Attackers are weaponizing an aged Microsoft Place of work vulnerability as aspect of phishing strategies to distribute a strain of malware known as Agent Tesla.
The an infection chains leverage decoy Excel paperwork attached in invoice-themed messages to trick potential targets into opening them and activate the exploitation of CVE-2017-11882 (CVSS rating: 7.8), a memory corruption vulnerability in Office’s Equation Editor that could end result in code execution with the privileges of the person.
The results, which appear from Zscaler ThreatLabz, create on prior experiences from Fortinet FortiGuard Labs, which detailed a similar phishing campaign that exploited the security flaw to supply the malware.
“When a consumer downloads a destructive attachment and opens it, if their edition of Microsoft Excel is vulnerable, the Excel file initiates conversation with a malicious vacation spot and proceeds to down load further documents without having demanding any additional consumer conversation,” security researcher Kaivalya Khursale stated.
The first payload is an obfuscated Visual Standard Script, which initiates the download of a destructive JPG file that arrives embedded with a Foundation64-encoded DLL file. This steganographic evasion tactic was formerly also specific by McAfee Labs in September 2023.
Approaching WEBINAR Conquer AI-Powered Threats with Zero Rely on – Webinar for Security Gurus
Traditional security actions will never slash it in present-day globe. It’s time for Zero Belief Security. Protected your data like by no means just before.
Sign up for Now
The hid DLL is subsequently injected into RegAsm.exe, the Windows Assembly Registration Tool, to start the final payload. It really is value noting that the executable has also been abused to load Quasar RAT in the past.
Agent Tesla is a .NET-dependent advanced keylogger and distant accessibility trojan (RAT) that is geared up to harvest delicate information and facts from compromised hosts. The malware then communicates with a remote server to extract the gathered data.
“Risk actors frequently adapt infection approaches, building it very important for businesses to keep current on evolving cyber threats to safeguard their electronic landscape,” Khursale reported.
The improvement arrives as aged security flaws become new attack targets for danger actors. Before this week, Imperva discovered that a three-year-old flaw in Oracle WebLogic Server (CVE-2020-14883, CVSS score: 7.2) is currently being used by the 8220 Gang to produce cryptocurrency miners.
It also coincides with an uptick in DarkGate malware exercise right after it started to be marketed before this year as a malware-as-a-support (MaaS) offering and as a substitution for QakBot subsequent its takedown back again in August 2023.
“The technology sector is the most impacted by DarkGate attack campaigns,” Zscaler mentioned, citing customer telemetry facts.
“Most DarkGate domains are 50 to 60 times outdated, which might indicate a deliberate strategy the place risk actors produce and rotate domains at precise intervals.”

Phishing strategies have also been learned targeting the hospitality sector with reserving-connected email messages to distribute information stealer malware these kinds of as RedLine Stealer or Vidar Stealer, in accordance to Sophos.
“They in the beginning make contact with the concentrate on above email that consists of very little but text, but with issue matter a assistance-oriented enterprise (like a hotel) would want to answer to rapidly,” scientists Andrew Brandt and Sean Gallagher stated.
“Only after the target responds to the threat actor’s original email does the danger actor send out a followup message linking to what they declare is specifics about their request or complaint.”
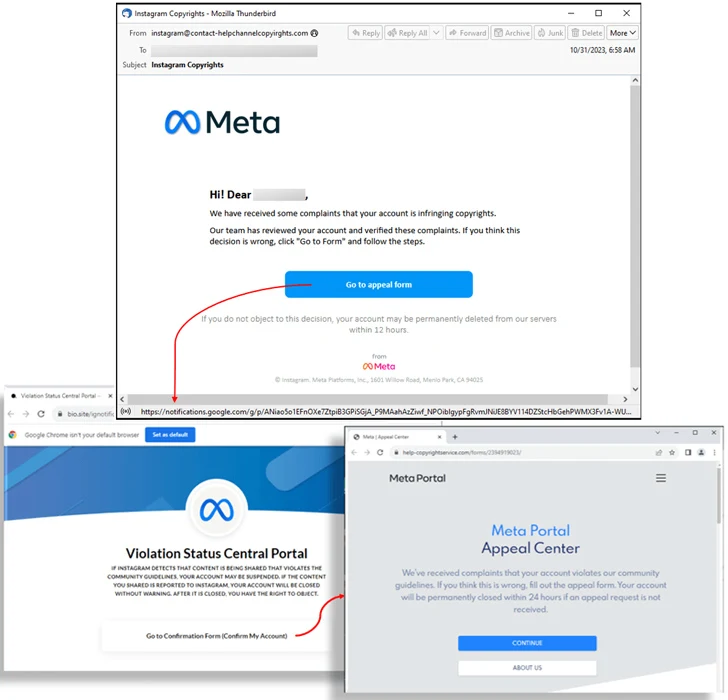
Stealers and trojans notwithstanding, phishing attacks have taken the variety of bogus Instagram “Copyright Infringement” emails to steal users’ two-variable authentication (2FA) backup codes by means of fraudulent web web pages with an intention to bypass account protections, a scheme termed Insta-Phish-A-Gram.
“The data attackers retrieve from this form of phishing attack can be sold underground or made use of to acquire about the account,” the cybersecurity organization stated.
Found this posting interesting? Stick to us on Twitter and LinkedIn to examine far more distinctive articles we submit.
Some parts of this article are sourced from:
thehackernews.com


 Urgent: New Chrome Zero-Day Vulnerability Exploited in the Wild – Update ASAP
Urgent: New Chrome Zero-Day Vulnerability Exploited in the Wild – Update ASAP