Sandboxes are synonymous with dynamic malware assessment. They help to execute destructive information in a secure digital environment and notice their actions. Nonetheless, they also offer you a lot of benefit in terms of static investigation. See these 5 situations exactly where a sandbox can establish to be a practical device in your investigations.
Detecting Threats in PDFs
PDF documents are often exploited by danger actors to produce payloads. Static analysis in a sandbox tends to make it attainable to expose any menace a malicious PDF is made up of by extracting its framework.
The presence of JavaScript or Bash scripts can reveal a attainable system for downloading and executing malware.
Sandboxes like ANY.Run also will allow buyers to scrutinize URLs observed in PDFs to discover suspicious domains, probable command and control (C2) servers, or other indicators of compromise.
Case in point:
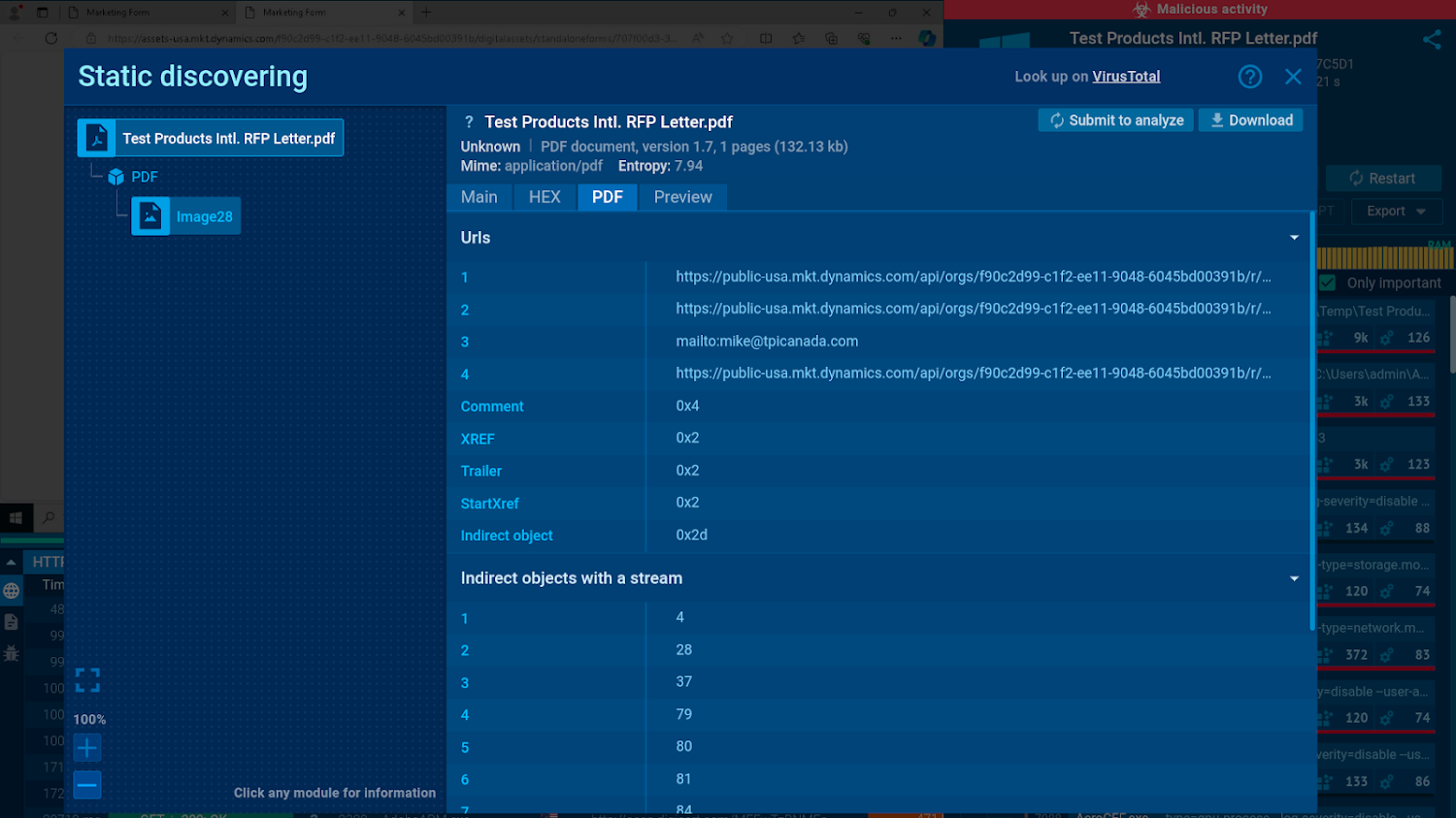 Static examination of a PDF file in ANY.Run
Static examination of a PDF file in ANY.Run
Interactivity lets our buyers to manipulate files in just a VM as they wish, but static Discovery presents even far more chances.
As part of this examination session, the static module lists quite a few URLs that can be uncovered inside the PDF. To investigate them, we can submit every of these for further sandbox analysis by simply just clicking a corresponding button.
See how static and dynamic evaluation in the ANY.Operate sandbox can benefit your security group.
E book a private demo of the service currently!
Exposing LNK Abuse
LNK information are shortcuts that immediate to an executable file, a document, or a folder. A sandbox can supply a clear watch of the LNK file’s homes, these kinds of as its focus on route, icon location, and any embedded commands or scripts.
Viewing instructions in LNK information can reveal attempts to launch malicious software or connect to distant servers.
Static investigation in a sandbox is notably helpful in pinpointing threats that do not spawn a new approach. These can be tricky to detect by way of dynamic investigation alone.
Illustration:
 The command line arguments shown in the static module reveal malicious action
The command line arguments shown in the static module reveal malicious action
Analyzing the contents of LNK data files can aid you detect assaults right before they start off.
In this sandbox session, we can discover just about every depth about the LNK file, like its command line arguments which show that the file is configured to down load and execute a payload from a malicious URL.
Investigating Spam and Phishing E-mail
Email stays just one of the most widespread vectors for malware distribution. A sandbox lets you upload an email file to the assistance and examine it safely to place spam and concealed malicious aspects quicker and with no any risk to your infrastructure.
A sandbox demonstrates an email preview and lists metadata and Indicators of Compromise (IOCs). You can take a look at the information of the email without the need of opening it and study the metadata that offers data about the email’s origin, timestamps, and other pertinent aspects.
The ANY.Run sandbox also integrates RSPAMD, an open-resource module that assigns a phishing score to every single analyzed email and displays all of its aspects applying these options:
- Header Examination: Examines email headers for sender authenticity and anomalies.
- Reputation Checks: Identifies known spam/malware sources utilizing DNSBLs and URIBLs.
- Bayesian Filtering: Classifies emails centered on probabilistic investigation.
In ANY.Operate, you can transfer outside of static evaluation and interact with the email instantly like you would on your own computer system. This suggests you can down load and open up attachments, which includes password-safeguarded kinds, or abide by by the complete phishing attack, starting from the initial backlink.
Case in point:
 Facts of an .eml file static analysis
Facts of an .eml file static analysis
All material inside of EMAIL files is extracted and manufactured obtainable by static examination in the sandbox, enabling customers to watch information about it even without having accessing the VM itself.
In this assessment session, we can notice a .RAR attachment which accompanies the email. Presented that 1 of the documents situated inside of of this archive is an executable named “Commercial Bill PDF”, we can promptly think its destructive nature.
To evaluate the executable, we can just click on the “Post to assess” button and start a new sandbox session.
Analyzing Suspicious Business Documents
Microsoft Workplace files, these kinds of as Word, Excel, and PowerPoint ones, are a single of the foremost security pitfalls in both of those company and own configurations. Sandbox static investigation can be utilized to scrutinize different aspects of these paperwork without having opening them. These consist of:
- Information: Sandbox static examination permits you to examine the document’s written content for signs of social engineering tactics, phishing tries, or suspicious hyperlinks.
- Macros: Attackers often exploit Visible Primary for Apps (VBA) code in Business files to automate destructive responsibilities. These tasks can variety from downloading and executing malware to stealing delicate facts. ANY.Run demonstrates the whole execution chain of the script, enabling you to examine it step by stage.
- Images and QR Codes: Steganography techniques allow attackers conceal code within just photographs. Sandbox static investigation is able of extracting this hidden data. QR codes embedded in documents may also contain malicious inbound links. A sandbox can decode these and expose the potential threats.
- Metadata: Info about the document’s development, modification, writer, etcetera. can assist you have an understanding of the document’s origin.
Case in point:
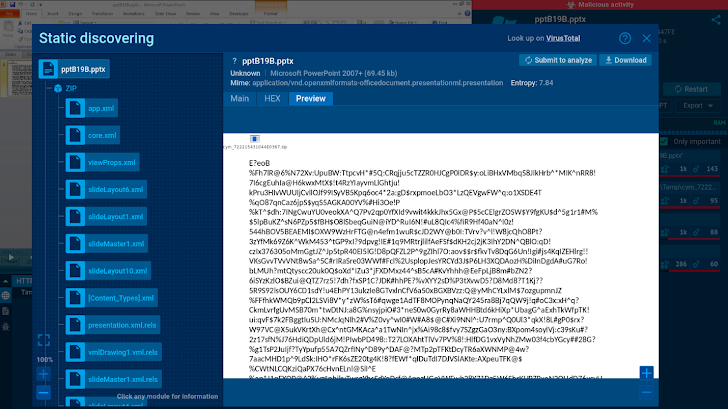 The sandbox can exhibit a preview of Office environment data files
The sandbox can exhibit a preview of Office environment data files
Microsoft Business office information occur in several formats, and analyzing their interior construction can from time to time be hard. Static Discovery for Office files enables you to analyze macros with out needing additional instruments.
All embedded information, which include images, scripts, and executable information, are also available for additional examination. QR codes are detected throughout static analysis, and buyers can post a new job that opens the written content encoded in these codes, these as URLs.
In this session, static evaluation helps make it attainable to see that the analyzed .pptx file incorporates a .zip archive.
Searching Within Destructive Archives
Archives like ZIP, tar.gz, .bz2, and RAR are usually utilised as signifies to bypass simple detection techniques. A sandbox surroundings delivers a safe and sound and isolated room to analyze these information.
For instance, sandboxes can unpack archives to reveal their contents, such as executable documents, scripts, and other possibly malicious components. These information can then be analyzed working with the designed-in static module to expose their threats.
Instance:
 ZIP file composition displayed in the static investigation window
ZIP file composition displayed in the static investigation window
In ANY.Operate, end users can submit data files for new evaluation specifically from archived data files from the static discovery window. This eliminates the will need to obtain or manually unpack them within a VM.
In this assessment session, we as soon as once again see an archive with documents that can be examined a person by just one to ascertain whether or not any further examination is necessary.
Carry out Static and Dynamic Analysis in ANY.Run
ANY.Operate is a cloud-primarily based sandbox with sophisticated static and dynamic evaluation capabilities. The service allows you scan suspicious data files and backlinks and get the to start with benefits on their danger degree in under 40 seconds. It offers you a authentic-time overview of the network website traffic, registry routines, and procedures happening throughout malware execution, highlighting destructive habits and the methods, methods, and treatments (TTPs).
ANY.Run offers you with finish management more than the VM, making it attainable to interact with the virtual setting just like on a normal laptop or computer. The sandbox generates in depth experiences that characteristic crucial risk info, which include indicators of compromise (IOCs).
Start off employing ANY.Operate these days for free of charge and love limitless malware evaluation in Windows and Linux VMs.
Discovered this posting fascinating? This short article is a contributed piece from a person of our valued partners. Stick to us on Twitter and LinkedIn to read through additional exclusive information we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Global Police Operation Disrupts ‘LabHost’ Phishing Service, Over 30 Arrested Worldwide
Global Police Operation Disrupts ‘LabHost’ Phishing Service, Over 30 Arrested Worldwide