As numerous as 200,000 WordPress web-sites are at risk of ongoing assaults exploiting a critical unpatched security vulnerability in the Greatest Member plugin.
The flaw, tracked as CVE-2023-3460 (CVSS score: 9.8), impacts all variations of the Best Member plugin, together with the most up-to-date variation (2.6.6) that was released on June 29, 2023.
Ultimate Member is a preferred plugin that facilitates the development of user-profiles and communities on WordPress sites. It also gives account administration features.
“This is a incredibly really serious issue: unauthenticated attackers could exploit this vulnerability to make new consumer accounts with administrative privileges, giving them the electrical power to choose total management of influenced sites,” WordPress security organization WPScan stated in an inform.

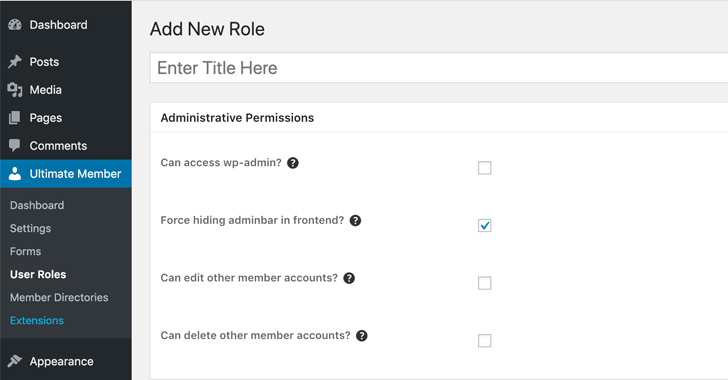
Despite the fact that specifics about the flaw have been withheld because of to lively abuse, it stems from an insufficient blocklist logic put in location to change the wp_abilities consumer meta value of a new user to that of an administrator and achieve complete obtain to the site.
“While the plugin has a preset defined listing of banned keys, that a person must not be ready to update, there are trivial approaches to bypass filters set in location these kinds of as using various conditions, slashes, and character encoding in a equipped meta crucial worth in susceptible versions of the plugin,” Wordfence researcher Chloe Chamberland mentioned.
The issue came to light-weight immediately after studies emerged of rogue administrator accounts becoming included to the afflicted web-sites, prompting the plugin maintainers to issue partial fixes in variations 2.6.4, 2.6.5, and 2.6.6. A new update is envisioned to be introduced in the coming days.
“A privilege escalation vulnerability applied as a result of UM Types,” Best Member mentioned in its release notes. “Identified in the wild that vulnerability allowed strangers to make administrator-stage WordPress people.”

WPScan, having said that, pointed out that the patches are incomplete and that it found numerous procedures to circumvent them, this means the issue is nonetheless actively exploitable.
In the noticed attacks, the flaw is becoming applied to sign-up new accounts under the names apadmins, se_brutal, segs_brutal, wpadmins, wpengine_backup, and wpenginer to upload destructive plugins and themes by way of the site’s administration panel.
People of Final Member are advised to disable the plugin until a right patch that entirely plugs the security hole is made offered. It is also suggested to audit all administrator-level buyers on the sites to decide if any unauthorized accounts have been included.
Identified this posting fascinating? Comply with us on Twitter and LinkedIn to browse more unique information we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Beware: New ‘Rustbucket’ Malware Variant Targeting macOS Users
Beware: New ‘Rustbucket’ Malware Variant Targeting macOS Users