Indian authorities entities and vitality firms have been focused by not known menace actors with an intention to deliver a modified model of an open-resource info stealer malware called HackBrowserData and exfiltrate sensitive facts in some scenarios by applying Slack as command-and-control (C2).
“The details stealer was shipped via a phishing email, masquerading as an invitation letter from the Indian Air Pressure,” EclecticIQ researcher Arda Büyükkaya stated in a report posted currently.
“The attacker used Slack channels as exfiltration details to add private interior documents, non-public email messages, and cached web browser details immediately after the malware’s execution.”
The marketing campaign, noticed by the Dutch cybersecurity agency commencing March 7, 2024, has been codenamed Procedure FlightNight in reference to the Slack channels operated by the adversary.

Targets of the destructive activity span multiple authorities entities in India, counting these related to digital communications, IT governance, and countrywide defense.
The danger actor is explained to have successfully compromised non-public energy providers, harvesting money documents, individual facts of workers, information about drilling pursuits in oil and gas. In all, about 8.81 GB of facts has been exfiltrated over the system of the marketing campaign.
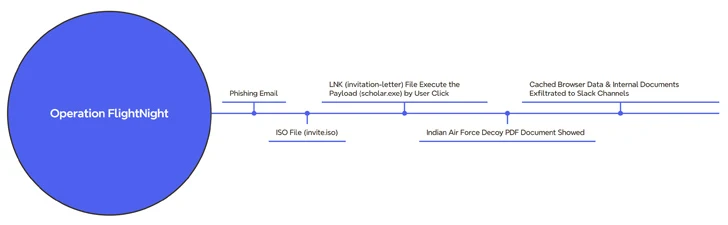
The attack chain commences with a phishing message that contains an ISO file (“invite.iso”), which, in turn, includes a Windows shortcut (LNK) that triggers the execution of a hidden binary (“scholar.exe”) present within the mounted optical disk image.
Concurrently, a lure PDF file that purports to be an invitation letter from the Indian Air Pressure is exhibited to the victim when the malware clandestinely harvests documents and cached web browser knowledge and transmits them to an actor-controlled Slack channel named FlightNight.
The malware is an altered model of HackBrowserData that goes over and above its browser info theft attributes to integrate capabilities to siphon documents (Microsoft Business, PDFs, and SQL database information), talk above Slack, and greater evade detection utilizing obfuscation techniques.

It is really suspected that the menace actor stole the decoy PDF in the course of a earlier intrusion, with behavioral similarities traced again to a phishing marketing campaign concentrating on the Indian Air Pressure with a Go-centered stealer called GoStealer.
Facts of the exercise had been disclosed by an Indian security researcher who goes by the alias xelemental (@ElementalX2) in mid-January 2024.
The GoStealer an infection sequence is nearly similar to that FlightNight, utilizing procurement-themed lures (“SU-30 Aircraft Procurement.iso”) to show a decoy file even though the stealer payload is deployed to exfiltrate details of curiosity about Slack.
By adapting freely obtainable offensive resources and repurposing authentic infrastructure these types of as Slack which is commonplace in business environments, it allows menace actors to lower time and progress fees, as nicely as very easily fly less than the radar.
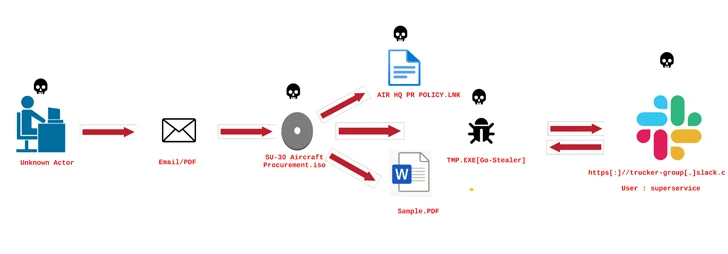 Image supply: ElementalX2
Image supply: ElementalX2
The effectiveness rewards also imply that it can be that considerably easier to start a targeted attack, even allowing considerably less-skilled and aspiring cybercriminals to spring into motion and inflict considerable hurt to companies.
“Procedure FlightNight and the GoStealer campaign spotlight a uncomplicated however powerful approach by menace actors to use open-source equipment for cyber espionage,” Büyükkaya claimed.
“This underscores the evolving landscape of cyber threats, wherein actors abuse broadly used open up-supply offensive tools and platforms to obtain their objectives with negligible risk of detection and expense.”
Identified this short article appealing? Stick to us on Twitter and LinkedIn to study extra special material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 CISA Warns: Hackers Actively Attacking Microsoft SharePoint Vulnerability
CISA Warns: Hackers Actively Attacking Microsoft SharePoint Vulnerability