Humans are elaborate beings with consciousness, thoughts, and the potential to act primarily based on feelings. In the ever-evolving realm of cybersecurity, humans regularly keep on being major targets for attackers. About the many years, these attackers have created their abilities in exploiting several human features, sharpening their competencies to manipulate biases and emotional triggers with the aim of influencing human conduct to compromise security regardless of whether it be personalized and organisational security.
Additional than just a ‘human factor’
Understanding what defines our humanity, recognizing how our features can be perceived as vulnerabilities, and comprehending how our minds can be specific offer the basis for determining and responding when we inevitably grow to be the focus on.
The human brain is a elaborate landscape that developed in excess of yrs of publicity to the pure setting, interactions with many others, and lessons drawn from past ordeals.
As people, our minds set us aside, marked by a multitude of features and emotions, normally as well complex to articulate precisely.
Human conduct is intricate
Some of our fundamental characteristics can be outlined as follows:
- Belief – Humans put their have confidence in in other people, assuming inherent goodness.
- Empathy – Humans exhibit treatment for some others and their thoughts.
- Ego – Human beings harbour a competitive spirit, aspiring to outshine their friends.
- Guilt – Human beings practical experience regret for their actions, specifically when they damage others.
- Greed – Humans desire possessions and may well succumb to impulsivity.
- Urgency – People reply immediately to cases demanding immediate awareness.
- Vulnerability – Human beings typically grapple with anxiety and are candid about their emotions.
When this record is not exhaustive, it summarises common and easy to understand areas that drive human behaviour. Human interactions maintain critical price, instilling life with importance and advancing cultural norms. Even so, for attackers looking for to exploit us, the social build of human-to-human interactions presents a pathway for manipulation.
Our the natural way social character forces us to revert to these traits. Emotions serve as a basic safety net for conversation, problem-resolving, and connections in our everyday everyday living and we have arrive to belief our psychological responses to even more tutorial and secure us in a variety of cases.
I imagine, as a result I can be manipulated
Attackers exploit this basic safety net (emotions and basic attributes) when concentrating on people, as it can be manipulated to fulfil their objectives. This protection net weakens even additional when we venture into the “online” realm, as sure safeguards fail due to a lack of insight. The abstraction of communication through a identify on display normally misleads our minds in deciphering situations in a way that our emotions are not able to precisely navigate.
In the realm of manipulation, several models and solutions have been employed more than centuries to influence human conduct. In modern context, attackers exploit these models to identify human vulnerabilities, characterised as weaknesses inside the system that can be exploited.
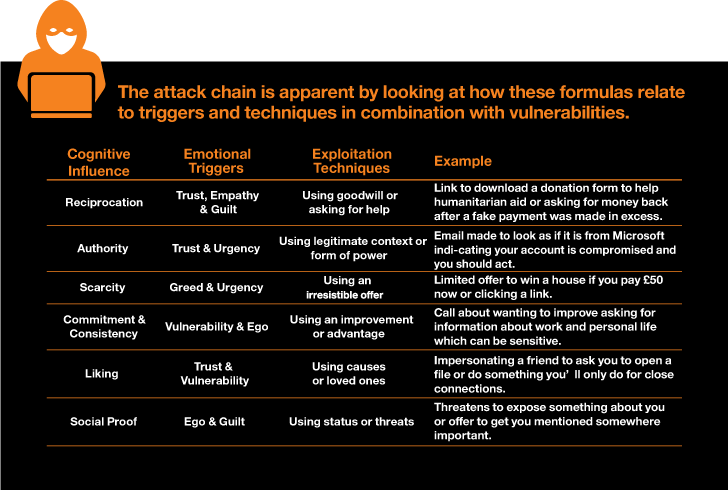
In addition to specifically manipulating essential characteristics by way of diligently specific attacks, attackers are inclined to goal people through types of impact and persuasion. These can be summarised as follows, and individuals are inclined to run mentally in these realms:
- Reciprocation – Human beings come to feel compelled to reciprocate what they have been given.
- Authority – Human beings are inclined to comply with authoritative/acknowledged figures.
- Shortage – People want things that are fewer attainable.
- Determination & Consistency – Individuals favour plan and composition.
- Liking – Individuals form psychological connections.
- Social Evidence – Individuals seek out validation and fame.
These features can be seen as prospective vulnerabilities in the human brain when mixed with thoughts and fundamental features. Attackers leverage these elements to get immediate command about our actions, an occurrence now recognised as social engineering. Social engineering encompasses many strategies and ways, nonetheless at its core, it exploits one particular or more of the spots pointed out higher than by means of accurately crafted interactions.

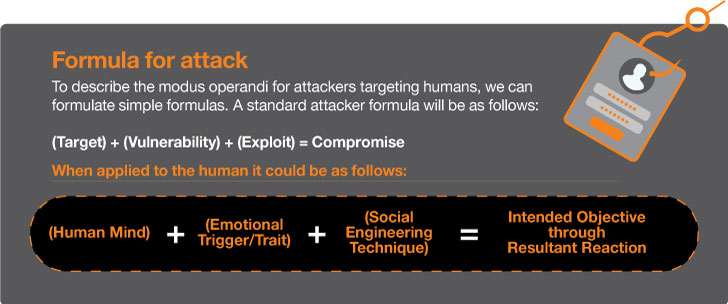
Exploitation strategies, usually found in digital channels like email, phone calls, or textual content messages, are commonly employed for phishing. These tactics manipulate recognized interactions to reach several targets, these types of as deceiving persons into parting with money, opening malicious data files, distributing credentials, or revealing sensitive info. The implications of these assaults can range from unique losses to organizational breaches.
Defending ourselves
To safeguard against these attacks towards our minds, we really should align our cognitive requirements with psychological triggers by asking inquiries like what is the goal, expectation, and legitimacy of the conversation. These inquiries could stop impulsive reactions and make it possible for introspection.
Setting up a “stop and evaluate” mentality acts as a mental firewall, strengthened by vigilance, to enrich personal and organisational security. By contemplating likely assaults, we heighten our consciousness of vulnerabilities and work on resilience. This recognition, coupled with a proactive approach, helps mitigate threats to our minds and humanity, advertising and marketing collaboration to disarm attackers and weaken their operations.
Keep vigilant, keep educated, and go on to problem everything.
This is just one particular of the stories identified in the Security Navigator. Other interesting analysis like a study of Hacktivism and an examination of the surge in Cyber Extortion (as properly as a ton of other intriguing study matters) can be uncovered there as nicely. It truly is no cost of charge, so have a seem. It can be truly worth it!
Note: This article was expertly published by Ulrich Swart, Coaching Manager & Complex Staff Chief at Orange Cyberdefense.
Identified this posting intriguing? Comply with us on Twitter and LinkedIn to study additional distinctive content we article.
Some parts of this article are sourced from:
thehackernews.com

 Building a Robust Threat Intelligence with Wazuh
Building a Robust Threat Intelligence with Wazuh