Misconfigured and inadequately secured Apache Tomcat servers are currently being focused as portion of a new campaign intended to provide the Mirai botnet malware and cryptocurrency miners.
The findings arrive courtesy of Aqua, which detected more than 800 attacks from its Tomcat server honeypots more than a two-yr time period, with 96% of the assaults joined to the Mirai botnet.
Of these attack makes an attempt, 20% (or 152) entailed the use of a web shell script dubbed “neww” that originated from 24 one of a kind IP addresses, with 68% of them originating from a single IP tackle (104.248.157[.]218).
“The danger actor scanned for Tomcat servers and launched a brute power attack from it, attempting to gain access to the Tomcat web software supervisor by trying various mixtures of credentials associated with it,” Aqua security researcher Nitzan Yaakov mentioned.
Upon getting a thriving foothold, the threat actors have been observed deploying a WAR file that contains a destructive web shell course named ‘cmd.jsp’ that, in flip, is made to listen to distant requests and execute arbitrary commands on the Tomcat server.
This contains downloading and working a shell script identified as “neww” right after which the file is deleted employing the “rm -rf” Linux command.
“The script consists of one-way links to download 12 binary information, and each individual file is suitable for a particular architecture in accordance to the method that has been attacked by the danger actor,” Yaakov pointed out.
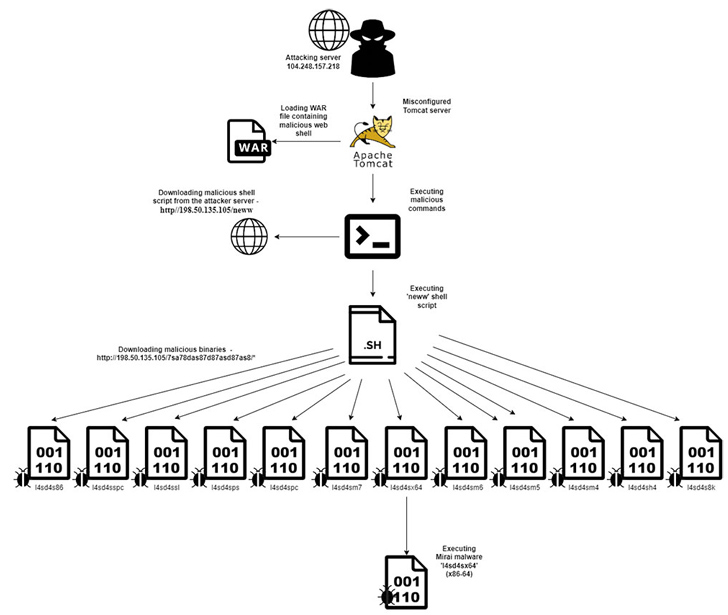
The closing phase malware is a variant of the infamous Mirai botnet that will make use of the infected hosts to orchestrate dispersed denial-of-support (DDoS) assaults.
“At the time the risk actor attained access to the web software supervisor utilizing legitimate qualifications, they leveraged the platform to add a web shell disguised in a WAR file,” Yaakov explained. “Following, the threat actor executed commands remotely and launched the attack.”
Impending WEBINARShield Versus Insider Threats: Learn SaaS Security Posture Administration
Anxious about insider threats? We’ve got you lined! Be part of this webinar to take a look at realistic strategies and the secrets of proactive security with SaaS Security Posture Management.
Be part of Currently
To mitigate in opposition to the ongoing marketing campaign, it’s advised that organizations secure their environments and abide by credential hygiene to avoid brute-pressure attacks.
The advancement arrives as the AhnLab Security Crisis Response Center (ASEC) described that inadequately managed MS-SQL servers are getting breached to deploy a rootkit malware identified as Purple Fox, which acts as a loader to fetch further malware these types of as coin miners.
These conclusions also show the lucrative mother nature of cryptocurrency mining, which has witnessed a 399% raise in excess of very last 12 months, with 332 million cryptojacking assaults recorded in the initial 50 percent of 2023 globally, in accordance to SonicWall.
Located this write-up appealing? Observe us on Twitter and LinkedIn to browse extra exceptional articles we submit.
Some parts of this article are sourced from:
thehackernews.com

 Group-IB Co-Founder Sentenced to 14 Years in Russian Prison for Alleged High Treason
Group-IB Co-Founder Sentenced to 14 Years in Russian Prison for Alleged High Treason