a SaaS administration platform for modern IT governance and security. It gives comprehensive visibility of every SaaS and cloud asset ever made by any one in your org, which include OAuth grants. The platform delivers an stock of just about every app-to-application OAuth grant at any time produced in your org, together with OAuth risk insights like grant kind, age, variety of scopes, who granted accessibility, and an general OAuth risk score. With this visibility, consumers can conveniently perform OAuth critiques, assess risk, and even revoke OAuth grants with just two clicks. Try out it for absolutely free.
Take note: This post was expertly composed and contributed by Jaime Blasco, CTO and co-founder of Nudge Security.
Uncovered this article interesting? Stick to us on Twitter and LinkedIn to read much more exceptional material we article.
Some parts of this article are sourced from:
thehackernews.com

 This Malware Turned Thousands of Hacked Windows and macOS PCs into Proxy Servers
This Malware Turned Thousands of Hacked Windows and macOS PCs into Proxy Servers