Human legal rights activists in Morocco and the Western Sahara location are the targets of a new risk actor that leverages phishing attacks to trick victims into setting up bogus Android applications and serve credential harvesting internet pages for Windows users.
Cisco Talos is tracking the activity cluster beneath the identify Starry Addax, describing it as mostly singling out activists linked with the Sahrawi Arab Democratic Republic (SADR).
Starry Addax’s infrastructure – ondroid[.]web-site and ondroid[.]shop – is created to concentrate on each Android and Windows end users, with the latter involving phony internet sites masquerading as login webpages for well-known social media web-sites.

The adversary, thought to be active given that January 2024, is recognized to ship spear-phishing email messages to targets, urging recipients to put in Sahara Push Service’s cell application or a appropriate decoy linked to the location.
Based on the running technique from wherever the request is originating from, the focus on is either served a malicious APK that impersonates the Sahara Press Provider or redirected to a social media login site to harvest their credentials.
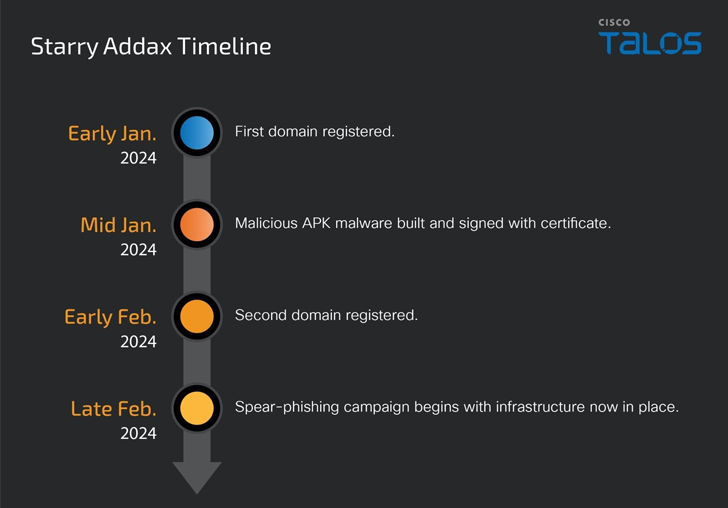
The novel Android malware, dubbed FlexStarling, is functional and equipped to provide more malware elements and steal sensitive data from infected units.
At the time installed, it requests the victim to grant it extensive permissions that let the malware to conduct nefarious actions, including fetching commands to be executed from a Firebase-based mostly command-and-control (C2), a sign that the risk actor is wanting to fly less than the radar.
“Strategies like this that concentrate on significant-worth people today usually intend to sit quietly on the unit for an prolonged time period,” Talos explained.

“All factors from the malware to the operating infrastructure seem to be to be bespoke/custom made-created for this unique campaign indicating a weighty emphasis on stealth and conducting pursuits below the radar.”
The advancement will come amid the emergence of a new industrial Android remote accessibility trojan (RAT) recognized as Oxycorat that’s getting made available for sale with numerous information and facts gathering abilities.
Identified this write-up intriguing? Stick to us on Twitter and LinkedIn to read through a lot more exceptional information we post.
Some parts of this article are sourced from:
thehackernews.com


 Researchers Discover LG Smart TV Vulnerabilities Allowing Root Access
Researchers Discover LG Smart TV Vulnerabilities Allowing Root Access