Security vulnerabilities in remote desktop plans these kinds of as Sunlogin and AweSun are staying exploited by menace actors to deploy the PlugX malware.
AhnLab Security Unexpected emergency Reaction Heart (ASEC), in a new analysis, mentioned it marks the ongoing abuse of the flaws to produce a wide range of payloads on compromised units.
This features the Sliver post-exploitation framework, XMRig cryptocurrency miner, Gh0st RAT, and Paradise ransomware. PlugX is the newest addition to this checklist.
The modular malware has been thoroughly place to use by danger actors dependent in China, with new options continuously included to help perform technique regulate and data theft.
In the assaults observed by ASEC, effective exploitation of the flaws is followed by the execution of a PowerShell command that retrieves an executable and a DLL file from a distant server.
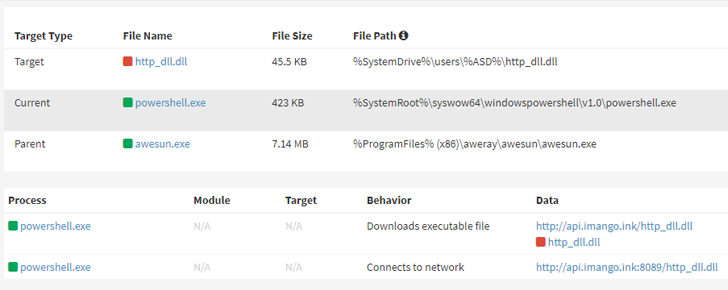
This executable is a authentic HTTP Server Service from cybersecurity organization ESET, which is employed to load the DLL file by implies of a method termed DLL aspect-loading and in the long run operate the PlugX payload in memory.
“PlugX operators use a substantial wide variety of trusted binaries which are vulnerable to DLL Facet-Loading, which include a lot of anti-virus executables,” Security Joes famous in a September 2022 report. “This has been confirmed to be powerful although infecting victims.”
WEBINARDiscover the Concealed Dangers of 3rd-Occasion SaaS Apps
Are you aware of the challenges associated with 3rd-party application accessibility to your firm’s SaaS apps? Be part of our webinar to learn about the varieties of permissions currently being granted and how to decrease risk.
RESERVE YOUR SEAT
The backdoor is also noteworthy for its ability to commence arbitrary providers, obtain and execute data files from an exterior resource, and drop plugins that can harvest info and propagate using Remote Desktop Protocol (RDP).
“New functions are staying extra to [PlugX] even to this day as it proceeds to see regular use in attacks,” ASEC reported. “When the backdoor, PlugX, is installed, threat actors can achieve control in excess of the contaminated system with out the know-how of the user.”
Identified this post appealing? Observe us on Twitter and LinkedIn to browse far more distinctive content we post.
Some parts of this article are sourced from:
thehackernews.com


 Proposed quantum device may succinctly realize emergent particles such as the Fibonacci anyon
Proposed quantum device may succinctly realize emergent particles such as the Fibonacci anyon