Risk actors are leveraging digital doc publishing (DDP) web pages hosted on platforms like FlipSnack, Issuu, Marq, Publuu, RelayTo, and Simplebooklet for carrying out phishing, credential harvesting, and session token theft, once once again underscoring how menace actors are repurposing legitimate providers for destructive ends.
“Hosting phishing lures on DDP sites improves the likelihood of a thriving phishing attack, due to the fact these websites typically have a favorable status, are not likely to surface on web filter blocklists, and could instill a phony perception of security in consumers who figure out them as common or legitimate,” Cisco Talos researcher Craig Jackson reported final 7 days.
When adversaries have applied well-liked cloud-based mostly companies these types of as Google Push, OneDrive, Dropbox, SharePoint, DocuSign, and Oneflow to host phishing files in the past, the most current development marks an escalation built to evade email security controls.

DDP products and services allow customers to add and share PDF files in a browser-primarily based interactive flipbook structure, introducing page flip animations and other skeuomorphic results to any catalog, brochure, or magazine.
Danger actors have been discovered to abuse the absolutely free tier or a no-cost demo period of time provided by these expert services to make numerous accounts and publish malicious paperwork.
Moreover exploiting their favorable domain standing, the attackers take gain of the reality that DDP sites aid transient file hosting, therefore letting printed content material to routinely turn into unavailable following a predefined expiration date and time.
What’s far more, productivity capabilities baked into DDP websites like Publuu could act as a deterrent, avoiding the extraction and detection of destructive backlinks in phishing messages.
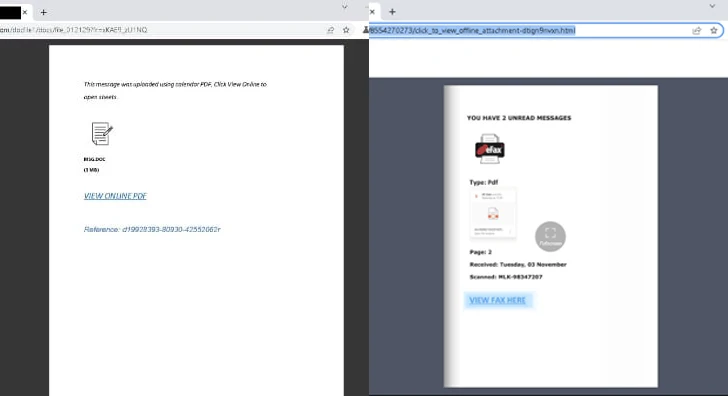
In the incidents analyzed by Cisco Talos, DDP websites are integrated into the attack chain in the secondary or intermediate stage, typically by embedding a hyperlink to a document hosted on a authentic DDP web-site in a phishing email.
The DDP-hosted document serves as a gateway to an exterior, adversary-managed site either instantly by clicking on a connection involved in the decoy file, or via a series of redirects that also demand fixing CAPTCHAs to thwart automatic evaluation efforts.

The last landing website page is a bogus web-site mimicking the Microsoft 365 login web page, as a result letting the attackers to steal qualifications or session tokens.
“DDP websites could stand for a blind location for defenders, because they are unfamiliar to educated buyers and not likely to be flagged by email and web material filtering controls,” Jackson explained.
“DDP sites generate rewards for menace actors seeking to thwart contemporary phishing protections. The exact same functions and advantages that draw in respectable consumers to these web pages can be abused by menace actors to enhance the efficacy of a phishing attack.”
Identified this short article intriguing? Observe us on Twitter and LinkedIn to read through more exclusive written content we post.
Some parts of this article are sourced from:
thehackernews.com


 Suspected Russian Data-Wiping ‘AcidPour’ Malware Targeting Linux x86 Devices
Suspected Russian Data-Wiping ‘AcidPour’ Malware Targeting Linux x86 Devices