
A new variant of AsyncRAT malware dubbed HotRat is becoming distributed by using no cost, pirated versions of popular software and utilities these kinds of as movie video games, impression and audio enhancing application, and Microsoft Business office.
“HotRat malware equips attackers with a extensive array of capabilities, this sort of as stealing login credentials, cryptocurrency wallets, display screen capturing, keylogging, putting in more malware, and gaining access to or altering clipboard details,” Avast security researcher Martin a Milánek explained.
The Czech cybersecurity firm stated the trojan has been commonplace in the wild because at minimum in Oct 2022, with a bulk of the infections concentrated in Thailand, Guyana, Libya, Suriname, Mali, Pakistan, Cambodia, South Africa, and India.
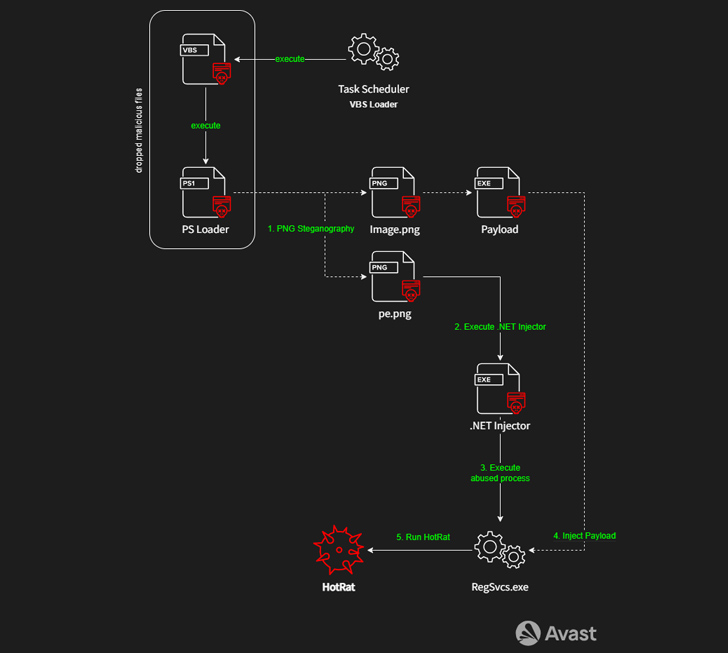
The attacks entail bundling the cracked software program out there on the internet by means of torrent sites with a destructive AutoHotkey (AHK) script that initiates an an infection chain designed to deactivate antivirus answers on the compromised host and in the end launch the HotRat payload making use of a Visual Standard Script loader.
Impending WEBINARShield From Insider Threats: Master SaaS Security Posture Management
Concerned about insider threats? We have got you coated! Sign up for this webinar to check out sensible tactics and the strategies of proactive security with SaaS Security Posture Management.
Sign up for Nowadays
HotRat, described as a detailed RAT malware, comes with just about 20 instructions, every of which executes a .NET module retrieved from a remote server, enabling the risk actors at the rear of the marketing campaign to extend its characteristics as and when necessary.
That explained, it’s well worth noting that the attack needs administrative privileges to properly realize its ambitions.
“Regardless of the sizeable hazards involved, the irresistible temptation to get significant-quality computer software at no expense persists, leading a lot of men and women to obtain unlawful application,” Milánek explained. “Hence, distributing these kinds of computer software continues to be an productive technique for greatly spreading malware.”
Found this posting appealing? Observe us on Twitter and LinkedIn to examine additional distinctive material we put up.
Some parts of this article are sourced from:
thehackernews.com


 Sophisticated BundleBot Malware Disguised as Google AI Chatbot and Utilities
Sophisticated BundleBot Malware Disguised as Google AI Chatbot and Utilities