A new cyber attack marketing campaign has been noticed making use of spurious MSIX Windows application package deal documents for common software program this sort of as Google Chrome, Microsoft Edge, Brave, Grammarly, and Cisco Webex to distribute a novel malware loader dubbed GHOSTPULSE.
“MSIX is a Windows application bundle structure that builders can leverage to package, distribute, and install their programs to Windows customers,” Elastic Security Labs researcher Joe Desimone mentioned in a technological report printed final week.
“On the other hand, MSIX needs entry to ordered or stolen code signing certificates earning them practical to teams of over-ordinary resources.”

Centered on the installers utilized as lures, it really is suspected that opportunity targets are enticed into downloading the MSIX offers by way of recognized tactics these kinds of as compromised internet sites, research motor optimization (Search engine optimisation) poisoning, or malvertising.
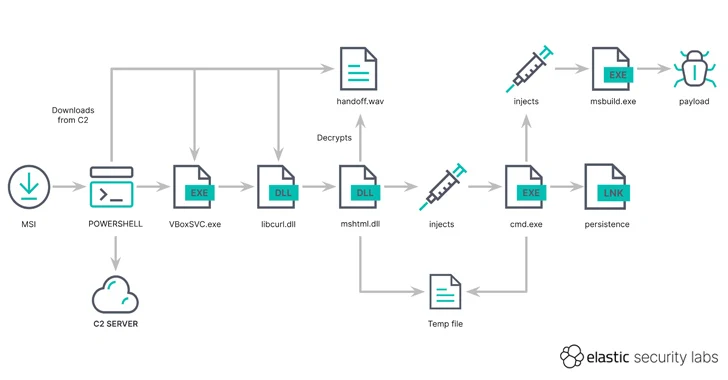
Launching the MSIX file opens a Windows prompting the customers to click on the Set up button, accomplishing so which success in the stealthy obtain of GHOSTPULSE on the compromised host from a distant server (“manojsinghnegi[.]com”) through a PowerShell script.
This method acquire position around multiple stages, with the first payload remaining a TAR archive file that contains an executable that masquerades as the Oracle VM VirtualBox provider (VBoxSVC.exe) but in truth is a legit binary that’s bundled with Notepad++ (gup.exe).
Also current inside the TAR archive is handoff.wav and a trojanized edition of libcurl.dll that’s loaded to get the an infection procedure to the future stage by exploiting the truth that gup.exe is susceptible to DLL aspect-loading.

“The PowerShell executes the binary VBoxSVC.exe that will facet load from the present directory the destructive DLL libcurl.dll,” Desimone reported. “By reducing the on-disk footprint of encrypted destructive code, the menace actor is equipped to evade file-based AV and ML scanning.”
The tampered DLL file subsequently proceeds by parsing handoff.wav, which, in transform, packs an encrypted payload which is decoded and executed through mshtml.dll, a technique recognised as module stomping, to in the long run load GHOSTPULSE.
GHOSTPULSE acts as a loader, employing a further approach regarded as procedure doppelgänging to kick start out the execution of the last malware, which consists of SectopRAT, Rhadamanthys, Vidar, Lumma, and NetSupport RAT.
Located this posting appealing? Stick to us on Twitter and LinkedIn to read through extra unique content we submit.
Some parts of this article are sourced from:
thehackernews.com

 Researchers Uncover Wiretapping of XMPP-Based Instant Messaging Service
Researchers Uncover Wiretapping of XMPP-Based Instant Messaging Service