Italian corporate banking purchasers are the focus on of an ongoing economical fraud campaign that has been leveraging a new web-inject toolkit named drIBAN considering that at minimum 2019.
“The key goal of drIBAN fraud operations is to infect Windows workstations inside of corporate environments striving to alter genuine banking transfers executed by the victims by shifting the beneficiary and transferring income to an illegitimate lender account,” Cleafy scientists Federico Valentini and Alessandro Strino mentioned.
The bank accounts, for every the Italian cybersecurity firm, are possibly controlled by the menace actors by themselves or their affiliate marketers, who are then tasked with laundering the stolen cash.
The use of web injects is a time-tested tactic that helps make it achievable for malware to inject customized scripts on the shopper side by means of a man-in-the-browser (MitB) attack and intercept website traffic to and from the server.

The fraudulent transactions are normally recognized by means of a strategy known as Automated Transfer Technique (ATS) which is capable of bypassing anti-fraud devices set in put by financial institutions and initiating unauthorized wire transfers from a victim’s personal computer.
Over the several years, the operators guiding drIBAN have gotten far more savvy at staying away from detection and producing powerful social engineering approaches, in addition to establishing a foothold for very long periods in company lender networks.
Cleafy claimed 2021 was the year when the basic “banking trojan” operation evolved into an superior persistent threat. Additionally, there are indications that the action cluster overlaps with a 2018 marketing campaign mounted by an actor tracked by Proofpoint as TA554 targeting consumers in Canada, Italy, and the U.K.
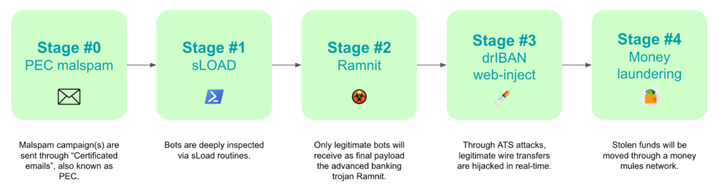
The attack chain starts with a qualified email (or PEC email) in an attempt to lull victims into a fake sense of security. These phishing e-mail arrive bearing an executable file that acts as a downloader for a malware known as sLoad (aka Starslord loader).
A PowerShell loader, sLoad is a reconnaissance software that collects and exfiltrates details from the compromised host, with the goal of examining the concentrate on and dropping a much more major payload like Ramnit if the target is considered rewarding.
“This ‘enrichment phase’ could continue for times or weeks, based on the quantity of infected equipment,” Cleafy pointed out. “Further knowledge will be exfiltrated to make the resulting botnet much more and a lot more stable and constant.”
Upcoming WEBINARLearn to Quit Ransomware with True-Time Defense
Be a part of our webinar and learn how to quit ransomware assaults in their tracks with serious-time MFA and assistance account protection.
Preserve My Seat!
sLoad also leverages residing-off-the-land (LotL) methods by abusing legit Windows equipment like PowerShell and BITSAdmin as part of its evasion mechanisms.
Yet another attribute of the malware is its capacity to look at against a predefined record of corporate banking establishments to establish if the hacked workstation is one particular among the targets, and if so, continue with the infection.
“All the bots that productively pass those people measures will be chosen by botnet operators and thought of as ‘new candidates’ for banking fraud functions shifting forward to the future stage, where by Ramnit, a single of the most superior banking trojans, will be set up,” the scientists claimed.
Located this posting exciting? Observe us on Twitter and LinkedIn to read extra unique articles we submit.
Some parts of this article are sourced from:
thehackernews.com


 Subscription Trojan Downloaded 600K Times From Google Play
Subscription Trojan Downloaded 600K Times From Google Play