Danger actors have been noticed leveraging a legitimate but outdated WordPress plugin to surreptitiously backdoor sites as part of an ongoing marketing campaign, Sucuri revealed in a report posted final week.
The plugin in concern is Eval PHP, unveiled by a developer named flashpixx. It allows consumers to insert PHP code webpages and posts of WordPress internet sites that is then executed each time the posts are opened in a web browser.
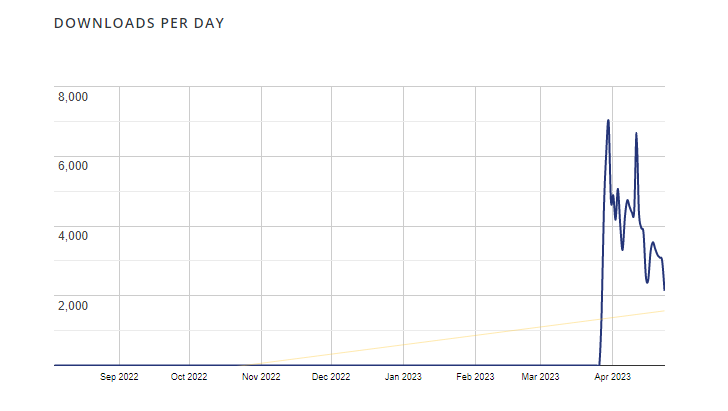
While Eval PHP has never acquired an update in 11 many years, stats collected by WordPress display that it truly is put in on about 8,000 internet websites, with the amount of downloads skyrocketing from a single or two on average considering that September 2022 to 6,988 on March 30, 2023.
On April 23, 2023, on your own, it was downloaded 2,140 periods. The plugin has racked up 23,110 downloads about the earlier seven times.
GoDaddy-owned Sucuri mentioned it observed some infected websites’ databases injected with destructive code into the “wp_posts” table, which retailers a site’s posts, pages, and navigation menu facts. The requests originate from three various IP addresses based in Russia.
“This code is quite easy: It works by using the file_set_contents function to create a PHP script into the docroot of the internet site with the specified distant code execution backdoor,” security researcher Ben Martin said.
“Even though the injection in problem does fall a conventional backdoor into the file composition, the mixture of a genuine plugin and a backdoor dropper in a WordPress post enables them to quickly reinfect the internet site and continue to be hidden. All the attacker desires to do is to go to one particular of the infected posts or web pages and the backdoor will be injected into the file structure.”
Sucuri explained it detected over 6,000 scenarios of this backdoor on compromised internet sites in the very last 6 months, describing the pattern of inserting the malware specifically into the databases as a “new and exciting enhancement.”
Approaching WEBINARZero Rely on + Deception: Find out How to Outsmart Attackers!
Find out how Deception can detect highly developed threats, cease lateral motion, and enhance your Zero Have faith in technique. Be a part of our insightful webinar!
Conserve My Seat!
The attack chain involves installing the Eval PHP plugin on compromised web sites and misusing it to establish persistent backdoors throughout several posts that are occasionally also saved as drafts.
“The way the Eval PHP plugin will work it really is plenty of to preserve a webpage as a draft in buy to execute the PHP code inside the [evalphp] shortcodes,” Martin defined, introducing the rogue web pages are produced with a authentic internet site administrator as their author, suggesting the attackers ended up capable to effectively indicator in as a privileged user.
The development once yet again points to how malicious actors are experimenting with distinctive methods to sustain their foothold in compromised environments and evade server-side scans and file integrity checking.
Web-site house owners are recommended to safe the WP Admin dashboard as well as check out out for any suspicious logins to prevent danger actors from gaining admin entry and install the plugin.
Observed this short article appealing? Adhere to us on Twitter and LinkedIn to browse additional distinctive content material we put up.
Some parts of this article are sourced from:
thehackernews.com


 Learn How a Platform Approach to AppSec Enables You to Shift Everywherecheckmarx.comAppSec / DevOpsCheckmarx One, it's an investment in growth. Drive sales with the most trusted AppSec platform.
Learn How a Platform Approach to AppSec Enables You to Shift Everywherecheckmarx.comAppSec / DevOpsCheckmarx One, it's an investment in growth. Drive sales with the most trusted AppSec platform.